Learn SPIFFE & SPIRE: From Zero to Zero Trust Workload Master
Goal: Deeply understand the Secure Production Identity Framework for Everyone (SPIFFE) and its reference implementation, SPIFFE Runtime Environment (SPIRE). You will master the foundational principles of Zero Trust, workload attestation, and cryptographic identity issuance. By the end of this journey, you will be able to design and implement a security architecture where every service, container, and function has a verifiable, short-lived identity, eliminating static secrets and enabling “Identity-First” security in any environment.
Why Identity-First Security Matters
In the early days of computing, security was simple: we built a big wall (the firewall) around our data center and trusted everything inside. But the rise of cloud computing, microservices, and remote work has shattered that perimeter.
According to the 2023 Verizon Data Breach Investigations Report, 74% of all breaches include the human element, often involving credential theft. In machine-to-machine communication, the “human” is replaced by “static secrets”—API keys, passwords, and long-lived certificates buried in config files.
If an attacker breaches a single service and finds a database password, the entire “trusted” network is compromised. This is why we need Zero Trust.
In the Zero Trust model:
- The Network is Untrusted: We assume the network is already compromised.
- Identity is the New Perimeter: We verify “who” is calling, not “where” they are calling from.
- Continuous Verification: Identity is short-lived and rotated automatically.
SPIFFE and SPIRE solve the “Bottom Turtle” problem—the logical paradox of how to safely deliver a secret to a service without already having a secret to identify that service.
The Bottom Turtle Problem
High-level Security "Connect to the Database securely"
↓
Need mTLS Cert "How do I get the cert?"
↓
Ask a Vault/CA "How do I prove I'm allowed to ask?"
↓
Use an API Key "Where did the API key come from?"
↓
Hardcoded Secret "THE BOTTOM TURTLE" (The static secret)
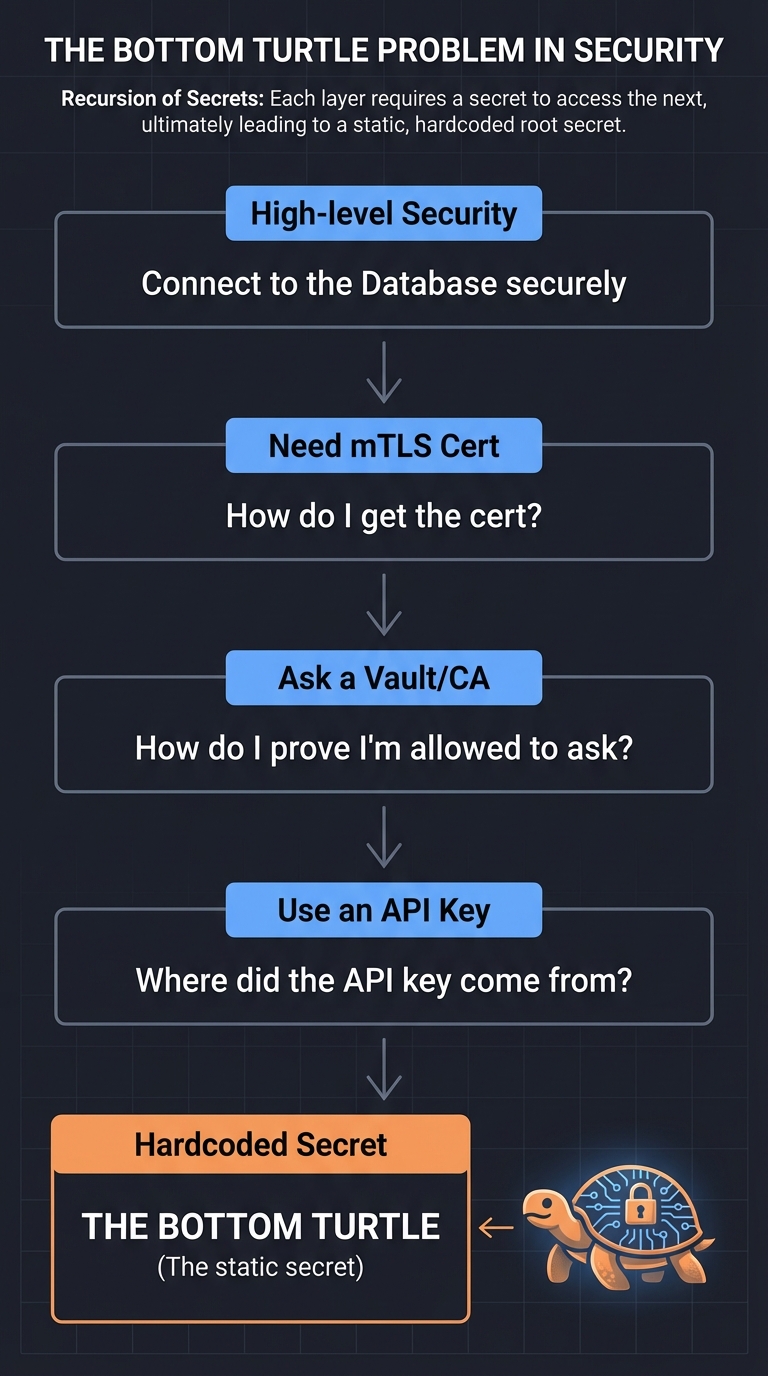
SPIRE eliminates the “Bottom Turtle” by using Attestation—verifying the workload’s properties (like its Kubernetes Service Account or its Linux Process ID) against the underlying platform’s metadata.
