2: Spring Boot Data and Invariants – Project Recommendations
Goal
After completing these projects, you will understand how Spring Boot turns complex enterprise patterns into consistent, testable systems, and why its conventions, defaults, and abstractions exist. You will deeply grasp how Spring Boot wires components, enforces invariants across data and transactions, and provides reliable boundaries for security, configuration, and observability. You will be able to design Spring Boot services that are predictable under load, safe under failure, and maintainable in teams. You will also understand when to lean on Boot defaults and when to override them deliberately.
Why Spring Boot Matters
Spring Boot emerged to tame the complexity of the Spring ecosystem: too many XML files, too much manual configuration, too many ways to wire the same thing. It standardized conventions, offered opinionated defaults, and made production-ready features a first-class concern. Today it powers APIs, microservices, batch systems, and internal platforms across enterprises because it makes the cost of correctness lower. Understanding Spring Boot means understanding the boundaries and invariants of real-world Java systems: configuration, transactions, security, and delivery.
Core ecosystem map:
User -> HTTP -> Spring MVC/WebFlux -> Service -> Data Access -> DB
| | |
| | +-- Transactions
| +-- Business invariants
+-- Security / Filters / Validation
Boot = Auto-config + Conventions + Actuator + Profiles
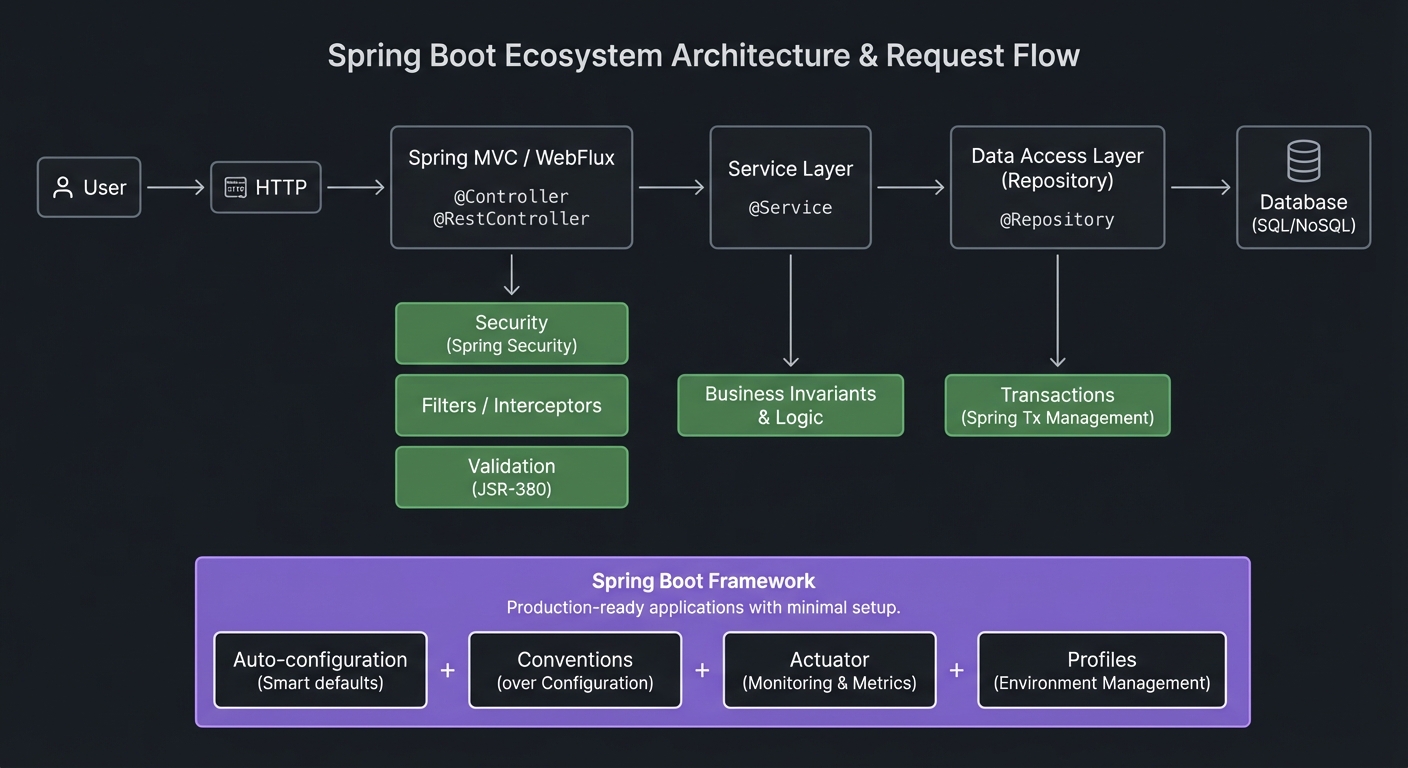
Foundational Concepts: The Five Pillars
1. Dependency Injection and IoC
Spring Boot builds object graphs for you. The invariant is: objects are created and wired once, with clear lifecycle boundaries.
Request
|
v
Controller -> Service -> Repository -> Data Source
^ ^ ^
| | |
Managed by Spring container
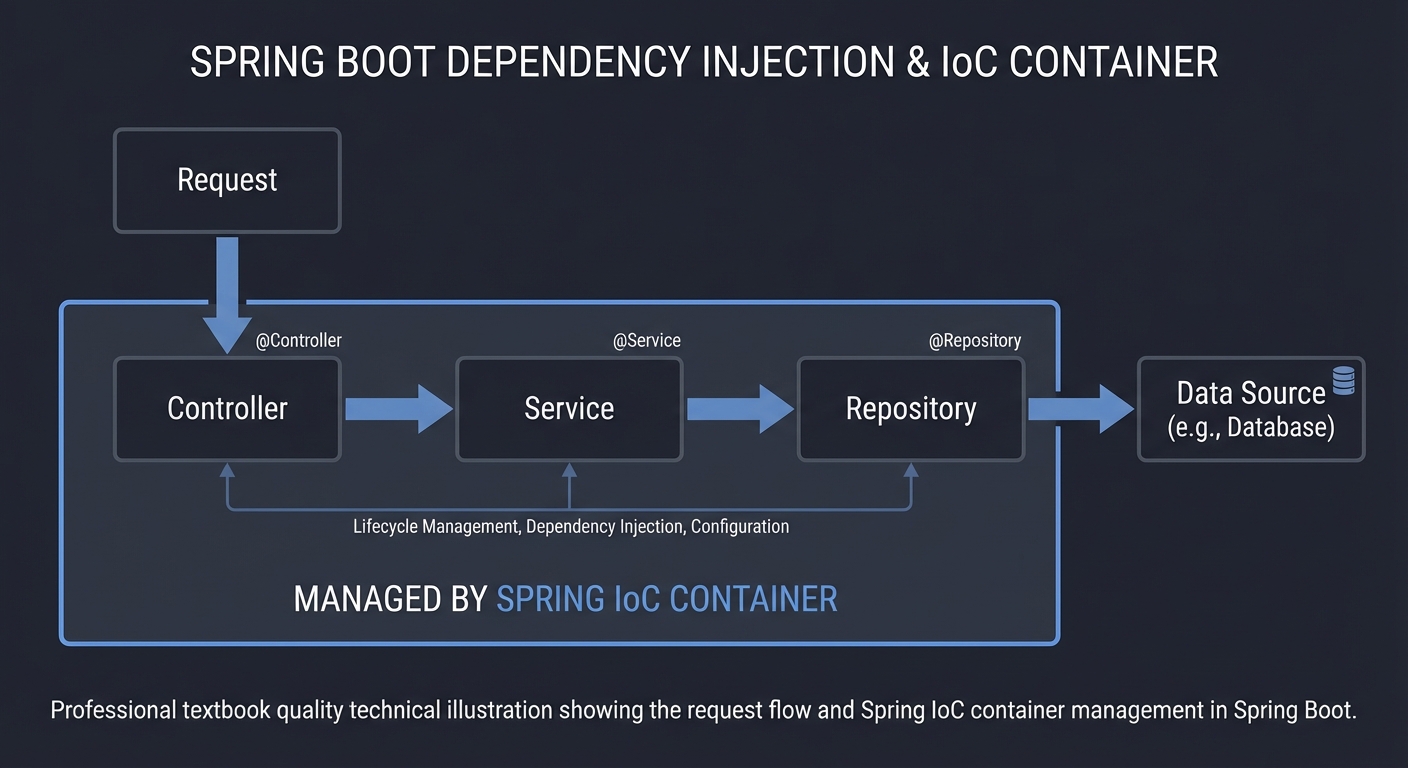
2. Configuration and Profiles
Configuration is a contract: the same code behaves differently based on environment, and those differences are explicit and validated.
application.yml
- defaults
application-dev.yml
- overrides for dev
application-prod.yml
- overrides for prod
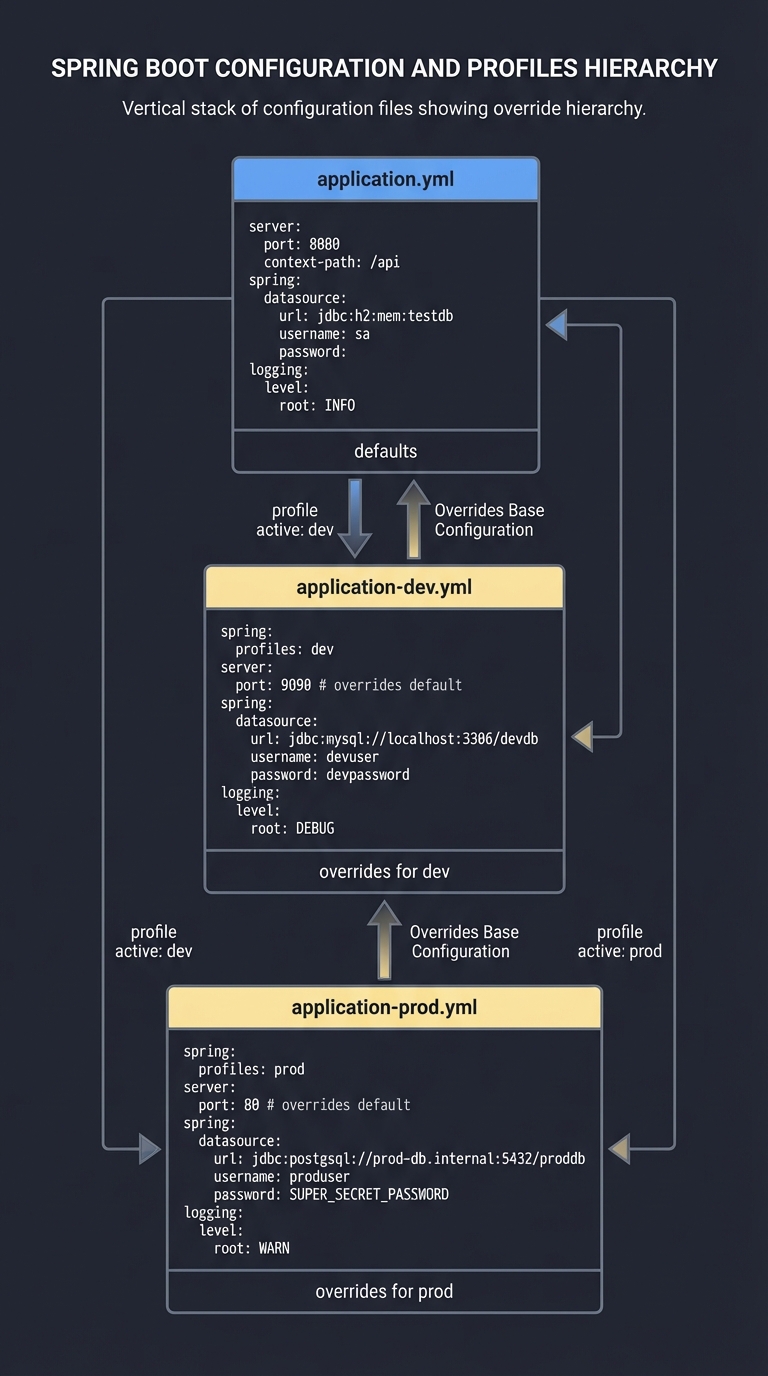
3. Data Invariants and Transactions
Your data has rules. Transactions exist to protect those rules from partial failure.
