Learn Post-Quantum Cryptography: Hybrid Schemes and Side-Channel Resilience
Goal: Deeply understand the transition from classical to quantum-safe cryptography. You will master the mathematical foundations of NIST PQC standards (Lattices, Hashes), implement hybrid schemes to bridge the gap between RSA/ECC and the future, and learn the critical “dark art” of side-channel resistance. By the end, you’ll be able to build systems that remain secure even in the face of cryptanalytically relevant quantum computers (CRQCs) and physical adversaries.
Why Post-Quantum Cryptography Matters
In 1994, Peter Shor proved that a sufficiently powerful quantum computer would make the math problems underlying RSA and ECC trivial. This isn’t just a theoretical concern; it’s a looming systemic collapse of our digital trust infrastructure.
Modern security rests on the assumption that certain math problems are hard:
- RSA: Factoring large numbers is hard.
- ECC: The discrete logarithm problem is hard.
Quantum computers use Shor’s Algorithm to solve these problems in polynomial time. If a CRQC is built today, every encrypted message sent over the last 30 years could be read.
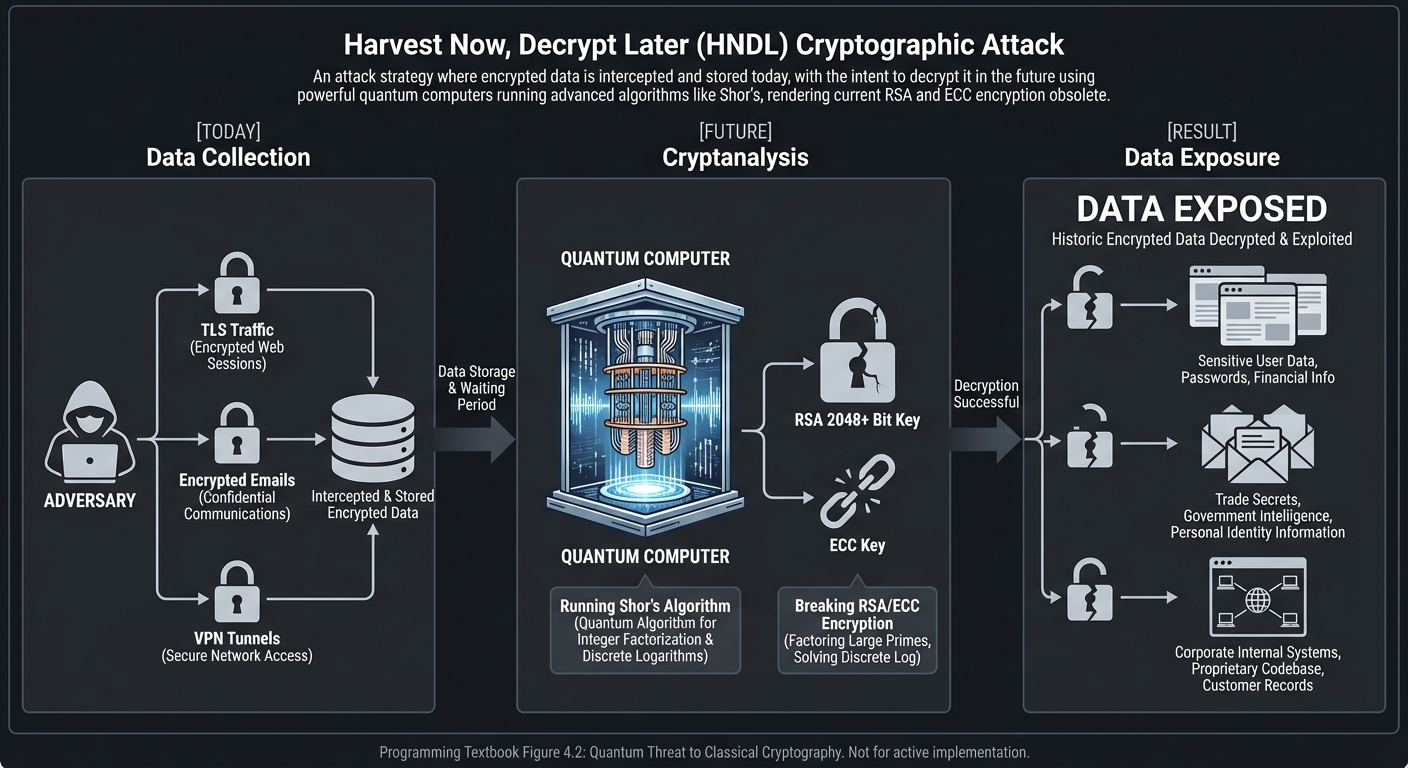
We are currently in a “Harvest Now, Decrypt Later” era. Adversaries are collecting encrypted traffic today, waiting for the quantum hardware of tomorrow to unlock it.
The Quantum Threat Visualized
Classical vs. Quantum Complexity
Problem Type | Classical Algorithm | Quantum (Shor/Grover) | Impact
-------------------|---------------------|-----------------------|-----------
Factoring (RSA) | Exponential | Polynomial (Fast) | BROKEN
Discrete Log (ECC) | Exponential | Polynomial (Fast) | BROKEN
Searching (AES) | O(N) | O(sqrt(N)) | Key Size / 2
Hashing (SHA) | O(N) | O(sqrt(N)) | Output Size / 2
The “Harvest Now, Decrypt Later” Attack
[ TODAY ] ---------------------> [ FUTURE ]
Adversary captures: Quantum Computer:
- TLS Sessions - Runs Shor's Alg
- Encrypted Emails - Breaks RSA/ECC keys
- VPN Traffic - Decrypts historical data
(Data stays secret) (Data is EXPOSED)
Core Concept Analysis
1. Lattice-Based Cryptography: The Foundation of PQC
Lattices are grids of points in high-dimensional space. The security of schemes like ML-KEM (Kyber) and ML-DSA (Dilithium) relies on the “Learning With Errors” (LWE) problem.
Imagine trying to find a secret vector s when given a set of linear equations, but each equation has a small, random “noise” added to it.
LWE Concept:
A * s + e = b (mod q)
A: Public Matrix (Known)
s: Secret Vector (Hidden)
e: Error/Noise (Hidden)
b: Result (Known)
To an observer, 'b' looks like random noise.
Without 's' or 'e', finding 's' is like finding a specific
needle in a 1000-dimensional haystack.
Why it’s Quantum-Safe: Quantum computers are great at finding periods in periodic functions (Shor’s), but they don’t have a known algorithm to “clean” the noise from LWE equations efficiently.