The Architecture: SPIRE Server & Agent
SPIRE (the SPIFFE Runtime Environment) is the reference implementation of SPIFFE. It is designed as a distributed system that manages the lifecycle of identities.
┌─────────────────────────────────┐
│ SPIRE Server │ ← Central Authority
│ (CA, Registry, Policy) │
└───────────────┬─────────────────┘
│ Node Attestation (mTLS)
┌───────────────┴─────────────────┐
│ SPIRE Agent │ ← Runs on every Host/Node
│ (Workload API, Cache) │
└───────────────┬─────────────────┘
│ Workload API (Unix Socket)
┌───────────────┴─────────────────┐
│ Your Workload │ ← App, Sidecar, or Function
│ (Requests identity) │
└─────────────────────────────────┘
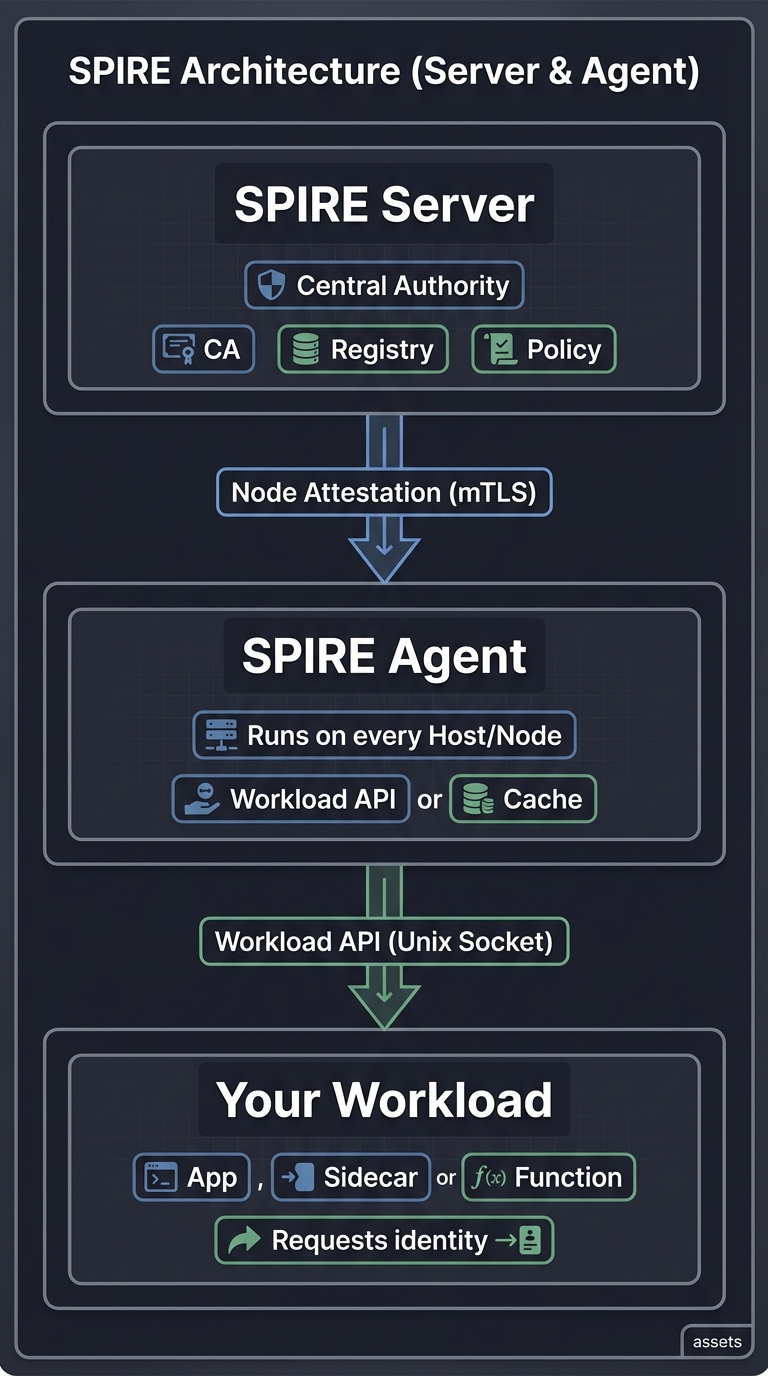
SPIRE Server
The Server is the central authority. It manages the identity registry, issues SVIDs to Agents, and validates Node Attestation. It acts as the Root of Trust for the entire system.
SPIRE Agent
The Agent runs on every node where workloads reside. It performs workload attestation, caches SVIDs from the Server, and exposes the Workload API via a local Unix Domain Socket.