Order created -> Payment captured -> Inventory reserved
All succeed or all roll back
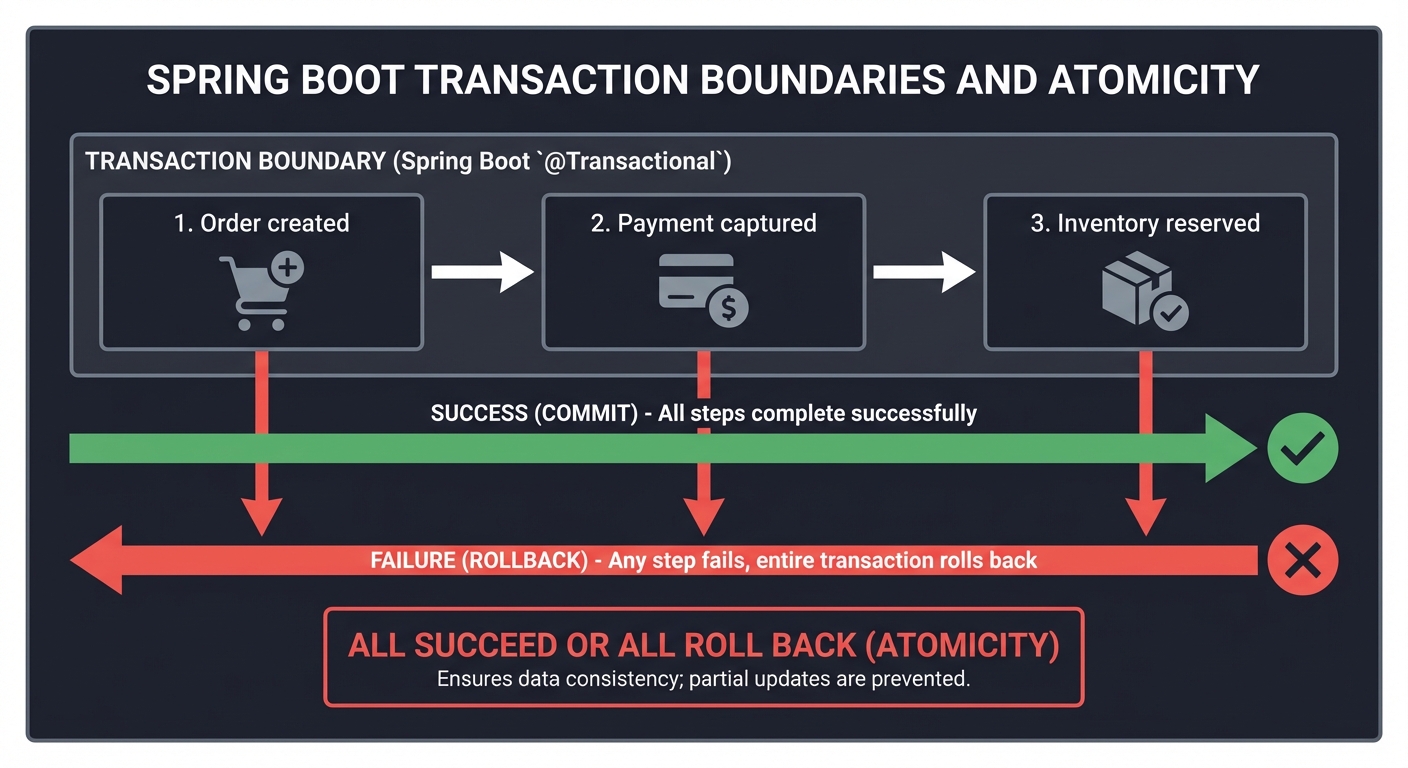
4. Security Boundaries
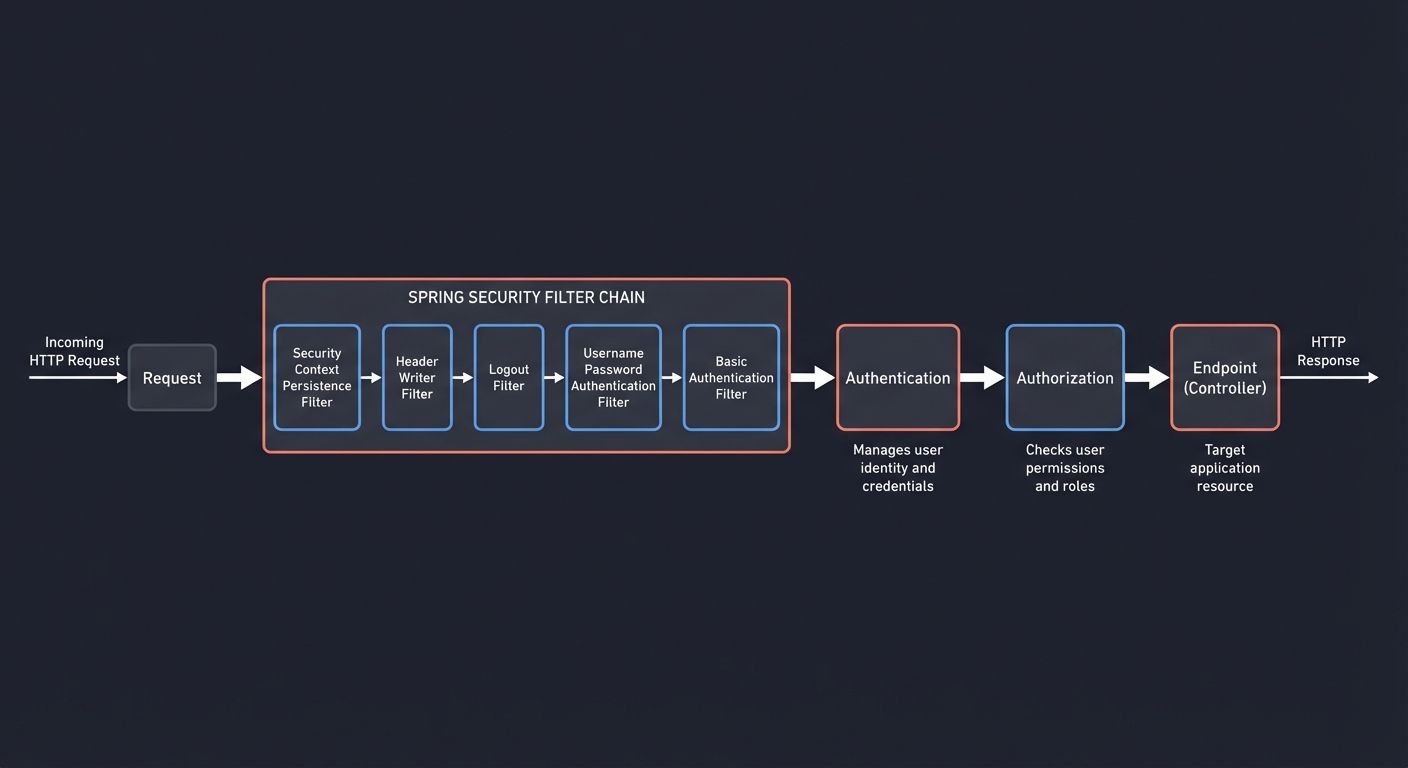
Security is not a feature; it is a boundary of the system. Spring Security enforces identity and authorization as invariants.
Request -> Filter chain -> Authentication -> Authorization -> Endpoint
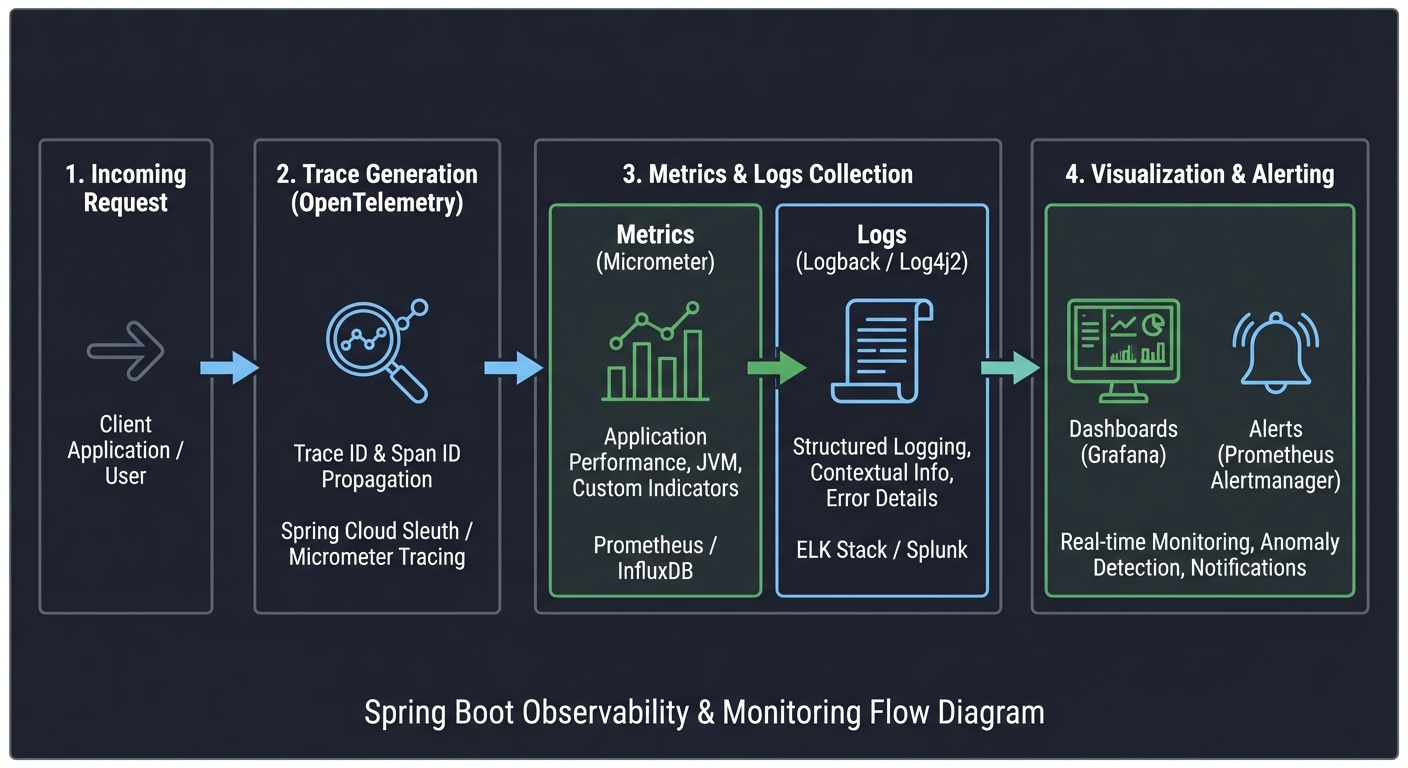
5. Observability and Operations
Spring Boot systems must be observable by default. Metrics, logs, and traces are the operational truth of your system.
Request -> Trace -> Metrics + Logs -> Dashboards + Alerts
Concept Summary Table
| Concept Cluster | What You Need to Internalize |
|---|---|
| IoC and DI | The container owns object creation and lifecycle; you must design for that contract. |
| Configuration | Environments differ; Boot provides a structured, testable way to express those differences. |
| Transactions | Data invariants require atomicity; failures must not leak partial state. |
| Security | Every request must prove identity and authorization before it touches data. |
| Observability | If you cannot measure it, you cannot operate it safely in production. |
Deep Dive Reading by Concept
This section maps each concept from above to specific book chapters for deeper understanding. Read these before or alongside the projects to build strong mental models.
IoC and DI
| Concept | Book and Chapter |
|---|---|
| Dependency injection | Spring in Action by Craig Walls – Ch. 1-2 |
| Component scanning and wiring | Spring Boot: Up and Running by Mark Heckler – Ch. 2 |
Configuration and Profiles
| Concept | Book and Chapter |
|---|---|
| Externalized configuration | Spring Boot: Up and Running by Mark Heckler – Ch. 3 |
| Profiles and environment | Spring in Action by Craig Walls – Ch. 5 |
Transactions and Data
| Concept | Book and Chapter |
|---|---|
| Transaction boundaries | Spring in Action by Craig Walls – Ch. 8 |
| Repository patterns | Spring Data (reference guide) – Repositories section |
Security
| Concept | Book and Chapter |
|---|---|
| Authentication and authorization | Spring Security in Action by Laurentiu Spilca – Ch. 2-4 |
Observability
| Concept | Book and Chapter |
|---|---|
| Metrics and health checks | Cloud Native Java by Josh Long – Observability chapters |
Essential Reading Order
For maximum comprehension, read in this order:
- Foundation (Week 1):
- Spring in Action Ch. 1-2 (IoC and DI)
- Spring Boot: Up and Running Ch. 2-3 (Boot basics and config)
- Data and boundaries (Week 2):
- Spring in Action Ch. 8 (transactions)
- Spring Security in Action Ch. 2-4 (security invariants)
- Operations (Week 3):
- Cloud Native Java observability chapters
Project List
Project 1: “Config-Driven Personal Finance API” — Spring Boot Fundamentals
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | Medium |
| Business Potential | Medium |
| Difficulty | Beginner |
| Knowledge Area | Web APIs |
| Software or Tool | Spring Boot, Spring MVC, Bean Validation |
| Main Book | Spring Boot: Up and Running |
What you’ll build: A REST API that tracks income, expenses, and budgets with strict validation rules enforced by configuration and profiles.
Why it teaches Spring Boot: You will wire controllers, services, and repositories while learning how Boot config and validation enforce consistent behavior across environments.
Core challenges you’ll face:
- Define configuration properties that change per profile (dev, test, prod)
- Enforce invariants like positive amounts and required categories
- Build consistent error responses across endpoints
Key Concepts
- Configuration properties: Spring Boot: Up and Running - Mark Heckler
- Validation and constraints: Spring in Action - Craig Walls
- Request lifecycle: Spring in Action - Craig Walls
Difficulty: Beginner Time estimate: 1-2 weeks Prerequisites: Basic Java, HTTP concepts, and familiarity with JSON; no prior Spring experience required.
Real World Outcome
You will run a local API server that accepts and returns transactions. You will be able to:
- Create an income record and see it persist in a database
- Create an expense record and see validation reject negative amounts
- Switch to a different profile and observe different log levels and database settings
Example Output:
$ curl -X POST http://localhost:8080/transactions
HTTP/1.1 201 Created
{
"id": 101,
"type": "expense",
"amount": 42.50,
"category": "groceries",
"createdAt": "2025-02-01T10:15:00Z"
}
The Core Question You’re Answering
“How does Spring Boot make configuration and validation enforce the rules of my domain?”
Before you write any code, sit with this question. Boot is not magic; it is a disciplined way to express rules in configuration and enforce them consistently. This project forces you to see those rules in action across environments.
Concepts You Must Understand First
Stop and research these before coding:
- Externalized configuration
- What is the difference between default properties and profile overrides?
- How does Boot choose which config files are active?
- Book Reference: “Spring Boot: Up and Running” Ch. 3 - Mark Heckler
- Validation constraints
- What is the difference between validation at the API boundary and validation in the service layer?
- Why must invariants be enforced in more than one place?
- Book Reference: “Spring in Action” Ch. 5 - Craig Walls
Questions to Guide Your Design
Before implementing, think through these:
- API boundaries
- Which fields should be required, and why?
- How will you respond when input violates invariants?
- Configuration strategy
- Which settings must vary by environment?
- How will you document those settings for future maintainers?
Thinking Exercise
Configuration Flow Map
Before coding, map out how configuration should flow:
Request -> Controller -> Service -> Repository
| | |
| | +-- Reads config values
+-- Validation happens here
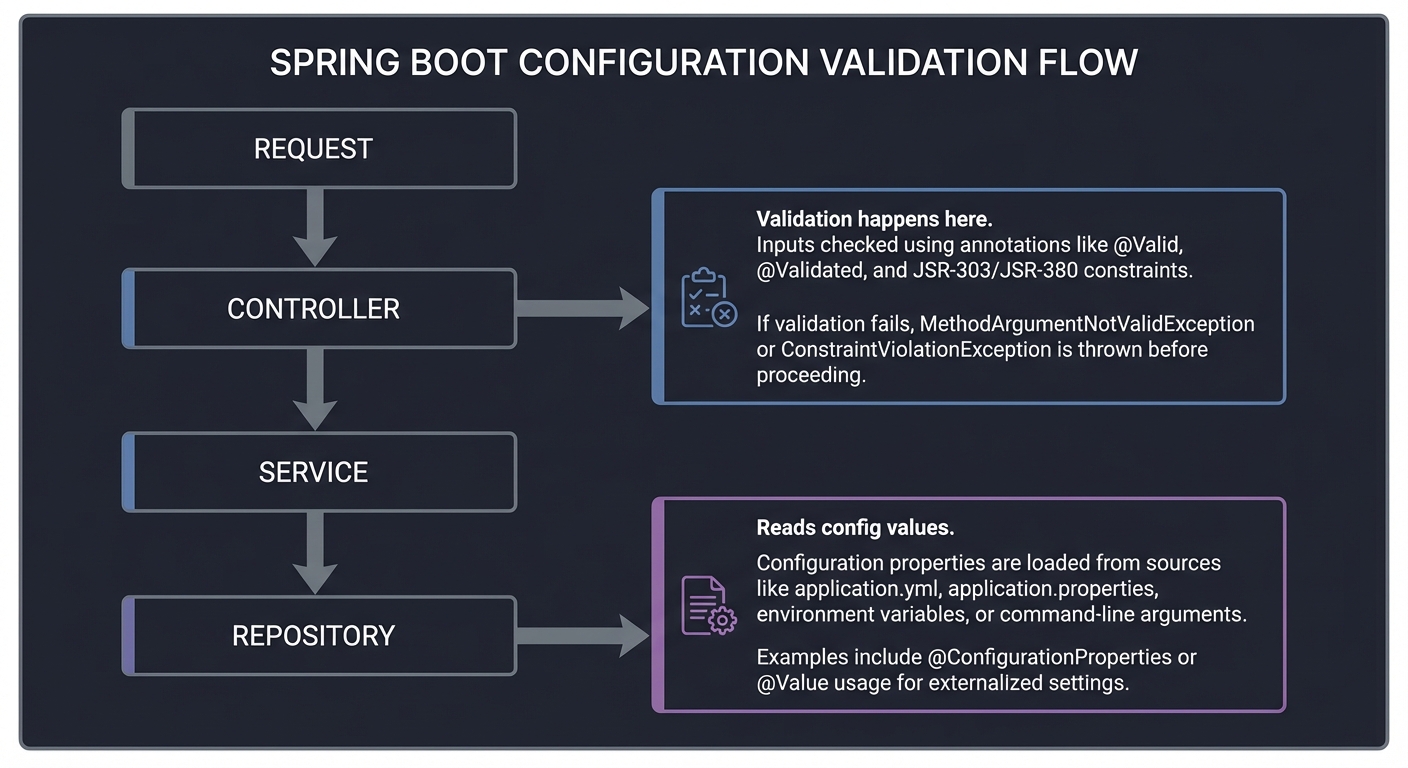
Questions while diagramming:
- Where must invariants be enforced so they cannot be bypassed?