2. Hash-Based Signatures: The Backup Plan
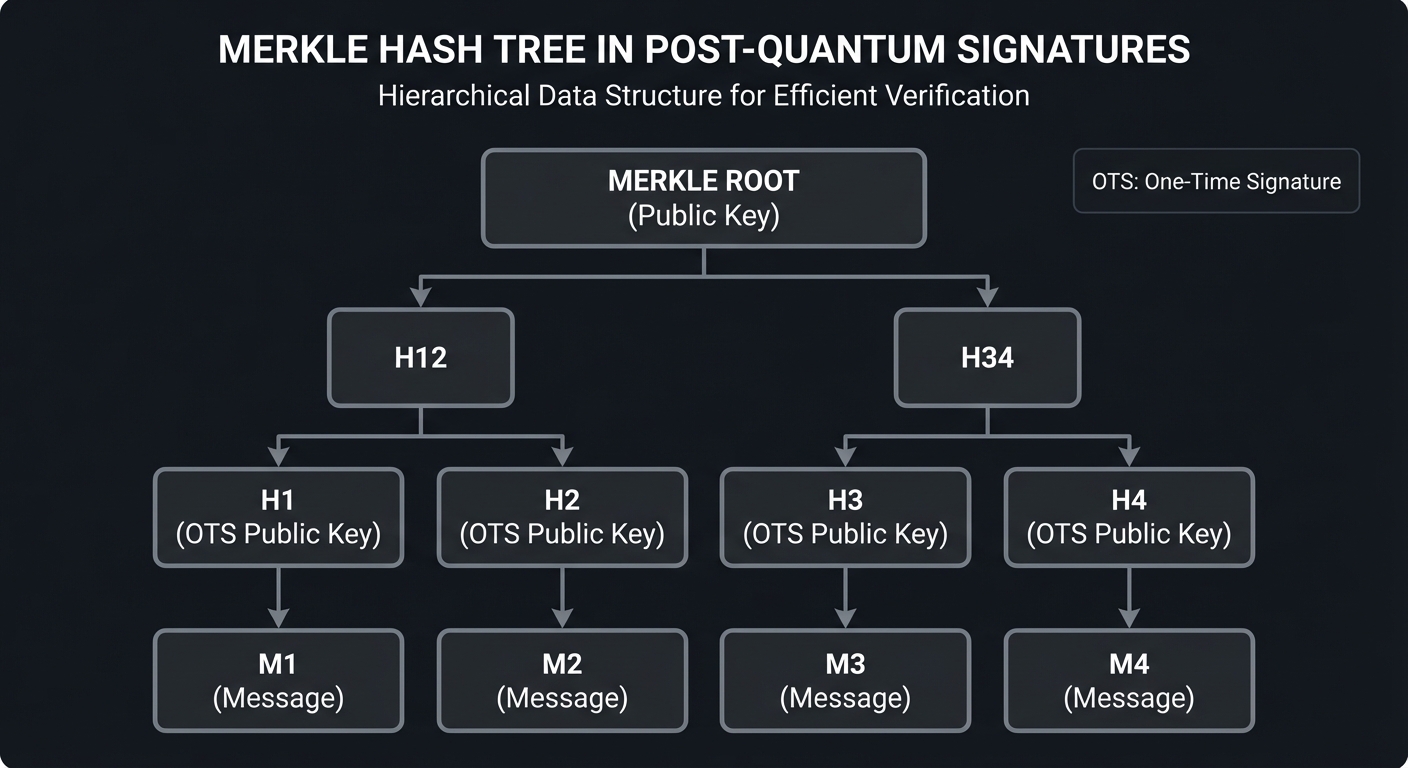
Hash-based schemes like SLH-DSA (SPHINCS+) rely only on the properties of cryptographic hash functions (like SHA-2 or SHA-3). They are “stateless,” meaning you don’t need to track which signatures you’ve already sent.
The structure is a Hypertree—a tree of trees—where each leaf ultimately derives from a series of one-time signatures.
Merkle Tree Structure (Binary Hash Tree):
[ Root ] <--- Public Key
/ \
[H12] [H34]
/ \ / \
[H1][H2][H3][H4] <--- Leaves (OTS Public Keys)
| | | |
[M1][M2][M3][M4] <--- Messages
3. Hybrid Cryptography: The Safety Net
Since PQC algorithms are relatively new, we don’t trust them completely yet. What if a flaw is found in the lattice math tomorrow? Hybrid schemes combine a classical key (like X25519) with a PQ key (like Kyber-768).
Hybrid Key Derivation (HKDF):
[ Classical Secret ] + [ PQ Secret ]
| |
+-------+-------+
V
[ HKDF Extract ]
V
[ HKDF Expand ]
V
[ Quantum-Safe Key ]

4. Side-Channel Resistance: The Implementation Attack
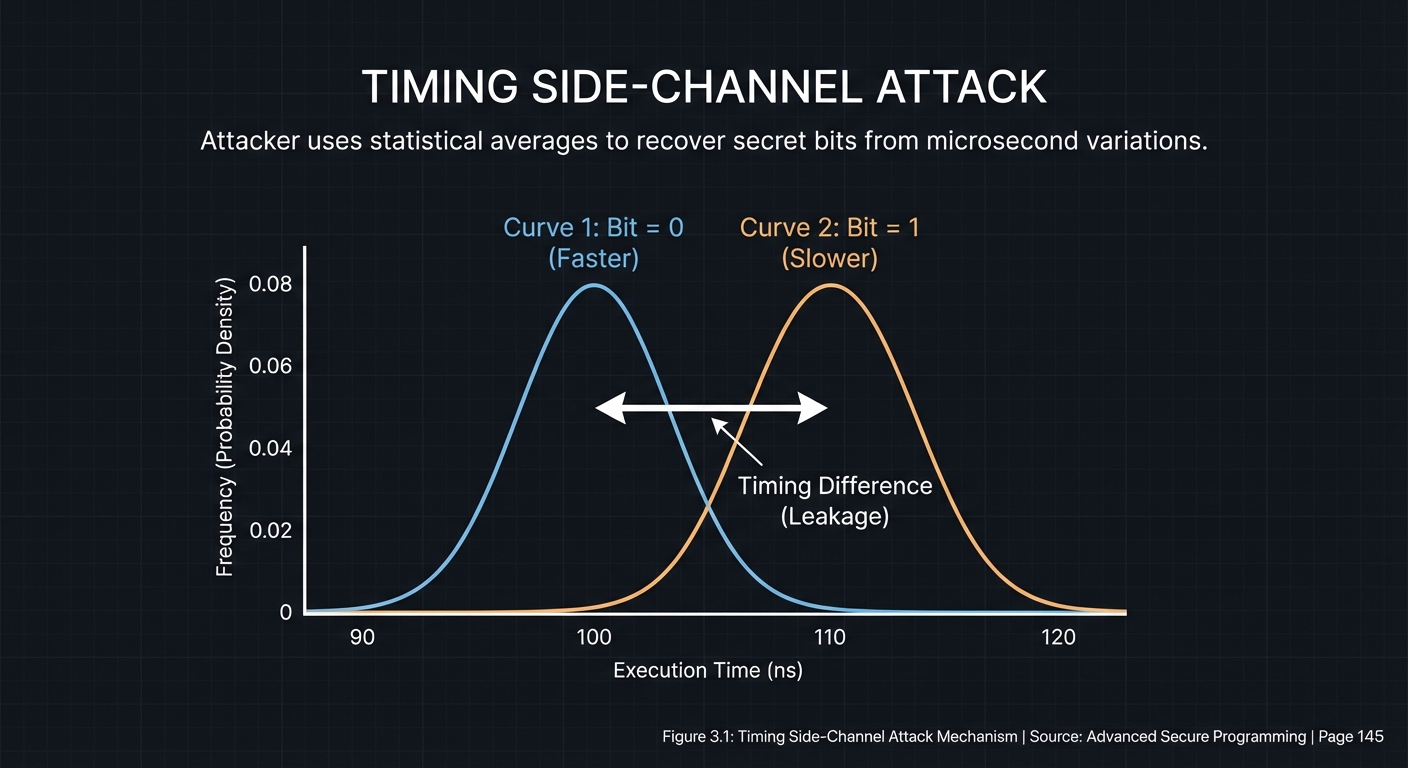
Side-channel attacks don’t attack the math; they attack the physical execution of the code. By measuring the time a CPU takes or the power it consumes, an attacker can extract the secret key.