The Attestation Mechanism: Establishing Trust
Attestation is the process by which SPIRE proves the identity of a workload without using shared secrets. This happens in two phases:
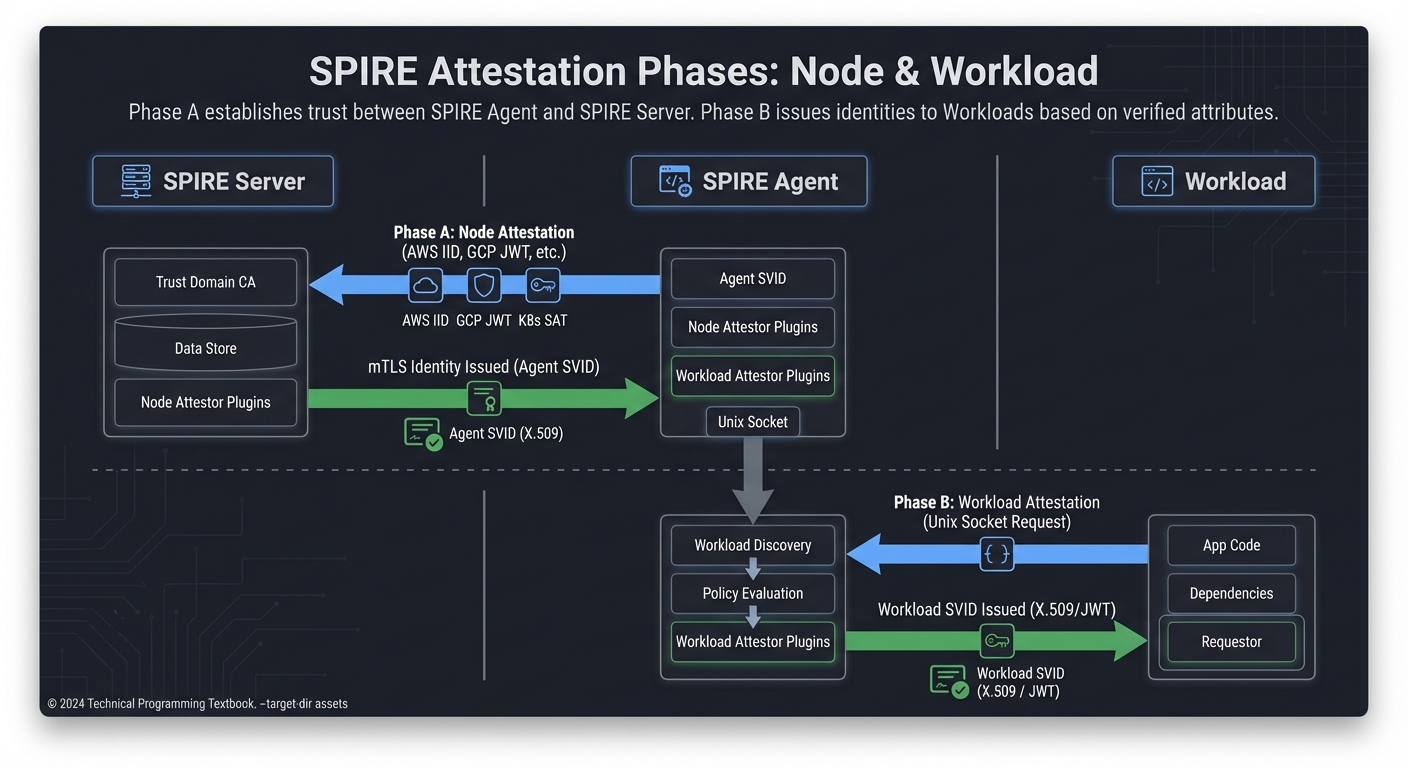
Phase A: Node Attestation
The Agent proves to the Server that it is running on a valid node.
- On AWS: The Agent uses the Instance Identity Document (IID).
- On Kubernetes: The Agent uses the Projected Service Account Token (PSAT).
- On Bare Metal: The Agent can use a TPM (Trusted Platform Module) or a Join Token.
Phase B: Workload Attestation
The Workload proves to the Agent that it is who it claims to be.
- The Workload calls the local Unix socket.
- The Agent inspects the connection to find the caller’s PID/UID/GID.
- The Agent looks up the process metadata (e.g., cgroups, K8s labels).
- The Agent matches this metadata against Selectors defined in the Server.
SPIFFE ID & SVID Anatomy
A SPIFFE ID is a structured URI that represents a unique identity: spiffe://trust-domain/path/to/workload.
An SVID (SPIFFE Verifiable Identity Document) is the cryptographic proof of that identity.
| SVID Type | Format | Internal Structure |
|---|---|---|
| X.509-SVID | X.509 Certificate | SPIFFE ID is stored in the Subject Alternative Name (SAN) field as a URI. |
| JWT-SVID | JSON Web Token | SPIFFE ID is stored in the subject (sub) claim. |
Key Feature: SVIDs are designed to be short-lived. SPIRE automatically handles the rotation of these documents before they expire, ensuring that even if a credential is leaked, its window of utility is minimal.