- Which layer should know about environment-specific settings?
- What happens if a required config value is missing?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What is the difference between @ConfigurationProperties and @Value?”
- “Where should validation happen in a Spring Boot app?”
- “How do profiles change application behavior?”
- “How do you structure error responses consistently?”
- “Why is validation a data invariant rather than just input checking?”
Hints in Layers
Hint 1: Starting Point List the domain rules first (amount must be positive, category required, etc.).
Hint 2: Next Level Decide which rules belong at the API boundary and which belong in the service layer.
Hint 3: Technical Details Use configuration properties to declare environment-specific values and validate them at startup.
Hint 4: Tools/Debugging Use Actuator to verify active profiles and inspect configuration properties.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Boot configuration | “Spring Boot: Up and Running” by Mark Heckler | Ch. 3 |
| Validation | “Spring in Action” by Craig Walls | Ch. 5 |
Project 2: “Order Service with Transactional Invariants” — Data Consistency
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | High |
| Business Potential | High |
| Difficulty | Intermediate |
| Knowledge Area | Data and Transactions |
| Software or Tool | Spring Data JPA, Spring Boot |
| Main Book | Spring in Action |
What you’ll build: A service that creates orders, reserves inventory, and records payments with strict transactional guarantees.
Why it teaches Spring Boot: You will learn how Boot and Spring Data manage transactions and enforce data invariants across multiple tables.
Core challenges you’ll face:
- Define transactional boundaries for multi-step workflows
- Prevent partial updates when failures occur
- Model invariant rules like “inventory cannot go negative”
Key Concepts
- Transaction management: Spring in Action - Craig Walls
- Repository abstractions: Spring Data reference guide
- Domain modeling: Domain-Driven Design - Eric Evans
Difficulty: Intermediate Time estimate: 1-2 weeks Prerequisites: Basic Spring Boot project setup and REST API knowledge.
Real World Outcome
You will be able to place orders that either fully succeed or fully fail. You will verify that:
- Successful orders show inventory reduced and payment recorded
- Failed orders leave inventory untouched and no payment records
- Transaction logs show clear commit or rollback boundaries
Example Output:
$ curl -X POST http://localhost:8080/orders
HTTP/1.1 201 Created
{
"orderId": 2201,
"status": "CONFIRMED",
"itemsReserved": 3,
"paymentStatus": "CAPTURED"
}
The Core Question You’re Answering
“How do transactions protect business invariants from partial failure?”
Before you write any code, sit with this question. The key insight is that correctness is about system-wide invariants, not just single method success.
Concepts You Must Understand First
Stop and research these before coding:
- Transactional boundaries
- What is the difference between atomicity and isolation?
- Why do partial writes break invariants?
- Book Reference: “Spring in Action” Ch. 8 - Craig Walls
- Repository abstraction
- What does Spring Data generate for you?
- When should you write custom queries?
- Book Reference: “Spring Data” reference guide – Repositories
Questions to Guide Your Design
Before implementing, think through these:
- Data model
- Where do you store order state transitions?
- How do you represent reserved inventory?
- Failure handling
- What happens if payment fails after inventory is reserved?
- How will you prove rollback worked?
Thinking Exercise
Transaction Boundary Sketch
Before coding, sketch the sequence:
Create order -> Reserve inventory -> Capture payment -> Commit
Failure at any step -> Rollback all state
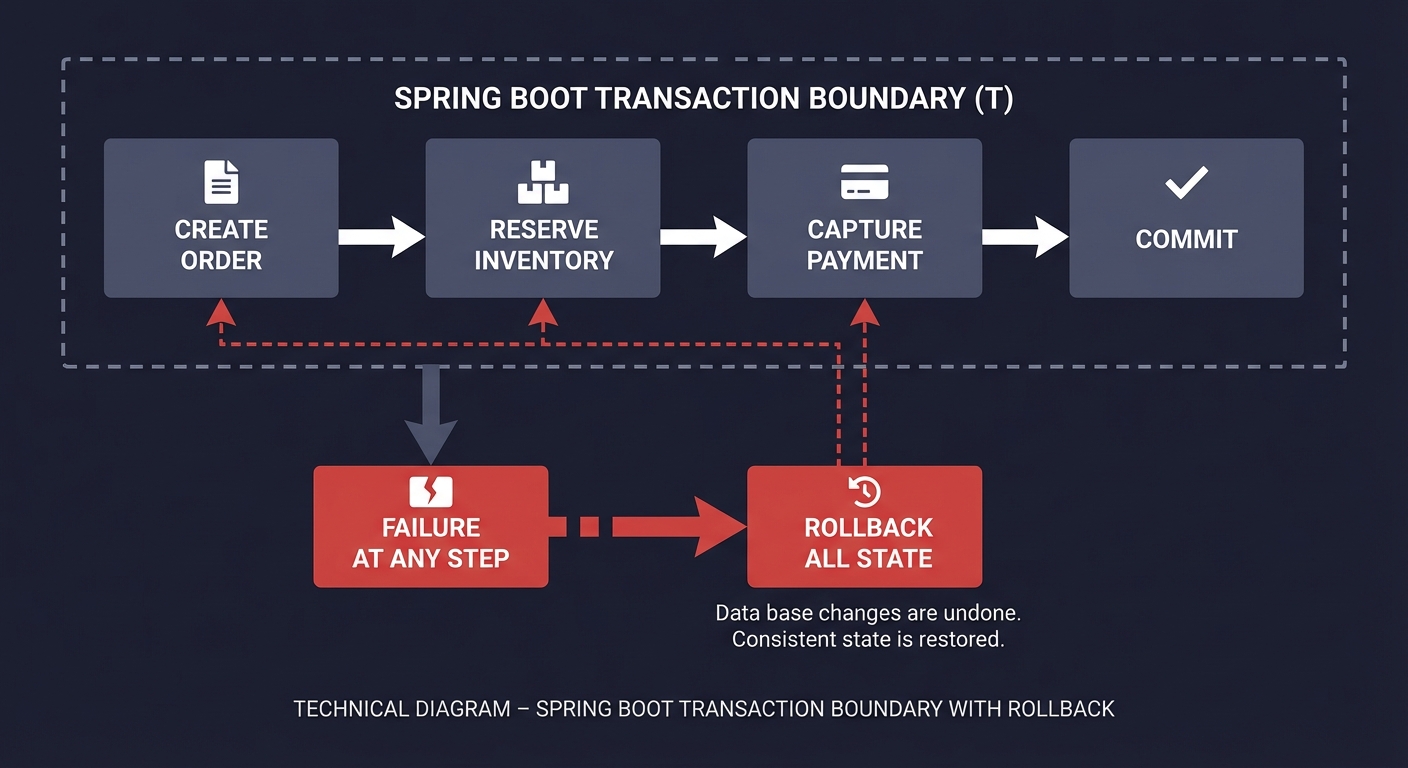
Questions while diagramming:
- Where is the single boundary that must wrap all steps?
- How will you verify rollback occurred?
- Which invariants are violated if rollback is missing?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What does @Transactional guarantee and what does it not?”
- “How do you handle transaction boundaries across service calls?”
- “What isolation level would you use for inventory updates?”
- “What is the difference between optimistic and pessimistic locking?”
- “How do you test transactional rollbacks?”
Hints in Layers
Hint 1: Starting Point List the invariants and map them to tables and states.
Hint 2: Next Level Decide which service methods must be wrapped in one transaction.
Hint 3: Technical Details Use transactional annotations to define atomic boundaries and verify with logs.
Hint 4: Tools/Debugging Enable SQL logging and inspect commit or rollback markers.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Transactions | “Spring in Action” by Craig Walls | Ch. 8 |
| Domain modeling | “Domain-Driven Design” by Eric Evans | Part I |
Project 3: “Secure Account Management Service” — Authentication and Authorization
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | High |
| Business Potential | High |
| Difficulty | Intermediate |
| Knowledge Area | Security |
| Software or Tool | Spring Security |
| Main Book | Spring Security in Action |
What you’ll build: A secure account service with login, role-based access, and audited profile changes.
Why it teaches Spring Boot: You will learn how Spring Security enforces authentication and authorization invariants across every request.
Core challenges you’ll face:
- Build a filter chain that protects endpoints consistently
- Enforce role-based rules that cannot be bypassed
- Capture audit trails for sensitive actions
Key Concepts
- Filter chains: Spring Security in Action - Laurentiu Spilca
- Authorization rules: Spring Security in Action - Laurentiu Spilca
- Security testing: Spring in Action - Craig Walls
Difficulty: Intermediate Time estimate: 1-2 weeks Prerequisites: Basic Spring Boot REST knowledge and understanding of authentication concepts.
Real World Outcome
You will authenticate with a login flow and then access protected endpoints. You will be able to:
- Log in as a regular user and see only your own profile
- Log in as an admin and see full account management endpoints
- Trigger audit records whenever profiles are updated
Example Output:
$ curl -H "Authorization: Bearer <token>" http://localhost:8080/profile
HTTP/1.1 200 OK
{
"username": "douglas",
"roles": ["USER"],
"lastUpdatedBy": "douglas"
}
The Core Question You’re Answering
“How does Spring Security enforce identity and authorization as system invariants?”
Before you write any code, sit with this question. Security is not a feature you add later; it is a boundary that must be enforced on every request.
Concepts You Must Understand First
Stop and research these before coding:
- Authentication vs authorization
- What is the difference between identity and permission?
- Where should authorization decisions be enforced?
- Book Reference: “Spring Security in Action” Ch. 2 - Laurentiu Spilca
- Filter chain model
- What is the order of security filters?
- Why does ordering matter for correctness?
- Book Reference: “Spring Security in Action” Ch. 3 - Laurentiu Spilca
Questions to Guide Your Design
Before implementing, think through these:
- Security boundaries
- Which endpoints must be protected and why?
- What happens if an unauthenticated request reaches a controller?
- Audit trail
- What security-sensitive actions must be recorded?
- Who should be able to view audit records?
Thinking Exercise
Filter Chain Sketch
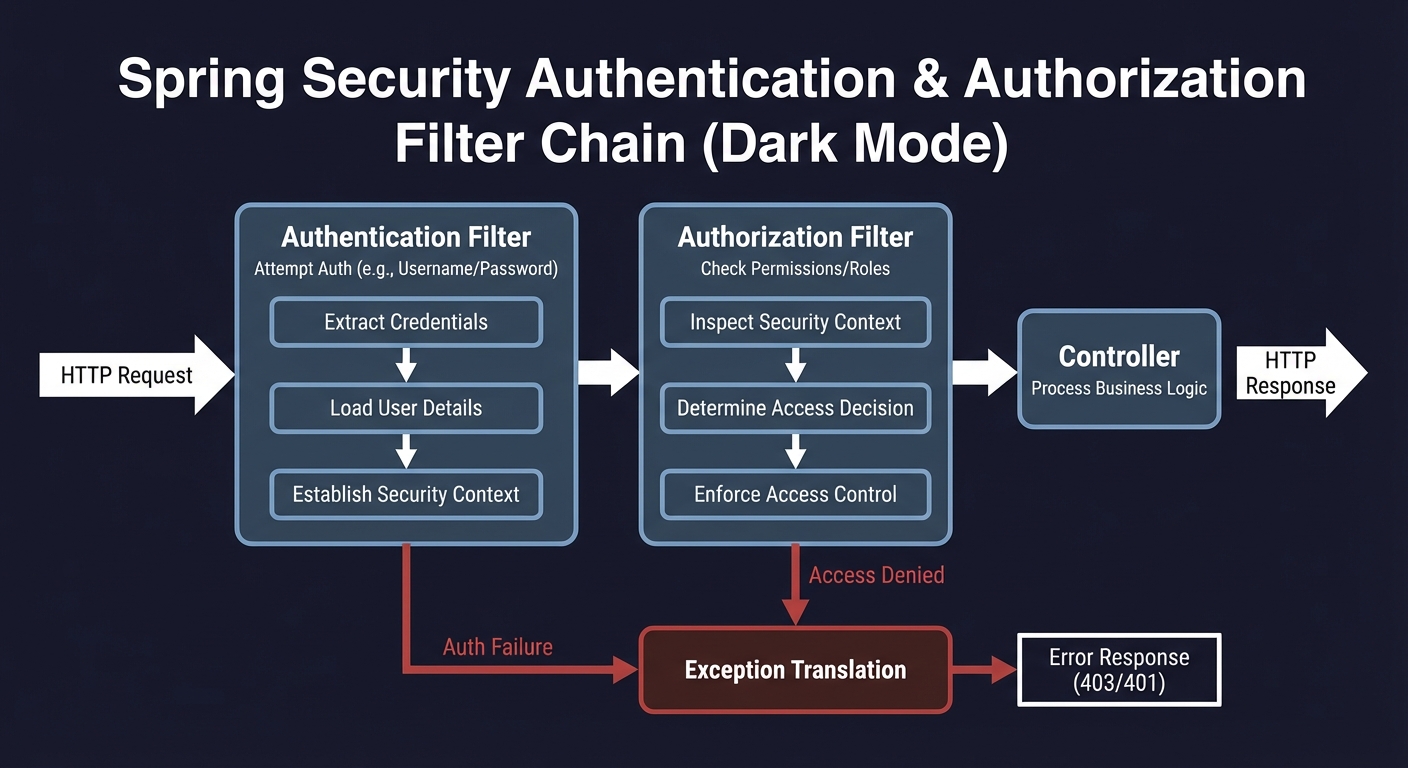
Before coding, sketch the filter chain:
Request -> Authentication filter -> Authorization filter -> Controller
Questions while diagramming:
- Where does identity get established?
- Where is authorization checked?
- How do you ensure audit logging happens after authorization?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What is the difference between authentication and authorization?”
- “How does Spring Security integrate with Spring Boot?”
- “How do you apply method-level security?”
- “How do you secure endpoints differently by role?”
- “How do you test security rules?”