Timing Leakage
If your code has a branch that depends on a secret bit, an attacker can measure the execution time to guess that bit.
if (secret_bit == 1) {
complex_math(); // Takes 50ms
} else {
simple_math(); // Takes 10ms
}
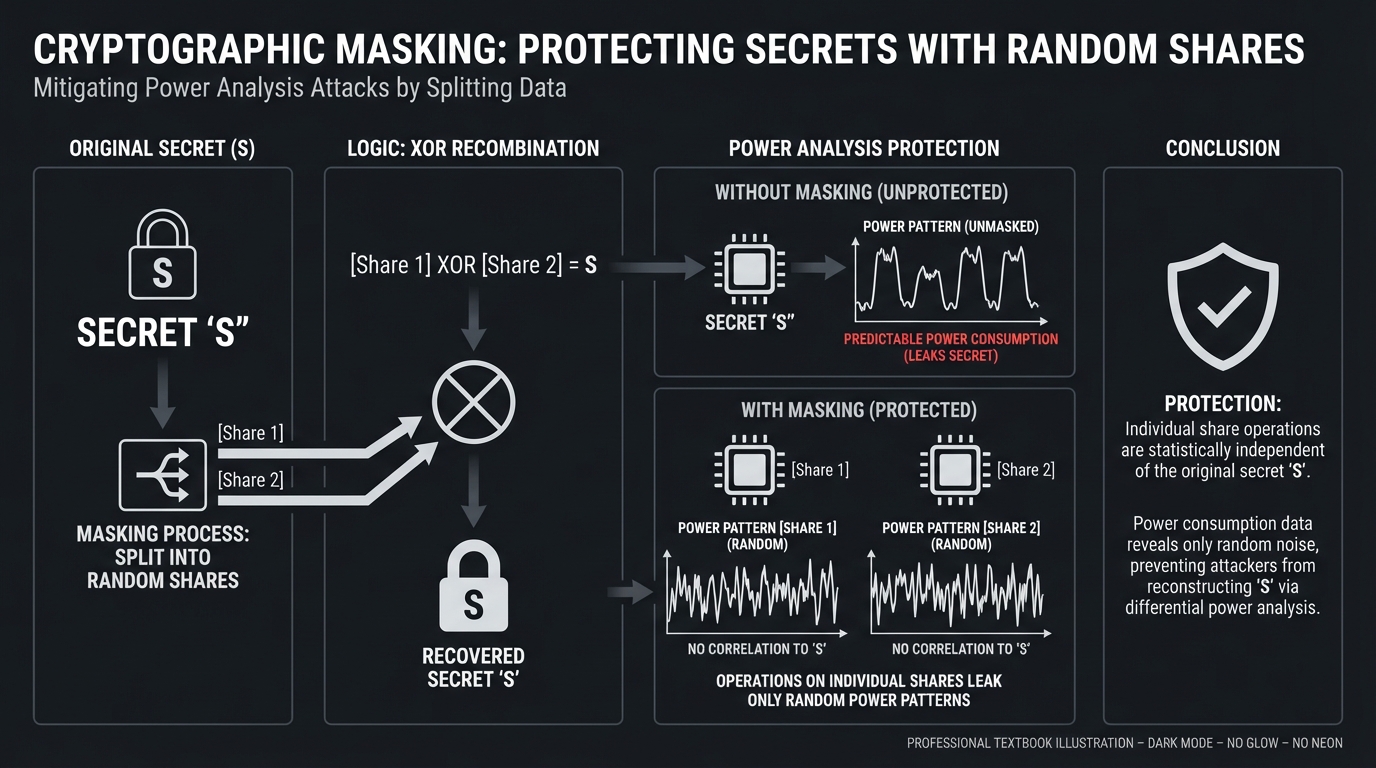
Masking (The Random Split)
Masking protects secrets by splitting them into random “shares”. You perform math on the shares, and only at the very end do you combine them back.
Secret S -> [Share 1] XOR [Share 2] = S
[Share 1] is random.
[Share 2] = S XOR [Share 1].
Operations are performed on shares separately.
Leaked power for Share 1 looks random.
Leaked power for Share 2 looks random.
5. Efficient Polynomial Math: NTT & Barrett
PQC (especially lattice-based) involves heavy polynomial multiplication. Naive multiplication is O(N²).
Number Theoretic Transform (NTT) is like a Fast Fourier Transform (FFT) for integers modulo q. It turns O(N²) multiplication into O(N log N). This is why Kyber is fast enough for real-time web traffic.
Barrett Reduction is a way to perform modular reduction (a mod q) without using the slow DIV instruction, using only multiplication and bit-shifts.