Concept Summary Table
| Concept Cluster | What You Need to Internalize |
|---|---|
| Trust Domain | The security boundary (e.g., prod.acme.com). The “root” of your identity tree. |
| Attestation | Proving identity via runtime properties rather than pre-shared keys. |
| Workload API | The local gRPC channel where apps “ask” for their identity. |
| SVID Rotation | Identities are short-lived (e.g., 1 hour). SPIRE rotates them automatically. |
| Selectors | The “rules” for identity (e.g., k8s:ns:default). If you have the selector, you get the ID. |
| Federation | Allowing two different SPIRE clusters to trust each other’s identities. |
Deep Dive Reading by Concept
Zero Trust Fundamentals
| Concept | Book & Chapter |
|---|---|
| The shift from network to identity | Zero Trust Networks by Gilman & Barth — Ch. 1: “Zero Trust Fundamentals” |
| The cost of static credentials | Security Engineering by Ross Anderson — Ch. 3: “System Issues” |
| PKI and Certificate Chains | Serious Cryptography by Aumasson — Ch. 13: “PKI” |
Distributed Identity & SPIFFE/SPIRE
| Concept | Book & Chapter |
|---|---|
| Workload Identity Patterns | Solving the Bottom Turtle (SPIRE Authors) — All Chapters |
| gRPC and Unix Domain Sockets | The Linux Programming Interface by Kerrisk — Ch. 57: “Sockets: Unix Domain” |
| Kubernetes Security context | Kubernetes Up & Running by Burns et al — Ch. 15: “Security” |
| Envoy & SDS (Secret Discovery) | Istio Explained by Sun & Posta — Ch. 3: “The Envoy Proxy” |
Project 1: Basic SPIRE Deployment & Workload Identity Issuance
What you’ll build: A minimal SPIRE deployment consisting of a SPIRE Server and a SPIRE Agent, and then register a simple “hello-world” workload to obtain its unique SPIFFE ID and SVID.
Real World Outcome
You will interact directly with the “Source of Truth” for identity. You’ll run a command-line tool that “becomes” the workload and requests its passport.
Example Output:
# 1. Start the Server and Agent
$ ./spire-server run &
$ ./spire-agent run -joinToken <TOKEN> &
# 2. Register the workload (Admin action)
$ ./spire-server entry create -spiffeID spiffe://example.org/workload/tester -selector unix:uid:1000
# 3. Request identity (Workload action)
$ ./spire-agent api fetch x509 -write /tmp/certs
Received SVID: spiffe://example.org/workload/tester
Expires: 2025-12-26 15:00:00 UTC
Writing SVID to /tmp/certs/svid.0.pem...
Writing Key to /tmp/certs/svid.0.key.pem...
# You just solved the Bottom Turtle problem!
The Core Question You’re Answering
“How can a process prove who it is to a local authority without holding any pre-shared secrets or passwords?”
Concepts You Must Understand First
- Unix Domain Sockets: Why does SPIRE use
/tmp/spire-agent/public/api.sockinstead of a TCP port? - Selectors: What does
unix:uid:1000actually mean? How does the agent verify this? - PKI: What is a “Trust Bundle” and why does the workload need it to verify others?
Questions to Guide Your Design
- How does the SPIRE Agent prove its identity to the Server initially?
- If I change my Linux user (UID), will the
api fetchcommand still work? - What happens if the SPIRE Server goes down? Does the workload lose its identity immediately?
Thinking Exercise
Draw a sequence diagram showing the messages between the Workload, the Agent, and the Server. Mark where “Workload Attestation” happens. Does the Server ever talk to the Workload directly? (Spoiler: No).
The Interview Questions They’ll Ask
- “Explain the difference between Node Attestation and Workload Attestation.”
- “Why are SPIFFE SVIDs typically short-lived (e.g., 1 hour)?”
- “What prevents one process on a node from stealing another process’s identity in SPIRE?”
Hints in Layers
- Hint 1: Start by running SPIRE in a single Docker container to avoid networking headaches.
- Hint 2: Use
spire-server entry showto verify your registration was successful. - Hint 3: If
api fetchfails, check the Agent logs. It will tell you exactly which selectors it detected for your process.
Books That Will Help
| Topic | Book | Chapter | |——-|——|———| | Unix Sockets | “The Linux Programming Interface” | Ch. 57 | | SPIRE Internal Flow | “Solving the Bottom Turtle” | Ch. 4-5 |
Project 2: Secure Service-to-Service Communication with mTLS
What you’ll build: Two simple microservices (a “client” and a “server”) that communicate securely using Mutual TLS (mTLS), where their identities are provided by SPIRE SVIDs.
Real World Outcome
You will see two services that cannot talk to each other if you stop the SPIRE Agent, but establish a secure, encrypted tunnel automatically when identity is present.
Example Output:
# Start Server
$ go run server.go
Listening on :8443 (mTLS enabled)
# Start Client (with valid identity)
$ go run client.go
Successfully connected to spiffe://example.org/server
Server response: "Hello, authenticated client!"