Hints in Layers
Hint 1: Starting Point List all endpoints and classify them as public, user-only, or admin-only.
Hint 2: Next Level Map each role to an authorization rule and make sure defaults are deny-all.
Hint 3: Technical Details Use a clear authentication mechanism and enforce authorization consistently in filters or annotations.
Hint 4: Tools/Debugging Turn on security debug logs to trace filter decisions.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Security basics | “Spring Security in Action” by Laurentiu Spilca | Ch. 2-4 |
| Testing security | “Spring in Action” by Craig Walls | Ch. 10 |
Project 4: “Event-Driven Inventory Updates” — Messaging and Idempotency
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | High |
| Business Potential | High |
| Difficulty | Advanced |
| Knowledge Area | Messaging |
| Software or Tool | Spring Cloud Stream |
| Main Book | Cloud Native Java |
What you’ll build: A service that updates inventory in response to events from an order system.
Why it teaches Spring Boot: You will learn how Boot integrates with messaging systems and how event-driven design maintains data invariants across services.
Core challenges you’ll face:
- Define event schemas and validate them
- Guarantee idempotency to prevent double-decrement of inventory
- Trace event flow across services
Key Concepts
- Messaging patterns: Cloud Native Java - Josh Long
- Idempotency: Designing Data-Intensive Applications - Martin Kleppmann
- Event-driven systems: Building Microservices - Sam Newman
Difficulty: Advanced Time estimate: 1 month+ Prerequisites: Comfort with Spring Boot REST APIs and database transactions.
Real World Outcome
You will publish an order event and observe inventory updates asynchronously. You will be able to:
- Send an order event and see inventory change in the inventory service
- Re-send the same event and verify inventory does not change twice
- Inspect logs that show event processing and acknowledgments
Example Output:
$ curl -X POST http://localhost:8081/events
HTTP/1.1 202 Accepted
{
"eventId": "evt-9001",
"type": "ORDER_CONFIRMED",
"status": "QUEUED"
}
The Core Question You’re Answering
“How do distributed events preserve data invariants without shared transactions?”
Before you write any code, sit with this question. Event-driven systems remove shared transactions, so you must design for consistency through messages.
Concepts You Must Understand First
Stop and research these before coding:
- Event schemas
- What is the minimum information needed to update inventory?
- How do you version events safely?
- Book Reference: “Building Microservices” Ch. 4 - Sam Newman
- Idempotency
- Why must event handlers be safe to run twice?
- What happens if messages are delivered out of order?
- Book Reference: “Designing Data-Intensive Applications” Ch. 11 - Martin Kleppmann
Questions to Guide Your Design
Before implementing, think through these:
- Consistency model
- Which invariants must be strong and which can be eventual?
- How do you reconcile when updates arrive late?
- Failure handling
- What happens if processing fails after inventory is updated?
- How will you reprocess safely?
Thinking Exercise
Event Flow Sketch
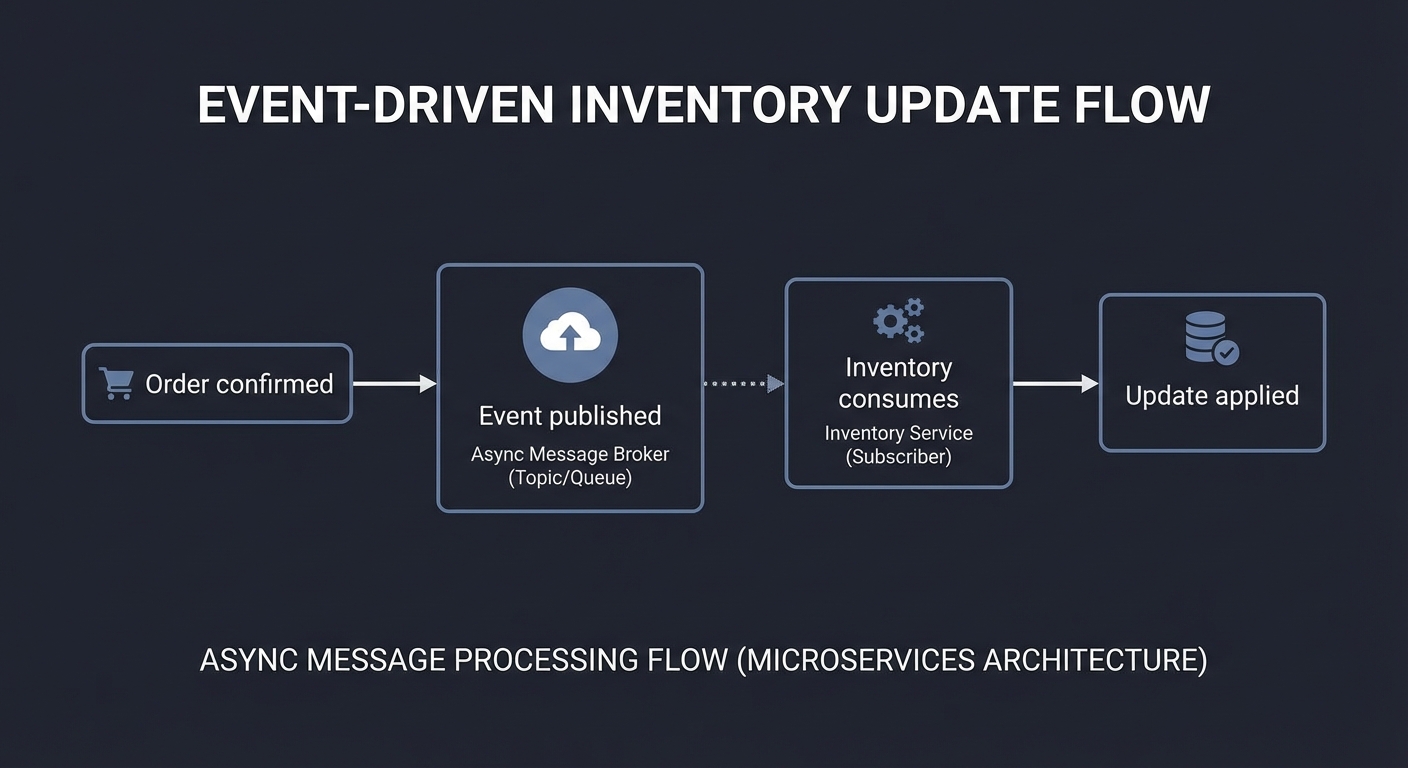
Before coding, diagram the flow:
Order confirmed -> Event published -> Inventory consumes -> Update applied
Questions while diagramming:
- Where do you enforce idempotency?
- How do you verify the event was processed exactly once?
- Which logs prove that the invariant holds?
The Interview Questions They’ll Ask
Prepare to answer these:
- “How do you design idempotent event handlers?”
- “What consistency guarantees does messaging provide?”
- “How do you handle event versioning?”
- “How do you trace messages across services?”
- “What does eventual consistency mean in practice?”
Hints in Layers
Hint 1: Starting Point Define the event schema and the invariant it must preserve.
Hint 2: Next Level Store processed event IDs to guard against duplicates.
Hint 3: Technical Details Use message acknowledgments and a dead-letter strategy to handle failures.
Hint 4: Tools/Debugging Instrument logs with event IDs so you can trace retries.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Event-driven design | “Building Microservices” by Sam Newman | Ch. 4 |
| Idempotency | “Designing Data-Intensive Applications” by Martin Kleppmann | Ch. 11 |
Project 5: “Resilient External API Client” — Circuit Breakers and Retries
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | Medium |
| Business Potential | High |
| Difficulty | Intermediate |
| Knowledge Area | Resilience |
| Software or Tool | Spring Boot, Resilience4j |
| Main Book | Release It! |
What you’ll build: A service that consumes a flaky external API with retries, timeouts, and circuit breakers.
Why it teaches Spring Boot: You will learn how Boot integrates resilience patterns and how these patterns enforce runtime invariants like latency and availability.
Core challenges you’ll face:
- Define timeouts and retries that do not overload upstream services
- Use circuit breakers to prevent cascading failure
- Capture metrics about failure rates
Key Concepts
- Circuit breakers: Release It! - Michael T. Nygard
- Retry strategies: Release It! - Michael T. Nygard
- Observability: Cloud Native Java - Josh Long
Difficulty: Intermediate Time estimate: 1-2 weeks Prerequisites: Basic Spring Boot REST and HTTP client understanding.
Real World Outcome
You will call an external API endpoint and see resilience patterns in action. You will be able to:
- Simulate upstream failure and watch the circuit breaker open
- Observe retries in logs with backoff timing
- See metrics show error rates and circuit state
Example Output:
$ curl http://localhost:8080/external-data
HTTP/1.1 503 Service Unavailable
{
"status": "CIRCUIT_OPEN",
"message": "Fallback response used"
}
The Core Question You’re Answering
“How do resilience patterns enforce runtime invariants like latency and availability?”
Before you write any code, sit with this question. In production, your system must fail safely without dragging everything down.
Concepts You Must Understand First
Stop and research these before coding:
- Timeouts and retries
- Why can retries amplify failures?
- How do you choose a safe retry budget?
- Book Reference: “Release It!” Ch. 4 - Michael T. Nygard
- Circuit breakers
- What is the difference between open, closed, and half-open states?
- How does a circuit breaker protect invariants?
- Book Reference: “Release It!” Ch. 5 - Michael T. Nygard
Questions to Guide Your Design
Before implementing, think through these:
- Failure strategy
- What is your fallback when the upstream is down?
- How will you communicate degraded results to clients?
- Metrics and alerts
- Which metrics prove resilience is working?
- How will you detect retry storms?
Thinking Exercise
Failure Timeline
Before coding, map the timeline of a failed call:
Call -> Timeout -> Retry -> Circuit opens -> Fallback response
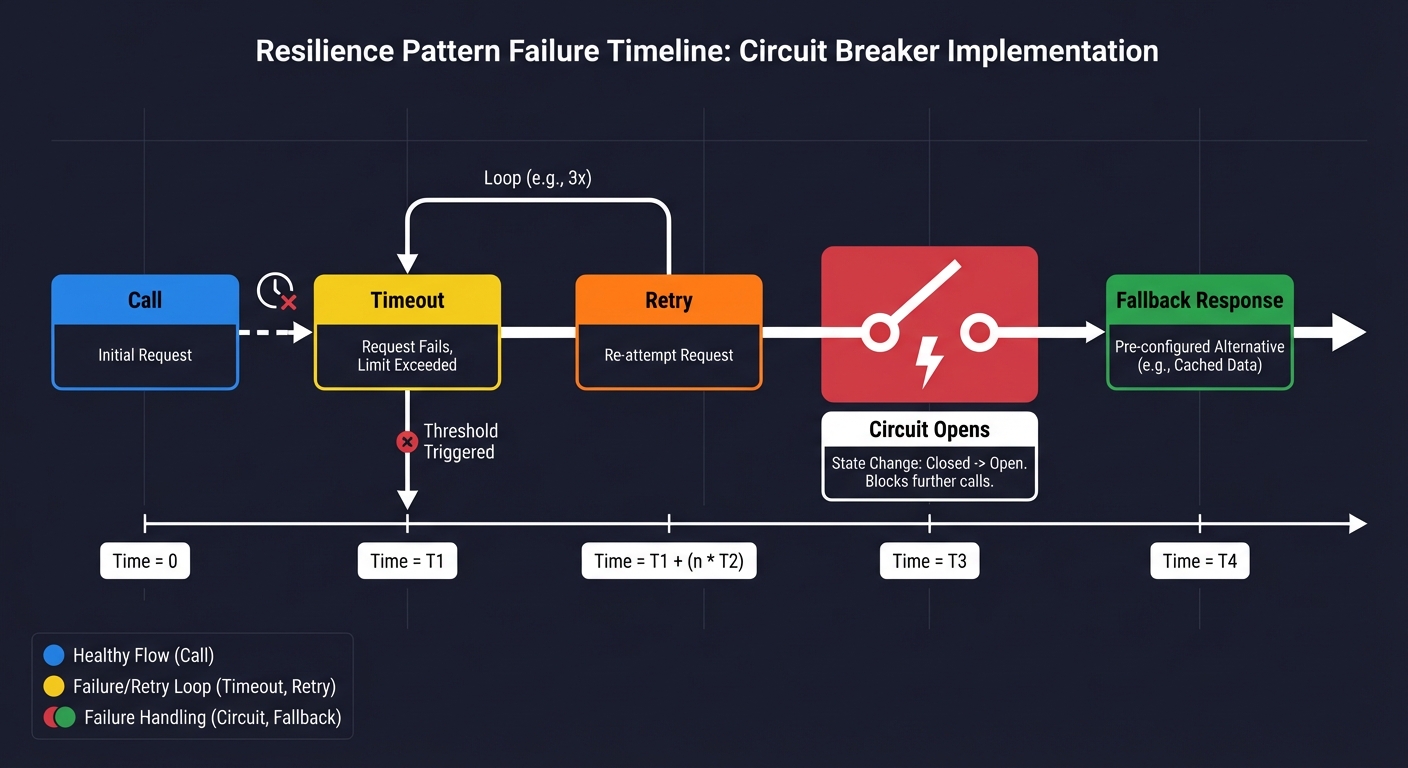
Questions while diagramming:
- At what point should the circuit open?
- What is the maximum acceptable latency?
- How do you prevent infinite retries?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What is a circuit breaker and why is it important?”
- “How do you choose retry and timeout values?”
- “How do you integrate resilience patterns in Spring Boot?”
- “What is the difference between fallback and retry?”
- “How do you monitor resilience in production?”
Hints in Layers
Hint 1: Starting Point Define acceptable latency and failure rates first.
Hint 2: Next Level Choose retry and timeout values that respect that budget.
Hint 3: Technical Details Configure circuit breakers and record state transitions in logs.
Hint 4: Tools/Debugging Use metrics to visualize circuit breaker states.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Resilience patterns | “Release It!” by Michael T. Nygard | Ch. 4-5 |
| Observability | “Cloud Native Java” by Josh Long | Observability sections |
Project 6: “Observability-First Service” — Metrics, Health, and Tracing
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | Medium |
| Business Potential | Medium |
| Difficulty | Intermediate |
| Knowledge Area | Observability |
| Software or Tool | Spring Boot Actuator, Micrometer |
| Main Book | Cloud Native Java |
What you’ll build: A service instrumented with metrics, health checks, and traces that reveal system behavior.
Why it teaches Spring Boot: You will learn how Boot exposes operational data and why observability is part of the system contract.
Core challenges you’ll face:
- Define meaningful metrics that represent user outcomes
- Configure health checks that reflect dependency status
- Correlate logs and traces across requests
Key Concepts
- Actuator endpoints: Cloud Native Java - Josh Long
- Metrics design: Designing Data-Intensive Applications - Martin Kleppmann
- Health checks: Site Reliability Engineering - Betsy Beyer et al.
Difficulty: Intermediate Time estimate: 1-2 weeks Prerequisites: Comfort with Spring Boot REST and basic logging.