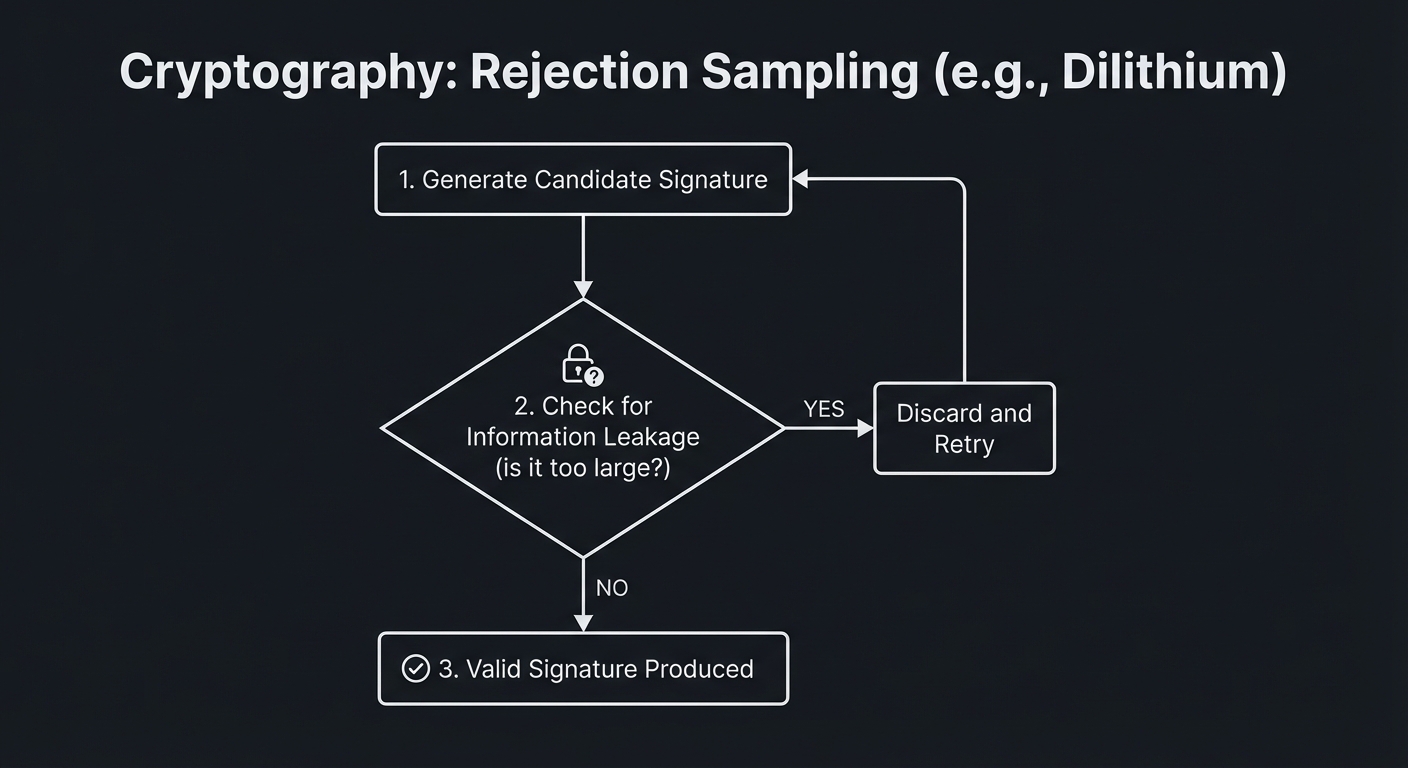
6. Rejection Sampling: Preventing Information Leakage
In PQC signature schemes like ML-DSA (Dilithium), we have to be extremely careful that the signature itself doesn’t leak the private key. Rejection sampling is a process where the signer checks the generated signature against a security bound. If it’s too “large” or “skewed”, it’s discarded and a new one is generated.
[ Generate Candidate Signature ]
|
V
[ Check for Info Leakage? (Too large?) ]
/ \
[YES] [NO]
| |
[ DISCARD & RETRY ] [ VALID SIGNATURE ]
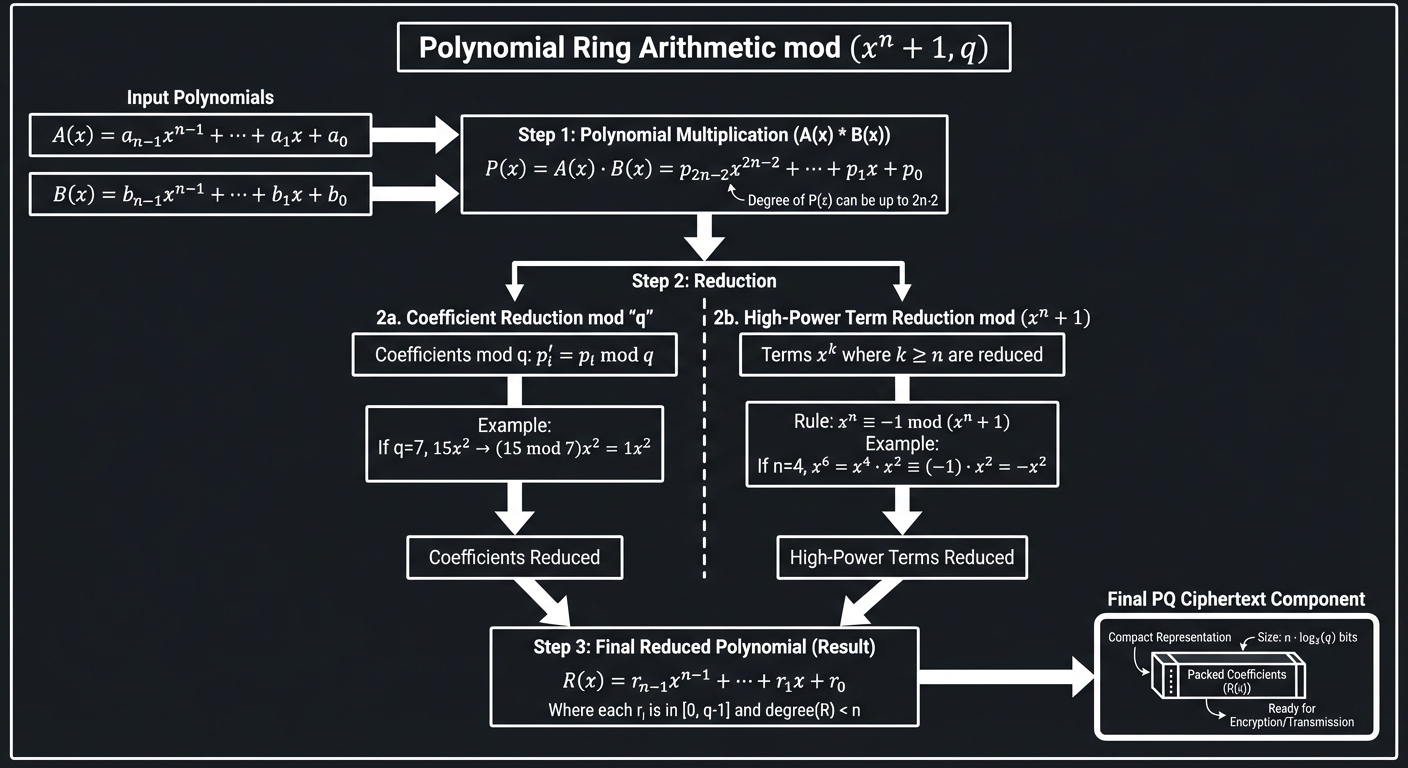
7. Polynomial Rings: The Workspace of PQC
In lattice-based cryptography, we don’t work with single numbers, but with polynomials. These polynomials live in a “Ring” defined by Z_q[x] / (x^n + 1).
This means:
- All coefficients are kept between
0andq-1. - Any power of
xequal to or greater thannis reduced (e.g.,x^nbecomes-1).
Polynomials mod (x^n + 1, q)
[ A(x) * B(x) ]
|
V
[ Result C(x) ]
|
V
[ Reduce coefficients mod q ]
[ Reduce powers mod x^n + 1 ]
|
V
[ Final PQ Ciphertext Component ]
8. PQC Networking & The Fragmentation Challenge
Transitioning to PQC isn’t just a math change; it’s a networking challenge. Classical ECC keys are ~32 bytes. Kyber ciphertexts are ~1KB. Dilithium signatures are ~2.5KB.
This “bloat” means that a single TLS handshake or VPN packet might no longer fit in the standard MTU (Maximum Transmission Unit) of 1500 bytes. This causes fragmentation, which can lead to dropped packets and failed connections on older hardware.
9. High-Assurance Systems: HSMs and Isolation
In a post-quantum world, a single private key compromise is catastrophic. We use Hardware Security Modules (HSMs) to isolate keys. The application never sees the raw key; it only sends data to the HSM and receives a signature or decapsulated secret back. This is the “Root of Trust”.