# Start Client (with WRONG identity)
$ go run malicious_client.go
TLS Error: remote error: tls: certificate required
# Access Denied! No identity, no entry.
The Core Question You’re Answering
“How do we move from ‘Trust the Network’ to ‘Trust the Identity’ using standard TLS?”
Concepts You Must Understand First
- mTLS Handshake: Why do both sides need to present a certificate?
- SAN (Subject Alternative Name): How does SPIFFE hide its ID inside a standard X.509 cert?
- Identity-Aware Middleware: How do you write code that says
if client.spiffeID != "authorized-app" then return 403?
Questions to Guide Your Design
- How do you handle certificate rotation in your Go/Python code without restarting the app?
- What happens if the Client trusts the Server, but the Server doesn’t trust the Client?
- How do you verify the specific SPIFFE ID of the peer, not just that they have any valid cert?
Thinking Exercise
Imagine you are an attacker. You have access to the network between the client and server. Can you read the data? Can you impersonate the server? What if you steal the SVID from the client’s memory?
The Interview Questions They’ll Ask
- “How does SPIFFE handle CRLs (Certificate Revocation Lists)?” (Answer: It doesn’t; it uses short lifetimes).
- “Describe the steps in a Mutual TLS handshake.”
- “How does a service verify that a SPIFFE ID belongs to a specific trust domain?”
Hints in Layers
- Hint 1: Use the
spiffe-go-toolkit. It handles the SVID rotation and Workload API communication for you. - Hint 2: Print the Peer’s SPIFFE ID in your server logs to see it in action.
- Hint 3: Use
openssl s_client -connect localhost:8443to try and connect manually. See it fail because you don’t have a valid SVID.
Books That Will Help
| Topic | Book | Chapter | |——-|——|———| | Cryptography & TLS | “Serious Cryptography” | Ch. 13 | | mTLS Patterns | “Zero Trust Networks” | Ch. 4 |
Project 3: Custom Node Attestor Plugin
What you’ll build: A custom SPIRE Node Attestor plugin that identifies a node based on a unique attribute (e.g., a specific kernel parameter or custom file).
Real World Outcome
You will extend the SPIRE Server to recognize a “Non-Cloud” node by a custom hardware ID or secret file, allowing you to bring “Zero Trust” to edge devices or legacy data centers.
Example Output:
# 1. Start SPIRE Server with your plugin loaded
$ spire-server run -config server.conf
time="2025-12-27T10:00:00Z" level=info msg="Plugin loaded" name=my_custom_attestor
# 2. Start SPIRE Agent on a node with the "secret file"
$ cat /etc/node_id
"hardware-id-9988-7766"
$ spire-agent run -config agent.conf
time="2025-12-27T10:00:05Z" level=info msg="Node attestation successful" trust_domain=example.org node_id=spiffe://example.org/spire/agent/my_custom_attestor/hardware-id-9988-7766
The Core Question You’re Answering
“How do we trust the hardware itself before we trust the software running on it, especially in environments where standard Cloud metadata is unavailable?”
Concepts You Must Understand First
- SPIRE Plugin Architecture: SPIRE uses HashiCorp’s
go-pluginsystem. Plugins are separate binaries that communicate with the main process over gRPC. - Node Attestation Flow: The sequence of events where the Agent collects evidence (data) and the Server validates it against a known truth.
- SPIRE API (GRPC): You’ll need to implement the
NodeAttestorservice defined in the SPIRE plugin SDK.
Questions to Guide Your Design
- What “proof” can the Node present that is hard to spoof but easy to verify? (e.g., a serial number from
/sys/class/dmi/id/product_serial). - If an attacker copies the “secret file” to another node, how does your plugin prevent identity theft? (Look into TPM-based attestation for a more secure approach).
- How do you map the evidence to a specific SPIFFE ID structure?
Thinking Exercise
Imagine you are building a system for a fleet of 1,000 Raspberry Pis. They don’t have AWS roles. How would you uniquely identify each Pi using your custom plugin? What hardware features would you query?
The Interview Questions They’ll Ask
- “What is a ‘Handshake’ in SPIRE plugin terms?”
- “How would you attest a node that doesn’t have a TPM or Cloud metadata?”
- “Explain how the Server-side and Agent-side components of a Node Attestor work together.”
Hints in Layers
- Hint 1: Start by looking at the
join_tokenattestor source code in the SPIRE repo. It’s the simplest example. - Hint 2: Use the SPIRE plugin SDK in Go. It handles the boilerplate for the gRPC connection.
- Hint 3: Run the Server with
log_level = "DEBUG"to see the plugin’s stdout/stderr during development.
Books That Will Help
| Topic | Book | Chapter | |——-|——|———| | OS Internals | “How Linux Works” | Ch. 3 (Devices) | | Plugin Design | “Solving the Bottom Turtle” | Ch. 8 | | gRPC Fundamentals | “gRPC: Up and Running” | Ch. 2 |
Project 4: Kubernetes Workload Attestation & Identity for Pods
What you’ll build: A SPIRE deployment within a Kubernetes cluster, where workloads (pods) obtain their SPIFFE IDs and SVIDs using Kubernetes-native workload attestation.