Real World Outcome
You will open a dashboard showing live metrics and health status. You will be able to:
- View uptime, request latency, and error rates
- Hit a health endpoint and see dependency status
- Trace a request end-to-end through logs and metrics
Example Output:
$ curl http://localhost:8080/actuator/health
HTTP/1.1 200 OK
{
"status": "UP",
"components": {
"db": { "status": "UP" },
"diskSpace": { "status": "UP" }
}
}
The Core Question You’re Answering
“How do I make system behavior visible and testable in production?”
Before you write any code, sit with this question. Observability is how you prove your system is healthy and trustworthy.
Concepts You Must Understand First
Stop and research these before coding:
- Metrics vs logs vs traces
- What question does each telemetry type answer?
- How do you correlate them?
- Book Reference: “Site Reliability Engineering” Ch. 6 - Betsy Beyer et al.
- Health checks
- What should be included in a readiness check?
- What should be excluded to avoid false positives?
- Book Reference: “Cloud Native Java” observability sections
Questions to Guide Your Design
Before implementing, think through these:
- Metric strategy
- Which metrics show user impact, not just system load?
- How will you aggregate them?
- Operational invariants
- What conditions must be true before the service is considered healthy?
- How will you signal degraded mode?
Thinking Exercise
Telemetry Map
Before coding, map the telemetry you want:
Request -> Log entry + Trace id + Metric increment
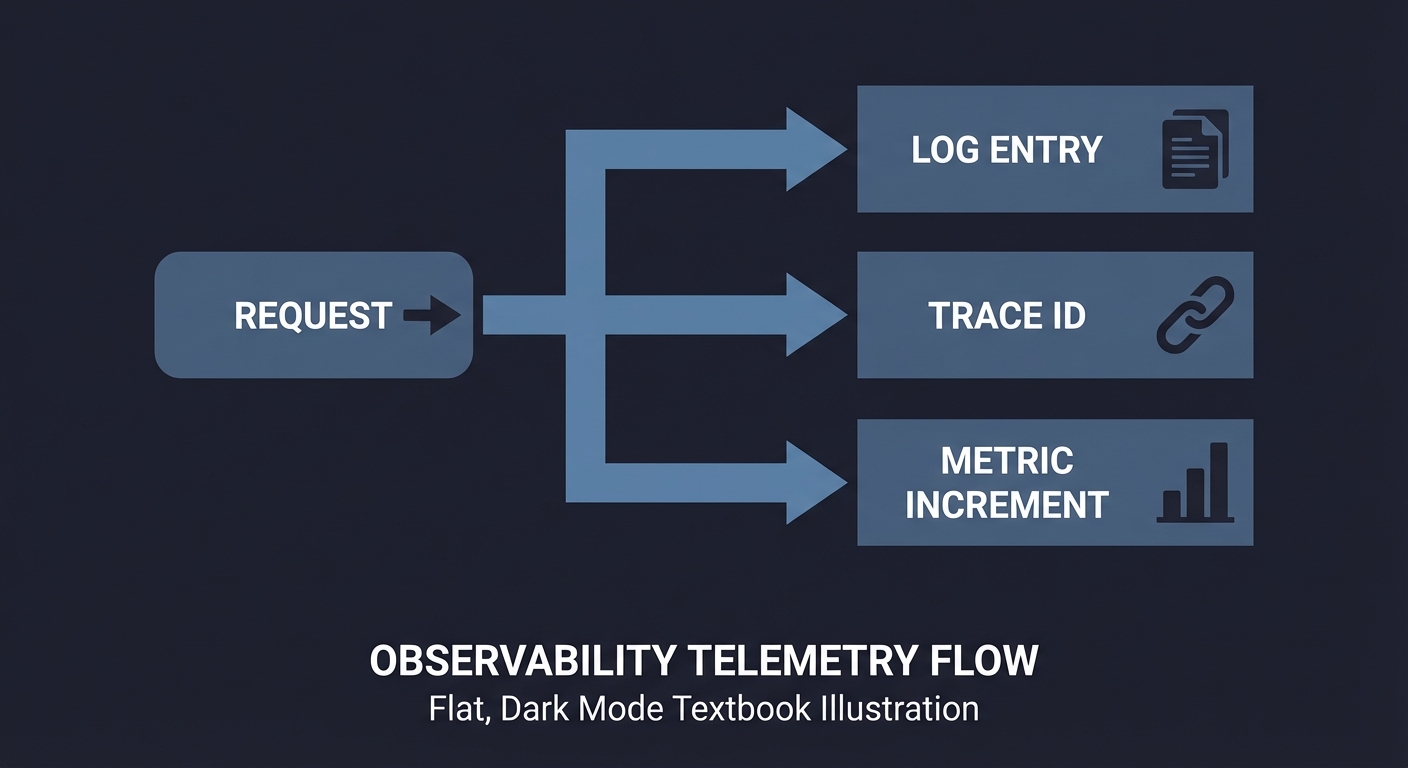
Questions while diagramming:
- Which fields correlate logs with traces?
- What metric proves success for a user action?
- How will you detect an unhealthy dependency?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What is the difference between readiness and liveness checks?”
- “How do you design meaningful metrics?”
- “How do you use Actuator safely in production?”
- “How do you correlate logs and traces?”
- “What telemetry would you add first to a new service?”
Hints in Layers
Hint 1: Starting Point List the user journeys and define success metrics for each.
Hint 2: Next Level Expose health indicators for every dependency.
Hint 3: Technical Details Configure metrics tags that identify endpoints and outcomes.
Hint 4: Tools/Debugging Use the Actuator endpoints to verify metrics and health outputs.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Observability | “Cloud Native Java” by Josh Long | Observability sections |
| SRE practices | “Site Reliability Engineering” by Betsy Beyer et al. | Ch. 6 |
Project 7: “Batch Data Pipeline with Spring Batch” — Chunk Processing and Restarts
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | Medium |
| Business Potential | Medium |
| Difficulty | Intermediate |
| Knowledge Area | Batch Processing |
| Software or Tool | Spring Batch |
| Main Book | Spring Batch in Action |
What you’ll build: A batch pipeline that imports CSV transactions, cleans data, and writes normalized records to a database.
Why it teaches Spring Boot: You will learn the batch processing model, job steps, and how invariants apply to offline processing.
Core challenges you’ll face:
- Define job steps and chunk sizes
- Handle invalid records without corrupting the job
- Track job state and restart safely
Key Concepts
- Batch job design: Spring Batch in Action - Michael Minella
- Data validation: Spring in Action - Craig Walls
- Restartability: Spring Batch in Action - Michael Minella
Difficulty: Intermediate Time estimate: 1-2 weeks Prerequisites: Basic Spring Boot and familiarity with CSV data.
Real World Outcome
You will run a batch job and see a detailed job report. You will be able to:
- Import a CSV file and see normalized records written to the database
- See skipped records for invalid rows
- Restart a failed job without duplicating data
Example Output:
$ java -jar batch-job.jar
Job: importTransactions
Status: COMPLETED
Read: 1200, Written: 1185, Skipped: 15
The Core Question You’re Answering
“How do I enforce data quality invariants in offline pipelines?”
Before you write any code, sit with this question. Batch systems must keep data trustworthy even when processing large volumes.
Concepts You Must Understand First
Stop and research these before coding:
- Chunk processing
- Why does chunk size affect correctness and performance?
- How do you recover from failures mid-chunk?
- Book Reference: “Spring Batch in Action” Ch. 4 - Michael Minella
- Job state
- How does Spring Batch track job execution?
- Why must job state be persistent?
- Book Reference: “Spring Batch in Action” Ch. 6 - Michael Minella
Questions to Guide Your Design
Before implementing, think through these:
- Data validation
- Which records must be rejected and why?
- How will you report data quality issues?
- Restart strategy
- What is the safe restart point after failure?
- How will you avoid duplicate writes?
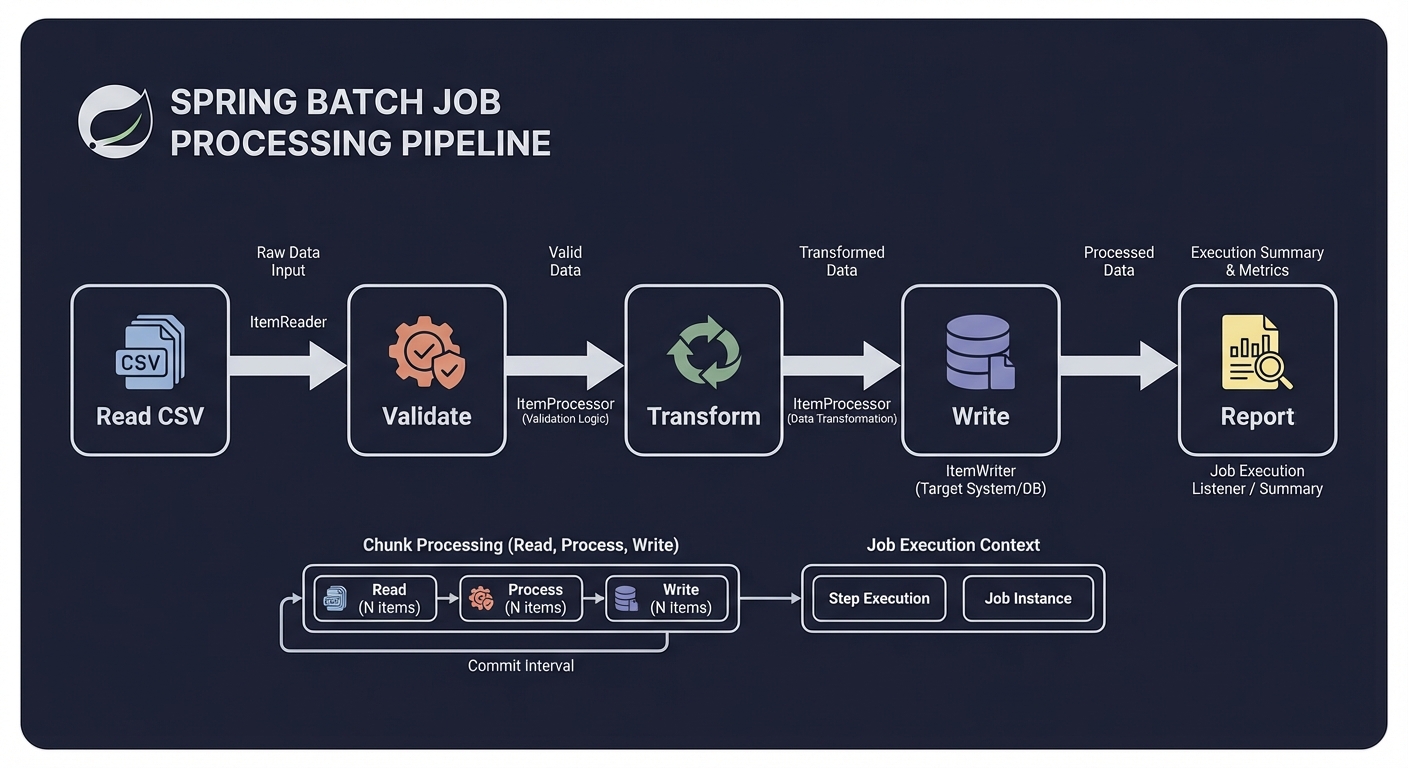
Thinking Exercise
Batch Step Flow
Before coding, diagram your steps:
Read CSV -> Validate -> Transform -> Write -> Report
Questions while diagramming:
- Which step enforces the strongest invariants?
- Where should invalid data be quarantined?
- How do you know if a job can be restarted?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What is a job repository in Spring Batch?”
- “How do you handle failures in batch jobs?”
- “What is chunk processing and why does it matter?”
- “How do you make batch jobs restartable?”
- “How do you track data quality issues in batch processing?”
Hints in Layers
Hint 1: Starting Point Define the data invariants for each field in the CSV.
Hint 2: Next Level Design steps around validation and transformation before writing.
Hint 3: Technical Details Store job execution metadata and validate restart behavior.
Hint 4: Tools/Debugging Use job logs and job repository tables to confirm status.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Spring Batch basics | “Spring Batch in Action” by Michael Minella | Ch. 4-6 |
| Validation | “Spring in Action” by Craig Walls | Ch. 5 |
Project 8: “Reactive Event Feed Service” — Backpressure and Non-Blocking IO
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | High |
| Business Potential | Medium |
| Difficulty | Advanced |
| Knowledge Area | Reactive Systems |
| Software or Tool | Spring WebFlux |
| Main Book | Reactive Spring |
What you’ll build: A reactive service that streams live updates to connected clients without blocking threads.
Why it teaches Spring Boot: You will learn the reactive model, backpressure, and the invariants that keep async pipelines stable.
Core challenges you’ll face:
- Design backpressure strategies to prevent overload
- Maintain consistent ordering of streamed events
- Manage connection lifecycles safely
Key Concepts
- Reactive streams: Reactive Spring - Josh Long
- Backpressure: Reactive Spring - Josh Long
- Non-blocking IO: Reactive Spring - Josh Long
Difficulty: Advanced Time estimate: 1 month+ Prerequisites: Strong Spring Boot knowledge and comfort with async programming concepts.
Real World Outcome
You will open multiple clients and see a live event feed update in real time. You will be able to:
- Connect clients and watch them receive new events immediately
- Simulate slow clients and observe backpressure handling
- Verify ordering of events across multiple subscribers
Example Output:
$ curl http://localhost:8080/stream
event: update
id: 1
data: inventory adjusted
The Core Question You’re Answering
“How do reactive systems enforce stability under high concurrency?”
Before you write any code, sit with this question. Reactive design is not about speed alone, it is about system stability under load.
Concepts You Must Understand First
Stop and research these before coding:
- Reactive streams
- What is backpressure and why is it required?
- How do publishers and subscribers coordinate flow?
- Book Reference: “Reactive Spring” Ch. 2 - Josh Long
- Non-blocking IO
- Why does blocking break reactive pipelines?
- How do you detect hidden blocking calls?
- Book Reference: “Reactive Spring” Ch. 3 - Josh Long
Questions to Guide Your Design
Before implementing, think through these:
- Flow control
- How many events per second can a client handle?
- What happens when a client disconnects mid-stream?
- Ordering
- Which ordering guarantees are required?
- How will you verify order under concurrency?