Concept Summary Table
| Concept Cluster | What You Need to Internalize |
|---|---|
| Shor’s Threat | Quantum computers solve factoring and discrete logs in poly-time. ECC/RSA are dead. |
| LWE / Lattices | Security comes from adding noise to linear equations. Hard to “clean” without the key. |
| Hybrid Protocols | Belt-and-suspenders: XOR/HKDF classical and PQ secrets to mitigate transition risk. |
| Constant-Time | Every execution path must take the same time, regardless of secret data bits. |
| Masking | Splitting secrets into shares to defeat power analysis (DPA). |
| NTT & Barrett | High-performance polynomial math required for practical lattice-based crypto. |
| Rejection Sampling | Critical in PQC signatures (Dilithium) to ensure the signature doesn’t leak the key. |
| Polynomial Rings | The “numbers” in PQC are actually polynomials. Understanding their reduction is key. |
| MTU & Frag | PQC keys are big. Handling network fragmentation is a practical necessity. |
| Isolation/HSM | Keeping keys out of application memory to prevent theft via software bugs. |
Deep Dive Reading by Concept
This section maps concepts to specific resources. Read these to build the mental models required for the projects.
Mathematical Foundations
| Concept | Book & Chapter |
|---|---|
| Shor’s Algorithm | “Quantum Computation and Quantum Information” by Nielsen & Chuang — Ch. 5 |
| Lattice Math | “An Introduction to Mathematical Cryptography” by Hoffstein et al. — Ch. 7 |
| LWE Problem | “A Decade of Lattice Cryptography” by Chris Peikert — Sections 1-4 |
| Modular Arithmetic | “Serious Cryptography” by Jean-Philippe Aumasson — Ch. 9 |
| Polynomial Rings | “Post-Quantum Cryptography” by Bernstein et al. — Ch. 2 (Lattice-based) |
NIST Standards (The “Big Three”)
| Concept | Standard |
|---|---|
| ML-KEM (Kyber) | FIPS 203: “Module-Lattice-Based Key-Encapsulation Mechanism Standard” |
| ML-DSA (Dilithium) | FIPS 204: “Module-Lattice-Based Digital Signature Standard” |
| SLH-DSA (SPHINCS+) | FIPS 205: “Stateless Hash-Based Digital Signature Standard” |
Implementation & Side-Channels
| Concept | Book & Chapter |
|---|---|
| Side-Channel Basics | “Cryptography Engineering” by Ferguson et al. — Ch. 19 |
| Timing Attacks | “The Art of Software Security Assessment” by Dowd et al. — Ch. 7 |
| Constant-Time Code | “Effective C” by Robert Seacord — Ch. 2 & Ch. 12 |
| Secure Coding | “Serious Cryptography” by Aumasson — Ch. 11 |
| Rejection Sampling | “Modern Cryptography: Theory and Practice” by Wenbo Mao — Ch. 15 |
Networking & Systems
| Concept | Book & Chapter |
|---|---|
| TCP/IP & MTU | “TCP/IP Illustrated, Volume 1” by Fall & Stevens — Ch. 11 (UDP) & Ch. 12 (IP) |
| Hardware Isolation | “Security Engineering” by Ross Anderson — Ch. 16 (Hardware Security) |
| Linux IPC (Sockets) | “The Linux Programming Interface” by Michael Kerrisk — Ch. 57 (Unix Domain Sockets) |
| Supply Chain Security | “The Practical Guide to Supply Chain Security” by Vickie Li — Ch. 2 |
Project 1: The Shor’s Simulator (Factoring with Qubits)
- Main Programming Language: Python (with Qiskit)
- Alternative Programming Languages: Julia, C++ (Microsoft Q#)
- Coolness Level: Level 5: Pure Magic
- Business Potential: 1. The “Resume Gold”
- Difficulty: Level 4: Expert
- Knowledge Area: Quantum Computation / Number Theory
- Software or Tool: IBM Qiskit
- Main Book: “Quantum Computation and Quantum Information” by Nielsen & Chuang
What you’ll build: A quantum circuit simulator that factors small integers (like 15 or 21) using Shor’s Algorithm, specifically focusing on the Period Finding step.
Why it teaches PQC: You cannot respect the solution (PQC) until you fear the problem (Shor’s). This project forces you to understand exactly how a quantum computer collapses the complexity of RSA. You’ll see how interference patterns in a Quantum Fourier Transform (QFT) reveal the secret period of a modular function.
Core challenges you’ll face:
- Quantum Fourier Transform (QFT) → maps to the “engine” of Shor’s algorithm
- Modular Exponentiation as an Oracle → maps to encoding classical math into quantum gates
- Measurement Probabilities → maps to understanding the probabilistic nature of quantum output
Real World Outcome
Deliverables:
- Shor simulator for small integers
- Comparison report vs classical factoring
Validation checklist:
- Factors small composites correctly
- Results match classical algorithm
- Simulator parameters are reproducible
A Python script that constructs a multi-qubit circuit, executes it on a local simulator (Aer), and extracts the factors of a given number. You will see the circuit diagram rendered in ASCII (or Matplotlib) and a probability distribution of the measurement results.
$ python shor_sim.py --factor 15
[+] Initializing 8-qubit register (4 counting qubits, 4 work qubits)...
[+] Applying Hadamard gates to counting register...
[+] Constructing Modular Exponentiation Oracle for 7^x mod 15...
[+] Appending Inverse Quantum Fourier Transform (IQFT)...
[+] Executing on Aer Simulator (1024 shots)...
Measurement Histogram:
0000: 256 shots (0.25)
0100: 258 shots (0.25)
1000: 251 shots (0.25)
1100: 259 shots (0.25)
[!] Measured phase candidates: 0.0, 0.25, 0.5, 0.75
[!] Using phase 0.25 -> 1/4 -> Period r = 4
[!] Verifying period: 7^4 mod 15 = 2401 mod 15 = 1. [CORRECT]
[!] Computing Factors:
p = gcd(7^(4/2) - 1, 15) = gcd(48, 15) = 3
q = gcd(7^(4/2) + 1, 15) = gcd(50, 15) = 5
[SUCCESS] Factors of 15 are 3 and 5. RSA is sweating.
The Core Question You’re Answering
“How does a sequence of complex probability amplitudes translate into the physical breakdown of RSA-2048?”
Before you write any code, sit with this question. Shor’s isn’t just “fast math”; it’s using physics to find global structure in a function that classical computers can only see locally.
Concepts You Must Understand First
Stop and research these before coding:
- Superposition & Qubits
- How can a 3-qubit register represent 8 numbers simultaneously?
- Modular Periodicity
- Why does
a^x mod Nrepeat?
- Why does
- The QFT
- How does a Fourier transform find the period of a signal?
- Quantum Gates
- Understand Hadamard (H), CNOT, and Phase (U1/CPHASE).
Questions to Guide Your Design
- Register Sizing: How many qubits do you need to factor
N? (Hint: 2n+3 rule). - Oracle Construction: How do you implement
f(x) = a^x mod Nusing only CNOT and Phase gates? - Post-Processing: What happens if the measurement gives you
0? (Hint: This is the “trivial” phase, you must re-run).