Real World Outcome
Every Pod in your cluster will have a “Digital Passport” automatically. If you move a Pod from namespace A to B, its identity changes automatically, and its permissions change with it.
Example Output:
# 1. Check Pod SVID using the SPIRE Agent's tool
$ kubectl exec my-pod -- /opt/spire/bin/spire-agent api fetch x509
ID: spiffe://example.org/ns/default/sa/my-service-account
Selectors:
k8s:ns:default
k8s:sa:my-service-account
k8s:pod-name:my-pod-6f9...
# 2. Inspect the certificate (X.509-SVID)
$ kubectl exec my-pod -- openssl x509 -in /run/spire/sockets/svid.0.pem -text -noout
...
Subject Alternative Name:
URI:spiffe://example.org/ns/default/sa/my-service-account
...
# The identity is now bound to the Kubernetes Orchestration layer!
The Core Question You’re Answering
“How can we leverage the existing trust in Kubernetes (Namespaces/ServiceAccounts) to issue strong cryptographic identities without manual secret management?”
Concepts You Must Understand First
- Kubernetes Service Accounts: How K8s identifies pods.
- Admission Controllers (MutatingWebhook): How SPIRE “injects” the Unix socket and certificates into your Pods via a sidecar or volume mount.
- DaemonSets: Why the SPIRE Agent must run as a DaemonSet to serve every node.
- Projected Service Account Tokens (PSAT): The modern way to prove pod identity to the SPIRE Server.
Questions to Guide Your Design
- Should you use the Pod Name or the Service Account as the identity? Which is more stable during deployments?
- How do you prevent a Pod in namespace
evilfrom requesting an identity belonging to namespacesecure? (Look into SPIRE Registration Entries and selectors). - How do you handle “federation” if you have two Kubernetes clusters in different regions?
Thinking Exercise
Draw the flow of a Pod starting up:
- Pod is scheduled.
- SPIRE Agent detects new container.
- Agent queries Kubelet for Pod info.
- Agent sends info to SPIRE Server.
- Server verifies against K8s API. Where could an attacker intercept this?
The Interview Questions They’ll Ask
- “What is the
k8s_psatattestor and why is it more secure than the basick8sattestor?” - “How does SPIRE handle the ‘Trust Bootstrap’ for the Agent in a K8s environment?”
- “Explain how the SPIRE Agent identifies which Pod is talking to its Unix socket.”
Hints in Layers
- Hint 1: Use the
spire-tutorialsrepository’s K8s manifests as a starting point. - Hint 2: Make sure your SPIRE Agent has the necessary RBAC permissions to talk to the Kubelet API.
- Hint 3: Use the
spiffe-csi-driverto mount the socket into your pods instead of hostPath mounts for better security.
Books That Will Help
| Topic | Book | Chapter | |——-|——|———| | K8s Security | “Kubernetes Up & Running” | Ch. 15 | | Cloud-Native Identity | “Solving the Bottom Turtle” | Ch. 6 | | Container Internals | “How Linux Works” | Ch. 17 |
Project 5: JWT-SVID Authentication for Stateless APIs
What you’ll build: A stateless HTTP API service that authenticates incoming requests using JWT-SVIDs issued by SPIRE.
Real World Outcome
An API that doesn’t need a database to verify “Who is calling”. The identity is signed by the SPIRE Server and can be verified by any service using only the public key (Trust Bundle) from SPIRE.
Example Output:
# 1. Client requests a JWT from local Agent
$ spire-agent api fetch jwt -audience payment-gateway
Token: eyJhbGciOiJSUzI1NiIsImtpZCI6In...
# 2. Client calls API with the token
$ curl -H "Authorization: Bearer eyJhb..." https://api.internal/pay
# 3. Server-side log showing verification
[2025-12-27 11:00:00] INFO: Validating JWT-SVID for audience 'payment-gateway'
[2025-12-27 11:00:01] INFO: Request Authorized! Identity: spiffe://example.org/billing-app
The Core Question You’re Answering
“How do we handle identity in environments where persistent TLS connections (mTLS) aren’t possible, such as through load balancers or legacy proxies?”
Concepts You Must Understand First
- JWT (JSON Web Tokens): Header, Payload, Signature.
- JWKS (JSON Web Key Set): How the server finds the public keys to verify the signature.
- Audience (aud) Claim: Why it’s critical to prevent a token meant for “Service A” from being used on “Service B”.
Questions to Guide Your Design
- How does the API service get the SPIRE Trust Bundle (public keys)?
- Why is the
exp(expiration) claim in a JWT-SVID usually very short? - What is the difference between an X.509-SVID and a JWT-SVID in terms of performance and security?
Thinking Exercise
Compare JWT-SVID with X.509-SVID. If an attacker steals a JWT, they can “replay” it until it expires. If they steal an X.509 private key, they can impersonate the service. Which is harder to mitigate?
The Interview Questions They’ll Ask
- “Why doesn’t SPIFFE support custom claims in JWT-SVIDs?” (Answer: To maintain interoperability and minimize security risk by keeping the document “claims-neutral”).
- “How do you verify a JWT-SVID without calling the SPIRE Server on every request?”