Thinking Exercise
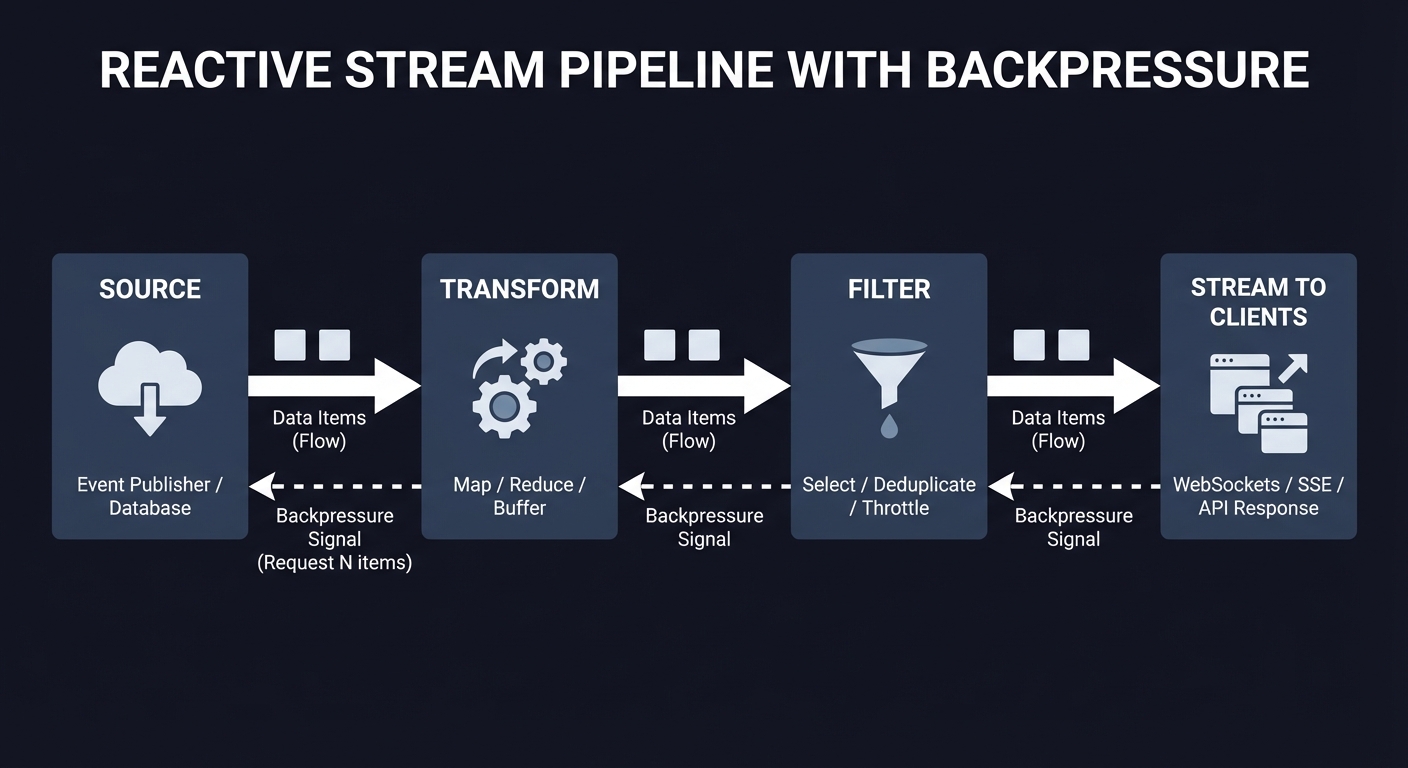
Reactive Pipeline Map
Before coding, map the pipeline:
Source -> Transform -> Filter -> Stream to clients
Questions while diagramming:
- Where do you apply backpressure?
- How do you prevent memory growth?
- What invariants must always hold for ordering?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What is backpressure and why does it matter?”
- “How is WebFlux different from Spring MVC?”
- “Why is blocking code dangerous in reactive systems?”
- “How do you handle errors in a reactive stream?”
- “How do you test reactive pipelines?”
Hints in Layers
Hint 1: Starting Point Define the event flow and expected rate.
Hint 2: Next Level Map client connections to stream subscribers.
Hint 3: Technical Details Use non-blocking APIs and verify backpressure behavior.
Hint 4: Tools/Debugging Simulate slow consumers and inspect memory usage.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Reactive streams | “Reactive Spring” by Josh Long | Ch. 2-3 |
| Async patterns | “Cloud Native Java” by Josh Long | Reactive sections |
Project 9: “Configuration Server and Client Fleet” — Centralized Config Management
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | High |
| Business Potential | High |
| Difficulty | Advanced |
| Knowledge Area | Configuration Management |
| Software or Tool | Spring Cloud Config |
| Main Book | Cloud Native Java |
What you’ll build: A centralized config server with multiple client services that refresh config without redeploy.
Why it teaches Spring Boot: You will learn configuration as a system-wide invariant and how Boot integrates with Spring Cloud.
Core challenges you’ll face:
- Organize configuration per service and environment
- Secure configuration access and secrets
- Refresh config without breaking running services
Key Concepts
- Externalized configuration: Cloud Native Java - Josh Long
- Configuration security: Spring Security in Action - Laurentiu Spilca
- Refresh scopes: Spring Cloud Config reference guide
Difficulty: Advanced Time estimate: 1 month+ Prerequisites: Spring Boot basics and familiarity with profiles.
Real World Outcome
You will change a config value in the server and watch clients update without redeploy. You will be able to:
- Change a rate limit value and see clients enforce it immediately
- Confirm unauthorized access to config is rejected
- Inspect logs to confirm refresh events occurred
Example Output:
$ curl http://localhost:8080/config-info
HTTP/1.1 200 OK
{
"service": "billing",
"rateLimit": 50,
"configVersion": "v12"
}
The Core Question You’re Answering
“How do I enforce configuration invariants across a fleet of services?”
Before you write any code, sit with this question. Configuration drift is a hidden source of failures; centralized config reduces that risk.
Concepts You Must Understand First
Stop and research these before coding:
- Configuration sources
- What is the precedence order of config values?
- How do you protect sensitive settings?
- Book Reference: “Cloud Native Java” configuration sections
- Dynamic refresh
- What is safe to refresh at runtime and what is not?
- How do you ensure changes propagate consistently?
- Book Reference: Spring Cloud Config reference guide
Questions to Guide Your Design
Before implementing, think through these:
- Change safety
- Which settings can be changed without restart?
- How will you roll back bad config quickly?
- Security boundary
- Who is allowed to see which config values?
- How will you audit config access?
Thinking Exercise
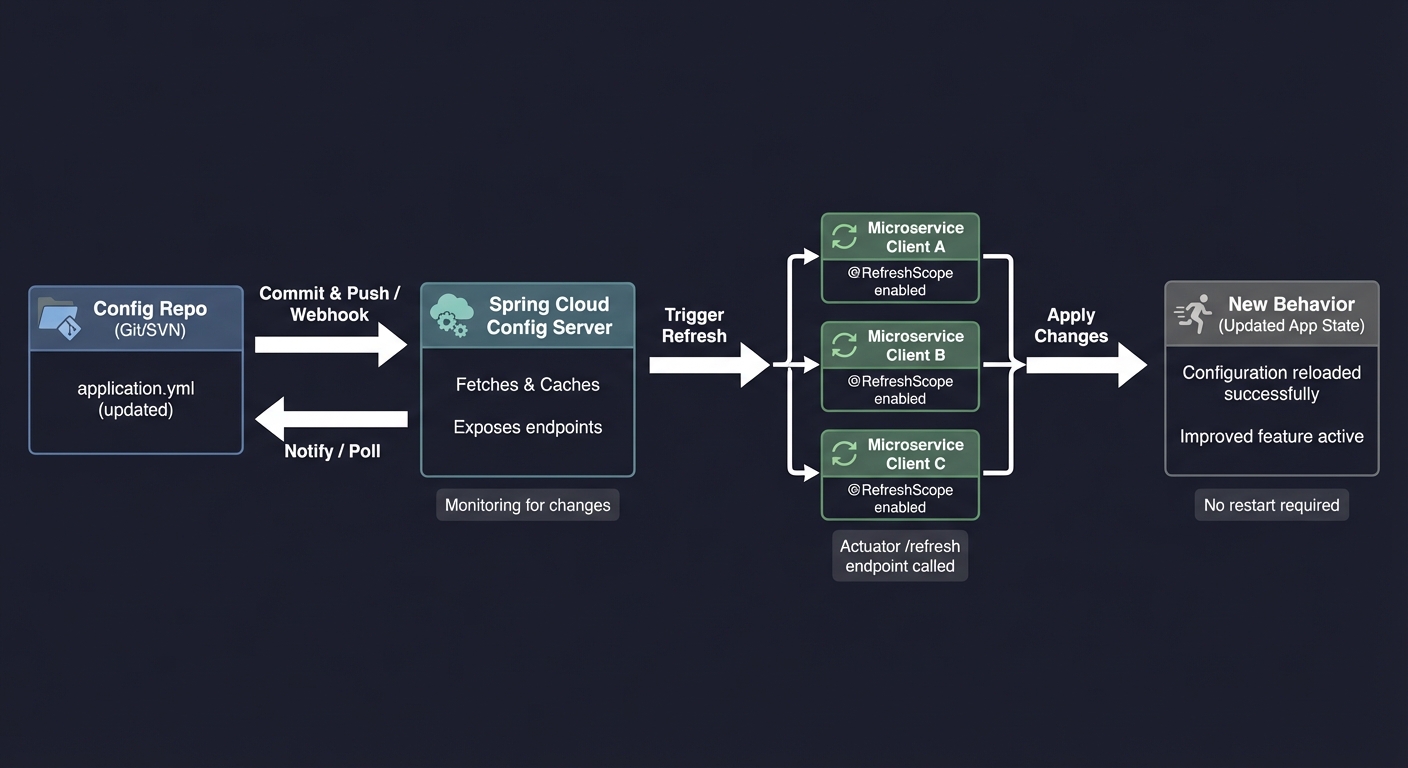
Config Flow Sketch
Before coding, sketch the flow:
Config repo -> Config server -> Client refresh -> New behavior
Questions while diagramming:
- Where is the source of truth?
- How do you validate configs before serving?
- What happens if the config server is down?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What is the purpose of Spring Cloud Config?”
- “How does config refresh work?”
- “How do you secure configuration values?”
- “How do you prevent configuration drift?”
- “What is the precedence of config sources in Spring Boot?”
Hints in Layers
Hint 1: Starting Point Define a simple config repo with base and environment overrides.
Hint 2: Next Level Secure config endpoints and test access control.
Hint 3: Technical Details Enable refresh and observe configuration changes without restart.
Hint 4: Tools/Debugging Log active config versions on startup and refresh.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Config server | “Cloud Native Java” by Josh Long | Configuration sections |
| Config security | “Spring Security in Action” by Laurentiu Spilca | Ch. 2-4 |
Project 10: “Search Service with Data Caching” — Cache Invalidation and Consistency
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | Medium |
| Business Potential | Medium |
| Difficulty | Intermediate |
| Knowledge Area | Caching |
| Software or Tool | Spring Cache |
| Main Book | Spring in Action |
What you’ll build: A search API that uses caching to reduce database load while keeping data consistent.
Why it teaches Spring Boot: You will learn how caching affects data invariants and how Boot integrates caching abstractions.
Core challenges you’ll face:
- Define cache keys that respect domain invariants
- Prevent stale data from violating correctness
- Measure cache hit rates and performance gains
Key Concepts
- Caching abstractions: Spring in Action - Craig Walls
- Consistency tradeoffs: Designing Data-Intensive Applications - Martin Kleppmann
- Performance measurement: Release It! - Michael T. Nygard
Difficulty: Intermediate Time estimate: 1-2 weeks Prerequisites: Spring Boot REST and database knowledge.
Real World Outcome
You will run a search endpoint and see response times improve with caching. You will be able to:
- Observe initial queries hitting the database
- Observe repeated queries served from cache
- Invalidate cache entries and verify fresh data returns
Example Output:
$ curl http://localhost:8080/search?q=monitor
HTTP/1.1 200 OK
{
"query": "monitor",
"results": 12,
"source": "cache"
}
The Core Question You’re Answering
“How do I add caching without breaking data correctness?”
Before you write any code, sit with this question. Caching is powerful but dangerous if it violates invariants.
Concepts You Must Understand First
Stop and research these before coding:
- Cache invalidation
- Why is invalidation the hardest problem in caching?
- What events must trigger cache eviction?
- Book Reference: “Designing Data-Intensive Applications” Ch. 5 - Martin Kleppmann
- Cache keys
- What makes a stable cache key?
- How do you avoid collisions and stale results?
- Book Reference: “Spring in Action” Ch. 13 - Craig Walls
Questions to Guide Your Design
Before implementing, think through these:
- Consistency
- Which queries can tolerate stale data and which cannot?
- How will you enforce different TTLs by query type?
- Measurement
- How will you measure cache hit rate?
- What is the expected performance improvement?
Thinking Exercise
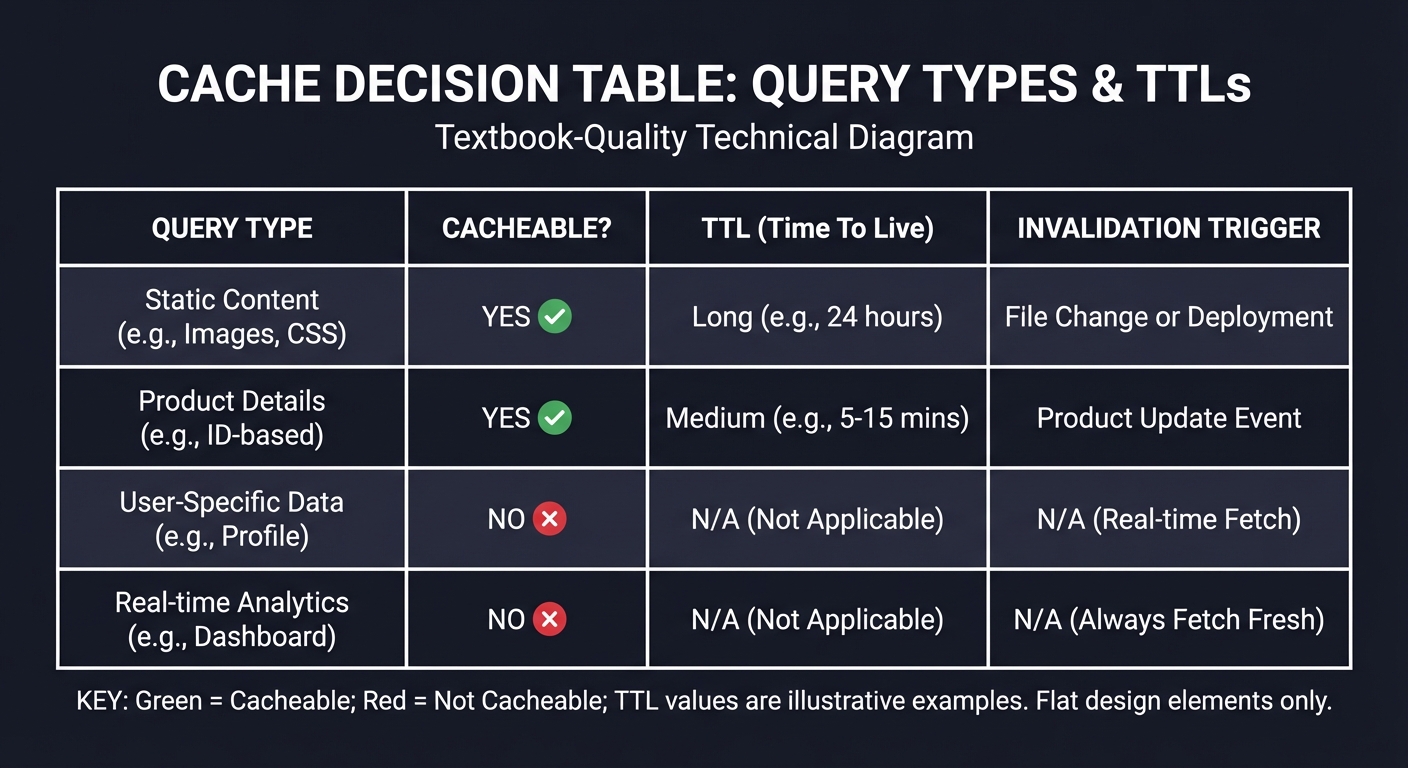
Cache Decision Table
Before coding, create a table of search cases:
Query type -> Cacheable? -> TTL -> Invalidation trigger
Questions while diagramming:
- Which queries must always be fresh?