Thinking Exercise
The Phase-Finding Trace
Trace 2^x mod 7 for x=0 to x=6.
2^0 = 1,2^1 = 2,2^2 = 4,2^3 = 1…- What is the period
r? - If a quantum computer puts this into a superposition of all
x, what does the QFT see? (Visualize the frequency of the repetition).
The Interview Questions They’ll Ask
- “Why is Shor’s algorithm a threat to ECC but not AES?”
- “What is the difference between a logical qubit and a physical qubit?”
- “How does the ‘Period Finding’ step relate to the Discrete Logarithm problem?”
Hints in Layers
Hint 1: The High Level Shor’s is just classical period finding but with a quantum accelerator for the hard part.
Hint 2: Using Qiskit
Use the Qiskit library. Don’t try to write the matrix multiplication yourself for the first pass.
Hint 3: The Oracle For factoring 15, the modular exponentiation circuit is well-documented. Look up the “Beauregard circuit.”
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Quantum Algs | “Quantum Computation and Quantum Information” | Ch. 5 |
| Factoring | “The Joy of Factoring” by Samuel Wagstaff | Ch. 12 |
Project 2: The Lattice Noise Playground (LWE Visualizer)
- Main Programming Language: Python (Matplotlib/NumPy)
- Alternative Programming Languages: Javascript (D3.js), C (SDL2)
- Coolness Level: Level 3: Genuinely Clever
- Business Potential: 1. The “Resume Gold”
- Difficulty: Level 2: Intermediate
- Knowledge Area: Linear Algebra / Lattices
- Software or Tool: NumPy
- Main Book: “An Introduction to Mathematical Cryptography” by Hoffstein
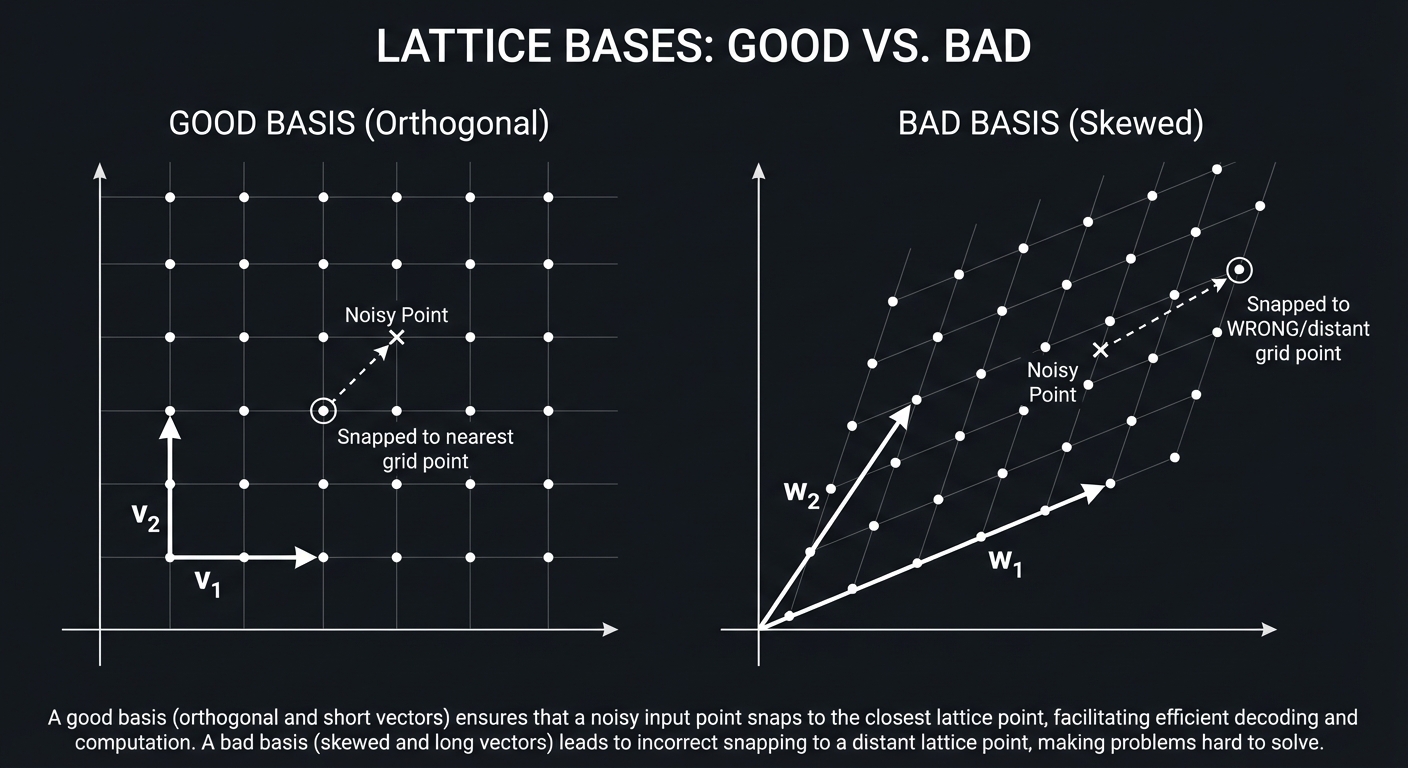
What you’ll build: A visual tool that generates a 2D lattice, adds “Learning With Errors” (LWE) noise, and shows why a “bad basis” makes it impossible to find the secret vector while a “good basis” makes it easy.
Why it teaches PQC: Most people find lattices abstract. This project makes them concrete. You’ll see how “secret keys” are just short vectors in a high-dimensional space, and “public keys” are long, skewed vectors that hide the grid’s structure.
Core challenges you’ll face:
- Basis Transformation → maps to generating public keys from private ones
- Noise Injection → maps to the ‘Errors’ in Learning With Errors
- Closest Vector Problem (CVP) → maps to the decryption process
Real World Outcome
Deliverables:
- LWE visualizer with tunable noise
- Exportable plots for hardness
Validation checklist:
- Noise-free system is solvable
- Added noise breaks solver accuracy
- Parameter changes update plots
A GUI window (via Matplotlib) showing a grid of dots.
- Left Panel: A “Good Basis” (orthogonal vectors). You click anywhere, and the program instantly snaps to the nearest lattice point (Decryption success).
- Right Panel: A “Bad Basis” (extremely long, nearly parallel vectors). You click, and the “Babai Rounding” algorithm fails to find the nearest point because the basis is too skewed (Decryption failure/Public Key security).
$ python lattice_viz.py
[+] Generating Secret Basis (Good): [[1, 0], [0, 1]]
[+] Generating Public Basis (Bad): [[101, 100], [100, 99]]
[+] Visualizing... Click on the plot to simulate a 'noisy' ciphertext.
The Core Question You’re Answering
“Why does adding a tiny bit of noise to a linear equation make it unsolvable for a quantum computer?”
Before you write any code, sit with this question. A quantum computer can solve linear equations perfectly (Gaussian elimination). But add a tiny, random +/- 1 to each equation, and suddenly it’s one of the hardest problems in mathematics.