- “What happens if a SPIRE Server’s private key is compromised? How does that affect JWT-SVIDs?”
Hints in Layers
- Hint 1: Use the
spiffe-go-toolkit’s JWT validation helper. It handles fetching the JWKS automatically. - Hint 2: Use
jwt.ioto decode your tokens and see the SPIFFE ID in thesubclaim. - Hint 3: Ensure the
audienceyou request inapi fetchmatches exactly what the server expects.
Books That Will Help
| Topic | Book | Chapter | |——-|——|———| | JWT Internals | “Serious Cryptography” | Ch. 13 | | API Security | “Design and Build Great Web APIs” | Ch. 8 | | Distributed Security | “Zero Trust Networks” | Ch. 6 |
Project 6: Policy-Based Authorization with OPA
What you’ll build: An API service that uses Open Policy Agent (OPA) to enforce fine-grained authorization policies based on SPIFFE IDs.
Real World Outcome
You decouple “Who you are” from “What you can do”. Your code only checks the SPIFFE ID; OPA decides if that ID can GET /data.
Example Output:
# 1. Start the OPA-enabled service
$ go run main.go
[INFO] Server started. Policy: allow GET if spiffe_id == 'spiffe://example.org/frontend'
# 2. Call from Authorized service
$ curl -H "X-SPIFFE-ID: spiffe://example.org/frontend" http://localhost:8080/data
{ "data": "Top secret content" }
# 3. Call from Unauthorized service
$ curl -H "X-SPIFFE-ID: spiffe://example.org/malicious-app" http://localhost:8080/data
HTTP/1.1 403 Forbidden
{ "error": "Unauthorized by OPA policy" }
The Core Question You’re Answering
“How do we move beyond simple authentication (Who are you?) to complex authorization (What are you allowed to do?) using SPIFFE IDs as the primary key?”
Concepts You Must Understand First
- Rego Policy Language: The language used by OPA to define rules.
- Identity-Aware Authorization: Why hardcoding roles into your app is a bad idea in a dynamic environment.
Thinking Exercise
Write a Rego policy that allows access only to services in the payment namespace during business hours (9 AM - 5 PM).
Books That Will Help
| Topic | Book | Chapter | |——-|——|———| | OPA & Rego | “Cloud Native Infrastructure” | Ch. 8 | | Policy as Code | “Zero Trust Networks” | Ch. 7 |
Project 7: SPIFFE Federation Across Trust Domains
What you’ll build: Two independent SPIRE deployments (e.g., prod and dev) configured to federate, allowing cross-domain trust.
Real World Outcome
A service in dev can connect via mTLS to a service in prod (if allowed). The prod server automatically trusts the dev root CA because they exchanged “Trust Bundles”.
Example Output:
# 1. Exchange bundles (Admin action)
$ spire-server bundle show -format spiffe > dev_bundle.json
$ spire-server federation create -trustDomain dev.acme.com -bundleEndpointURL http://dev-spire:8081
# 2. Client in DEV calls Service in PROD
$ curl --cert dev-svid.pem --cacert prod-bundle.pem https://prod-service.acme.com
"Hello from Production! I trust your Development identity."
The Core Question You’re Answering
“How do we scale Zero Trust identity across multiple clouds, regions, or organizational boundaries without a single, massive Root CA?”
Concepts You Must Understand First
- Trust Domain: The security boundary (e.g.,
prod.acme.com). - Bundle Exchange: How SPIRE servers share their public keys.
Books That Will Help
| Topic | Book | Chapter | |——-|——|———| | Federation Patterns | “Solving the Bottom Turtle” | Ch. 7 | | PKI Scaling | “Serious Cryptography” | Ch. 13 |
Project 8: Custom Workload Attestor Plugin
What you’ll build: A custom SPIRE Workload Attestor plugin that identifies a process based on its file hash (checksum) or a specific environment variable, rather than standard OS metadata.
Real World Outcome
You’ll be able to verify that a workload is exactly the binary you expect, preventing an attacker from replacing your app with a malicious version even if they have access to the file system.
Example Output:
# 1. Start Agent with custom attestor
$ spire-agent run
[INFO] Loaded workload attestor: file_hash_verifier
# 2. Workload calls Agent
$ ./my-app
[INFO] Requesting identity...
[AGENT LOG] Verifying hash of /usr/bin/my-app: eb82f3...
[AGENT LOG] Hash matched! Issuing SVID.
The Core Question You’re Answering
“How do we verify the integrity of the code itself as part of the identity issuance process?”
Concepts You Must Understand First
- Workload Attestation Plugins: How the Agent queries the OS for process metadata.
- Integrity Verification: Why hash-based identification is stronger than path-based identification.
Project 9: Integrating SPIFFE/SPIRE with a Secret Manager (Vault)
What you’ll build: A service that authenticates to HashiCorp Vault using its SPIFFE ID via the Vault-SPIFFE authentication method.
Real World Outcome
You eliminate the “First Secret” problem for Vault itself. Your app doesn’t need a Vault Token to talk to Vault; it uses its SVID to “log in” and get its secrets.