- What invalidation event is guaranteed for each?
- How do you detect stale results in logs?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What is the hardest part about caching?”
- “How does Spring Cache work under the hood?”
- “What is cache stampede and how do you prevent it?”
- “How do you test cache behavior?”
- “When should you avoid caching entirely?”
Hints in Layers
Hint 1: Starting Point Identify one search query that is safe to cache first.
Hint 2: Next Level Define cache keys that include all query parameters.
Hint 3: Technical Details Configure TTLs and validate cache hits in logs.
Hint 4: Tools/Debugging Expose cache statistics via Actuator.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Caching | “Spring in Action” by Craig Walls | Ch. 13 |
| Consistency | “Designing Data-Intensive Applications” by Martin Kleppmann | Ch. 5 |
Project 11: “Multi-Module Monolith with Clean Boundaries” — Modular Architecture
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | High |
| Business Potential | High |
| Difficulty | Advanced |
| Knowledge Area | Architecture |
| Software or Tool | Spring Boot, Maven or Gradle |
| Main Book | Clean Architecture |
What you’ll build: A modular monolith with explicit boundaries between billing, inventory, and user management.
Why it teaches Spring Boot: You will learn how Boot supports clean architecture, module boundaries, and dependency direction in a real system.
Core challenges you’ll face:
- Enforce module boundaries at build time
- Define interfaces for cross-module collaboration
- Prevent accidental dependency leaks
Key Concepts
- Clean architecture: Clean Architecture - Robert C. Martin
- Modular design: Building Microservices - Sam Newman
- Dependency management: Maven or Gradle docs
Difficulty: Advanced Time estimate: 1 month+ Prerequisites: Strong Spring Boot knowledge and understanding of software architecture.
Real World Outcome
You will run a multi-module system with strict boundaries. You will be able to:
- Build and run the entire monolith with clear module separation
- Demonstrate that a module cannot access another module directly without an interface
- Show dependency graphs that prove boundary enforcement
Example Output:
$ ./gradlew projects
Root project
+--- billing
+--- inventory
+--- users
The Core Question You’re Answering
“How do I keep a Spring Boot monolith modular and maintainable?”
Before you write any code, sit with this question. Many teams fail because their monolith turns into a tangled web of dependencies.
Concepts You Must Understand First
Stop and research these before coding:
- Dependency direction
- Which modules are allowed to depend on others?
- How do you enforce architecture rules in build tools?
- Book Reference: “Clean Architecture” Ch. 1-3 - Robert C. Martin
- Module contracts
- What should a module expose vs hide?
- How do you keep internal APIs private?
- Book Reference: “Building Microservices” Ch. 2 - Sam Newman
Questions to Guide Your Design
Before implementing, think through these:
- Boundary enforcement
- How will you detect boundary violations?
- Which tools will enforce these rules in CI?
- Collaboration patterns
- When should modules communicate via events vs direct calls?
- How will you prevent cyclic dependencies?
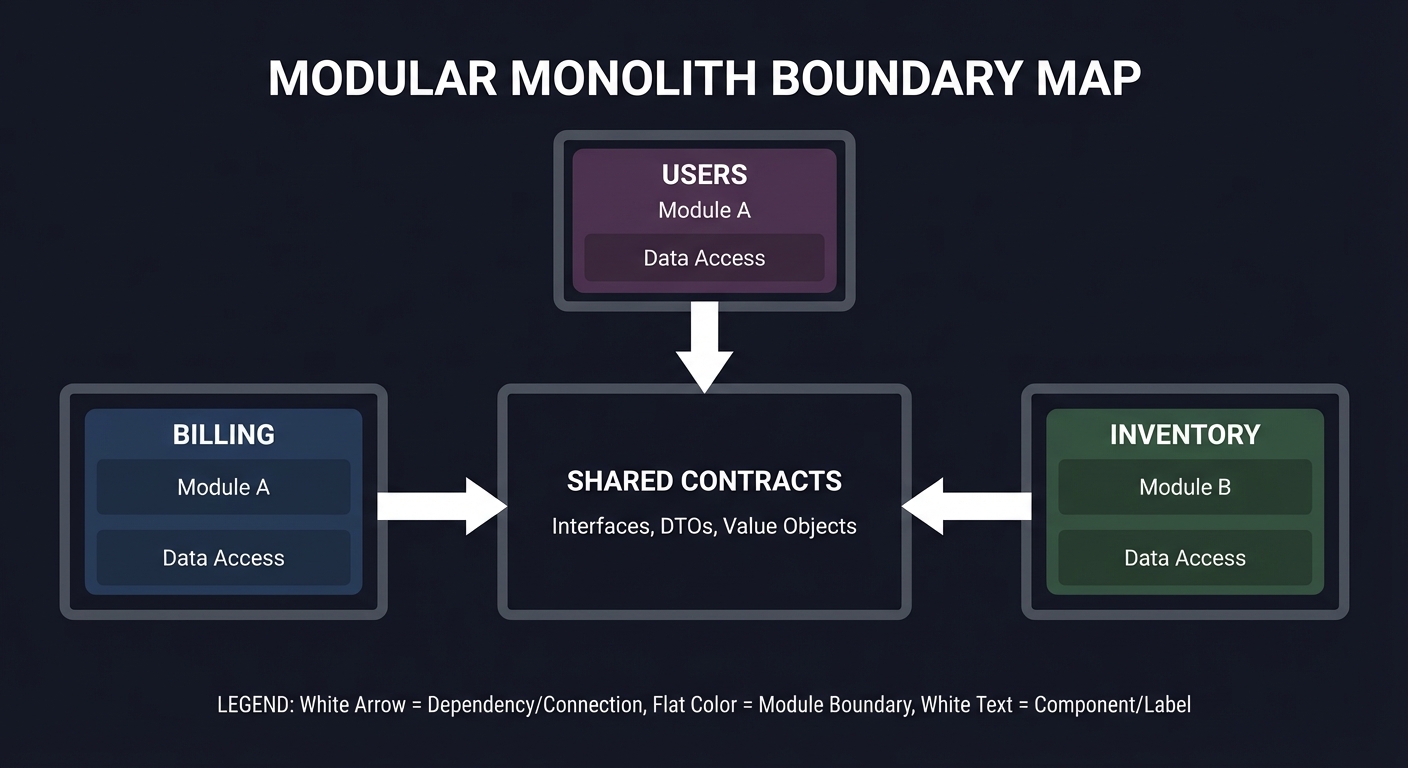
Thinking Exercise
Boundary Map
Before coding, sketch module boundaries:
Billing -> Shared contracts <- Inventory
Users -> Shared contracts
Questions while diagramming:
- Which module owns each domain concept?
- How do you prevent cross-cutting shortcuts?
- What test proves boundaries are intact?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What is a modular monolith and why use it?”
- “How do you enforce module boundaries in Java?”
- “What are the risks of a shared database across modules?”
- “How would you split this monolith later?”
- “How does Spring Boot help or hurt modularity?”
Hints in Layers
Hint 1: Starting Point Define modules and their public interfaces on paper first.
Hint 2: Next Level Create shared contracts that are stable and minimal.
Hint 3: Technical Details Use build tooling to enforce dependency direction.
Hint 4: Tools/Debugging Generate dependency graphs and review them regularly.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Clean architecture | “Clean Architecture” by Robert C. Martin | Ch. 1-3 |
| Modular systems | “Building Microservices” by Sam Newman | Ch. 2 |
Project 12: “Testing Pyramid for Spring Boot” — Unit, Slice, and Integration Tests
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | Medium |
| Business Potential | Medium |
| Difficulty | Intermediate |
| Knowledge Area | Testing |
| Software or Tool | Spring Boot Test |
| Main Book | Testing Java Microservices |
What you’ll build: A test suite that covers unit, slice, and integration tests for a Boot service.
Why it teaches Spring Boot: You will learn how Spring Boot testing tools enforce correctness and prevent regression.
Core challenges you’ll face:
- Define the right balance between unit and integration tests
- Use test slices to keep feedback fast
- Validate behavior under realistic configurations
Key Concepts
- Test slicing: Spring in Action - Craig Walls
- Test strategy: Testing Java Microservices - Alex Soto et al.
- Integration testing: Release It! - Michael T. Nygard
Difficulty: Intermediate Time estimate: 1-2 weeks Prerequisites: Familiarity with JUnit and basic Spring Boot structure.
Real World Outcome
You will run a full test suite and see a clear report. You will be able to:
- Run unit tests that execute in seconds
- Run integration tests that spin up real dependencies
- Identify which failures break invariants immediately
Example Output:
$ ./gradlew test
BUILD SUCCESSFUL
Tests: 52, Failures: 0
The Core Question You’re Answering
“How do I prove my Spring Boot system is correct and stays correct?”
Before you write any code, sit with this question. Tests are the mechanism that protect invariants over time.
Concepts You Must Understand First
Stop and research these before coding:
- Test pyramid
- Why should most tests be unit tests?
- What failures demand integration coverage?
- Book Reference: “Testing Java Microservices” Ch. 1-2 - Alex Soto et al.
- Spring test slices
- What does @WebMvcTest include and exclude?
- Why do slices make tests faster?
- Book Reference: “Spring in Action” Ch. 10 - Craig Walls
Questions to Guide Your Design
Before implementing, think through these:
- Test scope
- Which invariants must be validated at the service layer?
- Which require full integration tests?
- Test data
- How do you keep fixtures readable and stable?
- How do you prevent environment-specific failures?
Thinking Exercise
Test Coverage Map
Before coding, map tests to invariants:
Invariant -> Unit test -> Slice test -> Integration test
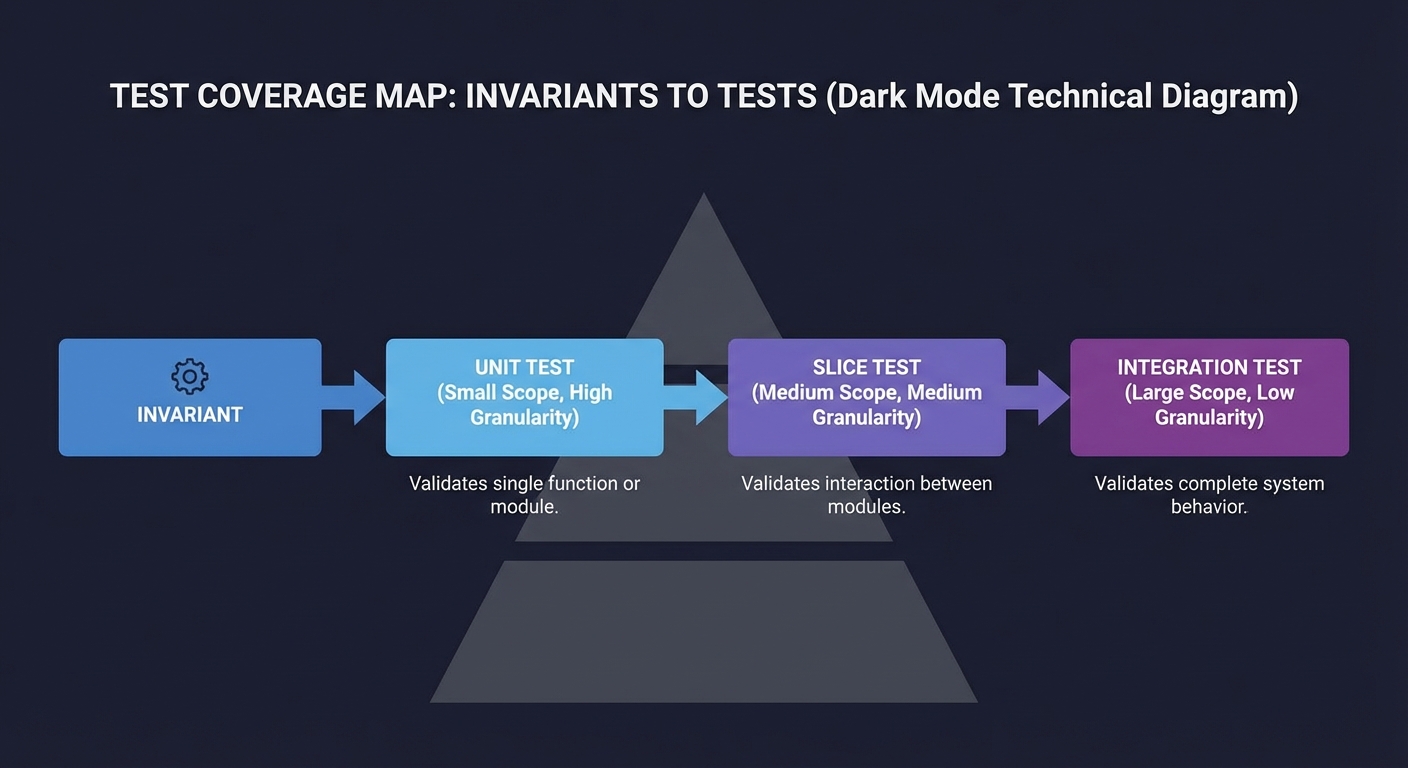
Questions while diagramming:
- Which invariants are most fragile?
- What tests catch them early?
- How do you keep tests fast?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What is the testing pyramid?”
- “What are Spring test slices and why use them?”
- “How do you test configuration-driven behavior?”
- “How do you keep integration tests stable?”
- “What would you test first in a new service?”
Hints in Layers
Hint 1: Starting Point List the invariants and decide which tests protect them.
Hint 2: Next Level Add slice tests for web and data layers.
Hint 3: Technical Details Use separate profiles for test configuration.
Hint 4: Tools/Debugging Keep tests isolated and inspect slow ones for hidden integration.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Testing strategy | “Testing Java Microservices” by Alex Soto et al. | Ch. 1-2 |
| Spring testing | “Spring in Action” by Craig Walls | Ch. 10 |
Project 13: “Multi-Tenant SaaS Starter” — Tenant Isolation and Identity
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | High |
| Business Potential | High |
| Difficulty | Advanced |
| Knowledge Area | Multi-Tenancy |
| Software or Tool | Spring Boot, Spring Data |
| Main Book | Building Microservices |
What you’ll build: A SaaS starter that isolates tenant data and enforces tenancy boundaries.
Why it teaches Spring Boot: You will confront the hardest data invariants: isolation, identity propagation, and safe query scoping.