Concepts You Must Understand First
- Basis Vectors: What does it mean for two vectors to “span” a lattice?
- Determinant of a Lattice: Why does the volume of the fundamental cell matter?
- The Babai Rounding Technique: How do you find the nearest point if your basis is “good”?
- Unimodular Matrices: How do you change a basis without changing the lattice itself?
Questions to Guide Your Design
- How do you generate a “bad” basis (long, nearly parallel vectors) from a “good” one?
- How much noise is “too much”? (When does the noise cross the Voronoi boundary?)
- Why does the “Bad Basis” fail to find the nearest point even though it describes the same set of points?
Thinking Exercise
Draw the Grid
Draw a grid of dots on paper. Choose a point not on a dot.
- If the dots are 1cm apart, and you are 0.1cm from a dot, it’s easy to see which dot you belong to.
- What if the dots are 1000-dimensional and you don’t know the grid’s orientation?
The Interview Questions They’ll Ask
- “What is the Shortest Vector Problem (SVP)?”
- “How does Module-LWE differ from standard LWE?”
- “Why are lattice problems considered quantum-resistant?”
Hints in Layers
Hint 1: Matrix Math
A lattice is just the set of all integer linear combinations of a basis. L = { B * x | x in Z^n }.
Hint 2: Good vs Bad A “good” basis is near-orthogonal. A “bad” basis is highly skewed. Use a unimodular matrix (determinant +/- 1) to transform a good basis into a bad one.
Hint 3: Closest Vector
To find the closest vector with basis B and point p: B * round(inv(B) * p). Try this with a skewed B and see it fail.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Lattice Math | “An Introduction to Mathematical Cryptography” | Ch. 7 |
| Complexity | “Lattices and Cryptography” by Daniele Micciancio | Ch. 1-2 |
Project 3: The Lattice KEM (A Toy Kyber)
- Main Programming Language: Python (NumPy)
- Alternative Programming Languages: C (for speed), Rust (for safety)
- Coolness Level: Level 4: Hardcore Tech Flex
- Business Potential: 1. The “Resume Gold”
- Difficulty: Level 3: Advanced
- Knowledge Area: LWE / Polynomial Arithmetic
- Software or Tool: NumPy
- Main Book: “Post-Quantum Cryptography” by Daniel J. Bernstein
What you’ll build: A simplified Key Encapsulation Mechanism (KEM) based on the Learning With Errors (LWE) problem. You’ll implement the three core functions: KeyGen, Encapsulate, and Decapsulate.
Why it teaches PQC: This is the heart of the NIST transition. By building a toy version of Kyber, you’ll understand why keys are represented as matrices of polynomials and how “decryption” is actually a process of error correction.
Core challenges you’ll face:
- Polynomial Multiplications mod (x^n + 1, q) → maps to the fundamental math of Ring-LWE
- Noise Sampling (Gaussian/Binomial) → maps to security through entropy
- Reconciliation/Rounding → maps to removing noise during decryption
Real World Outcome
Deliverables:
- Toy Kyber-style KEM implementation
- Keygen/encap/decap CLI
Validation checklist:
- Shared secrets match on success
- Incorrect ciphertext fails decap
- Parameters enforce modulo bounds
A library script that can generate a 1KB public key, produce a ciphertext, and recover a 256-bit shared secret. You will see the “raw” noisy polynomial before and after the reconciliation step.

$ python toy_kyber.py
[*] Generating Keypair...
[GEN] Public Key Size: 800 bytes
[GEN] Private Key Size: 768 bytes
[*] Alice encapsulates secret 'S' for Bob...
[ENC] Shared Secret: e3b0c442...
[ENC] Ciphertext (u, v) generated. Size: 1024 bytes
[*] Bob decapsulates ciphertext...
[DEC] Raw poly result (noisy): [1660, 21, 1670, 3320, ...]
[DEC] Reconciliation (Rounding): [1, 0, 1, 0, ...]
[DEC] Recovered Secret: e3b0c442...
[SUCCESS] Secrets match! Quantum-safe key exchange complete.
The Core Question You’re Answering
“How can we share a secret by sending ‘noisy’ math problems that only one person knows how to clean up?”
In classical RSA, we hide secrets behind the difficulty of factoring. In Kyber, we hide secrets in the “noise”. If you don’t have the private key, the ciphertext just looks like a bunch of random numbers.
Concepts You Must Understand First
- Polynomial Rings: What is
Z_q[x] / (x^n + 1)? - Error Distributions: Why do we use Centered Binomial Distributions instead of Uniform noise?
- Compression: How does Kyber reduce the size of its public keys?
- Number Theoretic Transform (NTT): Why is it needed for speed?
Questions to Guide Your Design
- How do you implement the polynomial reduction
x^n = -1? - What is the probability of decryption failure if your noise is too high?
- Why do we encode the message into the most significant bits of the polynomial?
Thinking Exercise
The Noise Floor
If q = 3329 and your noise is between -2 and +2.
- You add your message bit (0 or 1) by adding
round(q/2) * bit(i.e., add 1664 for bit 1). - If Bob receives
1660, is it a 0 or a 1? (Hint: 1660 is closer to 1664 than to 0). - At what point does the noise become so large that Bob guesses wrong?
The Interview Questions They’ll Ask
- “What is the difference between Ring-LWE and Module-LWE?”
- “Why does Kyber use a specific value for q (3329)?”
- “What happens if decapsulation fails? Does it leak information?”
Hints in Layers
Hint 1: Polynomials as Arrays
Represent polynomials as NumPy arrays of length n.
Hint 2: Modular Arithmetic
Remember to apply % q after every operation. For the polynomial reduction, any x^i where i >= n becomes -x^(i-n).
Hint 3: Kyber Parameters
Start with n=256, q=3329. These are the “Kyber” magic numbers.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Kyber Internals | NIST FIPS 203 | Full Doc |
| Poly Math | “The Joy of Hashing” | Ch. 8 (for Polynomials) |
Project 4: The Hybrid Bridge (ECDH + Kyber)
- Main Programming Language: Python
- Alternative Programming Languages: Go, Rust
- Coolness Level: Level 3: Genuinely Clever
- Business Potential: 2. Micro-SaaS
- Difficulty: Level 3: Advanced
- Knowledge Area: Protocol Design / Key Derivation
- Software or Tool:
cryptographylibrary + your Project 3 code - Main Book: “Serious Cryptography” by Aumasson
What you’ll build: A tool that performs a dual key exchange. It generates an X25519 (classical) secret and a Kyber (PQ) secret, then blends them together using HKDF to create a single session key.
Why it teaches PQC: This project is about risk management. You’ll learn how the industry is actually deploying PQC today (e.g., in Chrome and Cloudflare). It teaches you that “new” isn’t always “better” and that layering defenses is the hallmark of professional engineering.
Core challenges you’ll face:
- Secret Blending → maps to preventing one key from weakening the other
- Protocol Handshaking → maps to serializing multiple keys over one wire
- Backward Compatibility → maps to how to fall back if one side doesn’t support PQC
Real World Outcome
Deliverables:
- Hybrid ECDH+Kyber key derivation
- Transcript log with component secrets
Validation checklist:
- Hybrid secret changes if either component changes
- HKDF inputs are ordered consistently
- Both sides derive identical keys
A functional client/server script that establishes a shared 256-bit AES key. If you disable the Kyber part, the connection still works (but is only classically secure). If you disable X25519, it still works (quantum-safe but unproven). Together, they are “Hybrid”.