Example Output:
# 1. Vault configuration
$ vault write auth/spiffe/role/my-role \
allowed_spiffe_ids="spiffe://example.org/my-app" \
policies="read-db-secrets"
# 2. App authentication using its SVID
$ vault login -method=spiffe role=my-role
Success! You are now authenticated to Vault as 'my-role'.
The Core Question You’re Answering
“How do we securely bootstrap access to a secret manager without using a static master password or token?”
Project 10: Service Mesh Integration (Istio/Envoy)
What you’ll build: A Kubernetes microservices application within an Istio service mesh, where Istio is configured to use SPIRE as its Certificate Authority (CA).
Real World Outcome
Istio normally manages its own identities. You will “rip out” Istio’s internal identity and replace it with SPIRE. Now, your Service Mesh identities can be federated with non-Kubernetes workloads seamlessly.
Example Output:
# 1. Verify Envoy is using SPIRE via SDS
$ istioctl pc secret <pod-name>
NAME SERIAL NOT BEFORE NOT AFTER
default 123... 2025-12-27T14:00 2025-12-27T15:00
# Note the short 1-hour lifetime!
# 2. Verify SPIFFE ID in the cert
$ istioctl pc secret <pod-name> -o json | jq '.[0].subjectAlternativeNames'
[
"spiffe://example.org/ns/default/sa/my-service-account"
]
The Core Question You’re Answering
“How do we bridge the gap between high-level service mesh features and low-level workload identity?”
Interview Questions
- “Why use SPIRE with Istio instead of Citadel?”
- “How does SDS work in this context?”
Project 11: Agentless Workload Identity (SPIFFE Helper/Sidecar)
What you’ll build: A legacy application integrated with a “SPIFFE Helper” sidecar that fetches SVIDs and writes them to a shared disk volume for the app to consume.
Real World Outcome
You bring Zero Trust to “un-portable” legacy apps. The app just thinks it has a standard SSL certificate on disk, but that certificate is actually a SPIFFE SVID being rotated every hour by the helper.
Example Output:
# 1. Start the SPIFFE Helper sidecar
$ spiffe-helper -config helper.conf &
# 2. Helper fetches and writes certificates
[INFO] SVID fetched. Writing to /shared/certs/tls.crt
[INFO] Key fetched. Writing to /shared/certs/tls.key
# 3. Legacy app (Nginx) uses the certs
$ nginx -c /etc/nginx/nginx.conf
# Nginx is now using short-lived, rotated identities!
Project 12: Zero-Downtime Root CA Rotation
What you’ll build: A complex orchestration of rotating the Root Certificate Authority (CA) of your SPIRE trust domain without interrupting service-to-service communication.
Real World Outcome
You master the “Day 2” operations of a security platform. You’ll learn how to transition trust from an old Root key to a new one by maintaining a period where both are valid.
Project 13: Observability & Monitoring with Prometheus
What you’ll build: A monitoring dashboard that tracks SVID issuance rates, attestation failures, and Agent/Server health using Prometheus and Grafana.
Project 18: Minimal SPIFFE Workload API Client from Scratch
What you’ll build: A minimal SPIFFE Workload API client that directly interacts with the SPIRE Agent’s Unix socket using gRPC, without using pre-built libraries.
Real World Outcome
You will understand the “wire protocol” of identity. You’ll realize that the Workload API is just a standard gRPC service.
Example Output:
$ ./my-raw-client /tmp/agent.sock
[INFO] Sending FetchX509SVIDRequest...
[INFO] Received SVID for spiffe://example.org/workload/my-client
The Core Question You’re Answering
“What is actually happening at the byte level when a workload asks SPIRE for an identity?”
Interview Questions
- “How does the SPIRE Agent know which process is calling it on a Unix socket?” (Answer: Peer credentials /
ucred). - “Explain the gRPC stream used by the Workload API.”
Project Comparison Table
| Project | Difficulty | Time | Depth | Fun |
|---|---|---|---|---|
| 1. Basic SPIRE | Beginner | Weekend | Foundational | 3 |
| 2. mTLS | Intermediate | 1-2 weeks | Core | 4 |
| 4. K8s Identity | Advanced | 1-2 weeks | Cloud-Native | 5 |
| 7. Federation | Advanced | 1 week | Distributed | 4 |
| 9. Vault Int. | Intermediate | 3 days | Integration | 4 |
| 10. Service Mesh | Expert | 1 month | Ecosystem | 5 |
| 12. CA Rotation | Expert | 2 weeks | Operations | 3 |
| 18. Custom Client | Expert | 1 week | Protocol | 5 |
Recommendation
For beginners: Start with Project 1: Basic SPIRE Deployment. For Kubernetes Masters: Jump to Project 4. For Security Architects: Focus on Project 7 (Federation) and Project 10 (Service Mesh).
Final Overall Project: Zero Trust Microservices Platform
What you’ll build: A complete microservices platform on Kubernetes, using SPIRE for identity, Istio for mesh, OPA for authorization, and Vault for secrets.
Summary
This learning path covers SPIFFE and SPIRE through 20 hands-on projects, taking you from a basic hello-world to a production-grade Zero Trust architecture.