Core challenges you’ll face:
- Enforce tenant scoping in every query
- Prevent cross-tenant data leaks
- Manage tenant-specific configuration
Key Concepts
- Multi-tenancy patterns: Building Microservices - Sam Newman
- Data isolation: Designing Data-Intensive Applications - Martin Kleppmann
- Security boundaries: Spring Security in Action - Laurentiu Spilca
Difficulty: Advanced Time estimate: 1 month+ Prerequisites: Strong Spring Boot, Spring Data, and security understanding.
Real World Outcome
You will provision multiple tenants and verify strict data isolation. You will be able to:
- Create data for Tenant A and confirm Tenant B cannot access it
- Inspect logs to see tenant identifiers flow through the system
- Demonstrate safe configuration overrides per tenant
Example Output:
$ curl -H "X-Tenant: alpha" http://localhost:8080/resources
HTTP/1.1 200 OK
{
"tenant": "alpha",
"records": 12
}
The Core Question You’re Answering
“How do I guarantee data isolation in a multi-tenant Spring Boot system?”
Before you write any code, sit with this question. Multi-tenancy is a test of whether your invariants are truly enforced everywhere.
Concepts You Must Understand First
Stop and research these before coding:
- Tenant identification
- How is tenant identity carried through requests?
- Where should tenant context be stored?
- Book Reference: “Building Microservices” Ch. 6 - Sam Newman
- Data isolation
- What is the difference between shared schema and dedicated schema?
- How do you prevent accidental cross-tenant queries?
- Book Reference: “Designing Data-Intensive Applications” Ch. 5 - Martin Kleppmann
Questions to Guide Your Design
Before implementing, think through these:
- Isolation strategy
- Which isolation model fits your constraints?
- How will you test that isolation is enforced?
- Configuration overrides
- Which settings can vary by tenant?
- How do you prevent tenant-specific misconfiguration?
Thinking Exercise
Tenant Context Flow
Before coding, map tenant identity flow:
Request -> Tenant resolver -> Context -> Repository query
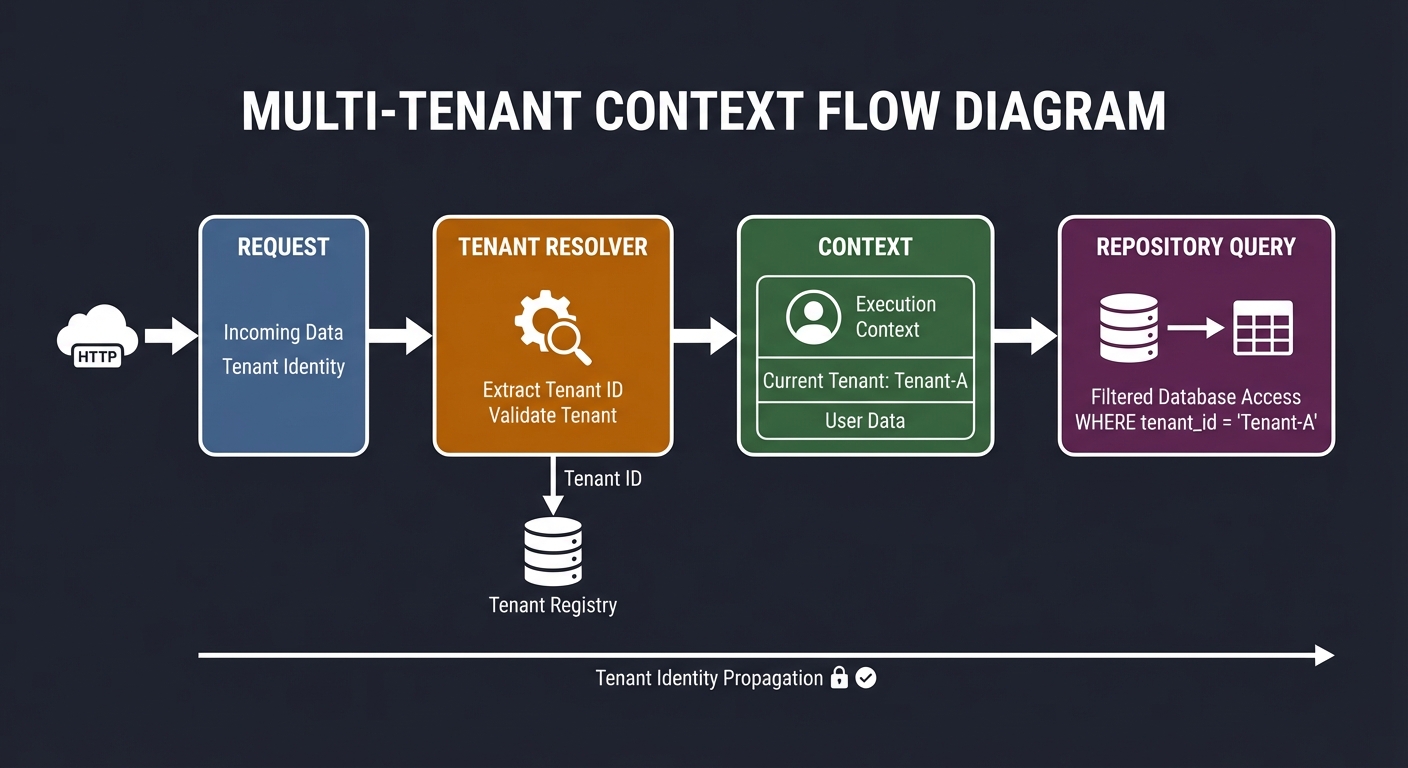
Questions while diagramming:
- Where is tenant identity validated?
- How do you prevent context leaks between requests?
- How do you test that tenant scoping cannot be bypassed?
The Interview Questions They’ll Ask
Prepare to answer these:
- “What are common multi-tenancy models?”
- “How do you enforce tenant isolation at the data layer?”
- “How do you propagate tenant identity in Spring Boot?”
- “What are the risks of shared schema multi-tenancy?”
- “How do you test for tenant data leaks?”
Hints in Layers
Hint 1: Starting Point Pick a simple tenant identifier and enforce it consistently.
Hint 2: Next Level Ensure every query includes tenant scope by default.
Hint 3: Technical Details Store tenant context in a request-scoped holder and clear it every request.
Hint 4: Tools/Debugging Add logging that prints tenant identifiers on each query.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Multi-tenancy | “Building Microservices” by Sam Newman | Ch. 6 |
| Data isolation | “Designing Data-Intensive Applications” by Martin Kleppmann | Ch. 5 |
Project Comparison Table
| Project | Difficulty | Time | Depth of Understanding | Fun Factor |
|---|---|---|---|---|
| Config-Driven Personal Finance API | Beginner | 1-2 weeks | Medium | Medium |
| Order Service with Transactional Invariants | Intermediate | 1-2 weeks | High | High |
| Secure Account Management Service | Intermediate | 1-2 weeks | High | High |
| Event-Driven Inventory Updates | Advanced | 1 month+ | Very High | High |
| Resilient External API Client | Intermediate | 1-2 weeks | High | Medium |
| Observability-First Service | Intermediate | 1-2 weeks | High | Medium |
| Batch Data Pipeline with Spring Batch | Intermediate | 1-2 weeks | High | Medium |
| Reactive Event Feed Service | Advanced | 1 month+ | Very High | High |
| Configuration Server and Client Fleet | Advanced | 1 month+ | Very High | Medium |
| Multi-Tenant SaaS Starter | Advanced | 1 month+ | Very High | High |
Recommendation
Start with Config-Driven Personal Finance API if you are new to Spring Boot because it forces you to understand configuration, validation, and the request lifecycle. Then do Order Service with Transactional Invariants to internalize data invariants and transaction boundaries. If you want to specialize in production readiness, prioritize Observability-First Service and Resilient External API Client.
Final Overall Project
Project 14: “Full-Stack Commerce Platform” — Boot Ecosystem Capstone
| Attribute | Value |
|---|---|
| File | SPRING_BOOT_SPRINT_2_DATA_AND_INVARIANTS_PROJECTS.md |
| Main Programming Language | Java |
| Alternative Programming Languages | Kotlin, Groovy, Scala |
| Coolness Level | Very High |
| Business Potential | Very High |
| Difficulty | Advanced |
| Knowledge Area | End-to-End Systems |
| Software or Tool | Spring Boot, Spring Cloud, Spring Security, Spring Data, Actuator |
| Main Book | Cloud Native Java |
What you’ll build: A commerce platform with orders, inventory, users, configuration server, observability, security, and resilient integrations.
Why it teaches Spring Boot: It forces you to combine every concept from this sprint: configuration, data invariants, transactions, security, observability, and resilience.
Core challenges you’ll face:
- Coordinate transactions and data invariants across multiple services
- Enforce security boundaries across user and admin flows
- Operate the system with full observability and resilience
Key Concepts
- Microservice architecture: Building Microservices - Sam Newman
- Observability: Cloud Native Java - Josh Long
- Security at scale: Spring Security in Action - Laurentiu Spilca
Difficulty: Advanced Time estimate: 1 month+ Prerequisites: Completion of at least three projects above, plus strong Spring Boot knowledge.
Real World Outcome
You will run a full system with multiple services and see real commerce workflows. You will be able to:
- Create users, authenticate them, and place orders
- Observe inventory updates and payment flows
- Monitor health and metrics across all services in a dashboard
Example Output:
$ curl -X POST http://localhost:8080/orders
HTTP/1.1 201 Created
{
"orderId": 9001,
"status": "CONFIRMED",
"total": 129.99
}
The Core Question You’re Answering
“Can I build and operate a production-grade Spring Boot system end-to-end?”
Before you write any code, sit with this question. This capstone is a full ecosystem test, not just a feature build.
Concepts You Must Understand First
Stop and research these before coding:
- Service boundaries
- What belongs in one service vs another?
- How do you avoid tight coupling across services?
- Book Reference: “Building Microservices” Ch. 2 - Sam Newman
- Operational readiness
- What telemetry proves the system is healthy?
- How do you handle failure without data loss?
- Book Reference: “Release It!” Ch. 4-5 - Michael T. Nygard
Questions to Guide Your Design
Before implementing, think through these:
- System contracts
- Which invariants must hold across all services?
- How will you detect violations early?
- Deployment strategy
- What environments will you deploy to?
- How will you manage configuration and secrets safely?
Thinking Exercise
End-to-End Flow Map
Before coding, map the full flow:
User -> Auth -> Order -> Inventory -> Payment -> Observability
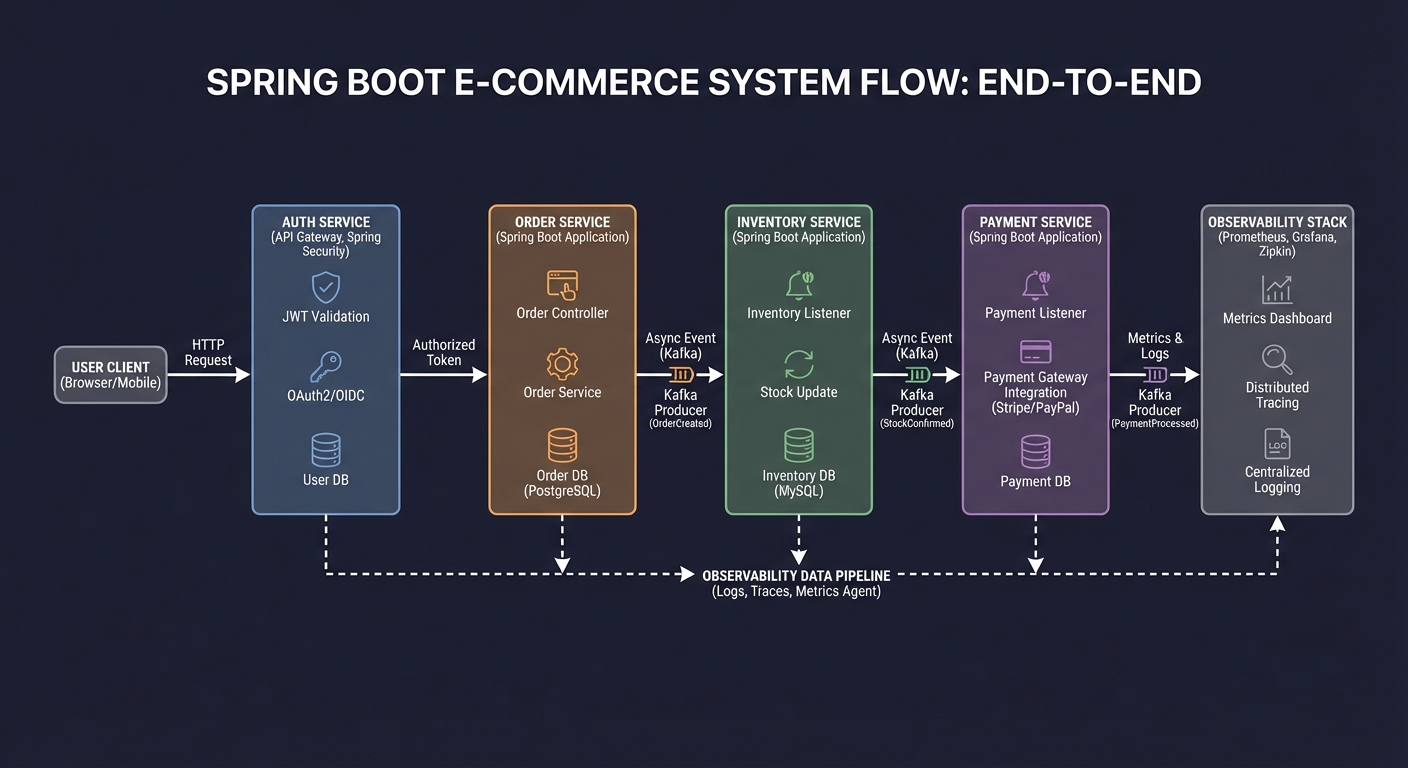
Questions while diagramming:
- Where are the most fragile invariants?
- Which service failures can be tolerated?
- What is your rollback strategy?
The Interview Questions They’ll Ask
Prepare to answer these:
- “How do you design service boundaries in Spring Boot?”
- “How do you ensure data consistency across services?”
- “How do you secure internal service communication?”
- “How do you observe system health in production?”
- “How do you handle partial failures in a distributed system?”
Hints in Layers
Hint 1: Starting Point Define the system boundaries and the invariants that must hold.
Hint 2: Next Level Design each service with clear contracts and failure modes.
Hint 3: Technical Details Use Boot defaults for wiring, then override only when justified.
Hint 4: Tools/Debugging Instrument everything with metrics and tracing from the start.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Microservices | “Building Microservices” by Sam Newman | Ch. 2-6 |
| Resilience | “Release It!” by Michael T. Nygard | Ch. 4-5 |
| Observability | “Cloud Native Java” by Josh Long | Observability sections |
Summary
You now have 10 Spring Boot projects that cover the full ecosystem:
- Config-Driven Personal Finance API
- Order Service with Transactional Invariants
- Secure Account Management Service
- Event-Driven Inventory Updates
- Resilient External API Client
- Observability-First Service
- Batch Data Pipeline with Spring Batch
- Reactive Event Feed Service
- Configuration Server and Client Fleet
- Multi-Tenant SaaS Starter
Each project forces you to confront Spring Boot invariants: configuration, data consistency, security boundaries, resilience, and observability.