$ python hybrid_server.py --port 4444 &
$ python hybrid_client.py --host localhost --port 4444
[+] Local: Generating X25519 Ephemeral Key
[+] Local: Generating Kyber-768 Ephemeral Key
[+] Sending Hybrid Key Exchange (X25519_PK || Kyber_CT)...
[+] Received Server Response.
[+] Computing Blended Secret:
X25519 Secret: 3c2a...
Kyber Secret: f1a9...
IKM = X25519_Sec || Kyber_Sec
[+] Deriving Session Key via HKDF-SHA256...
[+] FINAL SESSION KEY: 9e21... (32 bytes)
[SUCCESS] Quantum-Safe Secure Channel Established.
The Core Question You’re Answering
“How do we deploy unproven math without risking our current security?”
Before you trust a lattice-based algorithm with your life’s secrets, you want to be sure that if a flaw is found in the lattice math, your old ECC security is still there to catch you.
Concepts You Must Understand First
- HKDF (HMAC-based Key Derivation Function): Why do we “Extract” and then “Expand”?
- X25519: The industry standard for classical key exchange.
- Entropy Pooling: Why is
K_final = Hash(K1 || K2)safer thanK1 ^ K2?
Questions to Guide Your Design
- If the Kyber implementation has a back door, does the hybrid key still protect the session from a classical attacker?
- How do you handle different key lengths?
- What happens if the
X25519secret is all zeros? Does HKDF handle it?
Thinking Exercise
The XOR Trap
Imagine K1 is random and K2 is a constant 0x00.
- If you XOR them,
K_finalis random. - What if
K2isK1 ^ 0xDEADBEEF? - How does HKDF prevent an attacker from manipulating one component to cancel out the other? (Hint: HMAC properties).
The Interview Questions They’ll Ask
- “What is a ‘combiner’ in hybrid cryptography?”
- “Why use HKDF instead of just concatenating and hashing?”
- “Which NIST standard covers hybrid key exchange?”
Hints in Layers
Hint 1: The Library
Use the Python cryptography library for X25519 and HKDF.
Hint 2: The Concatenation
The standard way is to concatenate the two secrets: IKM = Secret_Classical || Secret_PQ.
Hint 3: Salt and Info Use a fixed “Salt” and a descriptive “Info” string (e.g., “Hybrid-X25519-Kyber-v1”) in your HKDF Expand step.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Key Agreement | “Serious Cryptography” | Ch. 10 |
| Protocol Design | “Cryptography Engineering” | Ch. 15 |
Project 5: The Timing Attack (Cracking Naive LWE)
- Main Programming Language: Python / C
- Alternative Programming Languages: Rust
- Coolness Level: Level 4: Hardcore Tech Flex
- Business Potential: 1. The “Resume Gold”
- Difficulty: Level 4: Expert
- Knowledge Area: Side-Channel Analysis / Statistics
- Software or Tool:
time.perf_counterorRDTSC(in C) - Main Book: “The Art of Software Security Assessment” by Dowd
What you’ll build: A “victim” program that performs a naive LWE decryption with a timing leak, and an “attacker” script that recovers the secret key by measuring how long the victim takes to process different ciphertexts.
Why it teaches PQC: PQC algorithms are math-heavy. In naive implementations, certain operations (like modular reduction or rejection sampling) take longer for some inputs than others. This project proves that a “quantum-safe” algorithm can be broken in microseconds by a classical computer if you aren’t careful about timing.
Core challenges you’ll face:
- Identifying the Leak → maps to spotting data-dependent branches
- Statistical Filtering → maps to removing background CPU noise
- Key Recovery Logic → maps to converting timing deltas into bit guesses
Real World Outcome
Deliverables:
- Timing attack script against naive LWE
- Measurement report with recovered bits
Validation checklist:
- Timing variance is measurable
- Attack recovers partial secret on naive code
- Noise reduction improves success rate
An attacker script that recovers a 128-bit secret key from a local C program without reading its memory, just by measuring its response time to 100,000 queries.
$ ./lwe_victim &
$ python timing_attacker.py
[*] Calibrating timer... Precision: 1.2ns
[*] Starting Attack on 128 bits...
[Bit 0] Testing 10,000 samples... Avg Diff: +4.2ns -> Guess: 1
[Bit 1] Testing 10,000 samples... Avg Diff: -0.1ns -> Guess: 0
[Bit 2] Testing 10,000 samples... Avg Diff: +3.9ns -> Guess: 1
...
[Bit 127] Testing 10,000 samples... Avg Diff: -0.2ns -> Guess: 0
[!] RECOVERED KEY: 101...0
[!] ACTUAL KEY: 101...0
[SUCCESS] Key recovered in 42 seconds via timing leakage.
The Core Question You’re Answering
“If the math is secure, why does the physical execution of that math leak the secret?”
Before you write “secure” code, you must see it fail. Math exists in a vacuum; code exists in a physical CPU with branch predictors and caches.
Concepts You Must Understand First
- Branch Misprediction: How do
ifstatements affect CPU cycles? - Modular Reduction (Naive): Why is
x % qsometimes slow (ifx >> q) and sometimes fast? - Signal-to-Noise Ratio (SNR): How many samples do you need to see a 5ns difference in a system with 100ns of jitter?
- RDTSC: The x86 instruction for reading the CPU clock cycle counter.
Questions to Guide Your Design
- Where in the Kyber decapsulation process is there a conditional branch based on a decrypted bit?
- How do you disable CPU frequency scaling (Turbo Boost) to get clean measurements?
- Why does the attacker send “specially crafted” ciphertexts instead of random ones?
Thinking Exercise
The Sleepy Decoder
Imagine a function:
if (secret_bit == 1) {
for(int i=0; i<1000; i++) asm("nop");
}
- This is an obvious leak.
- Now imagine the leak is caused by
x % q. Ifxis large, the CPU performs more internal subtractions. If the attacker controlsx(via the ciphertext), they can probe the secret.
The Interview Questions They’ll Ask
- “What is a ‘Constant-Time’ implementation?”
- “How does a cache-timing attack differ from a simple timing attack?”
- “Can PQC algorithms be protected by software-only countermeasures?”
Hints in Layers
Hint 1: The Victim
Write a C function that uses a switch or if based on the private key. Compile with optimizations on to see how the compiler might introduce branches you didn’t write.
Hint 2: High Resolution
Use the RDTSC instruction in C for the highest possible timing resolution (clock cycles). In Python, use time.perf_counter_ns().
Hint 3: The Attack Iterate through the key bit by bit. For each bit, send 10,000 requests and take the average time. If the average for Bit=1 is significantly higher than Bit=0, you’ve found the leak.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Side-Channels | “Cryptography Engineering” | Ch. 19 |
| Timing Attacks | “The Art of Software Security Assessment” | Ch. 7 |
Project 6: The Defense (Constant-Time Matrix Ops)
- Main Programming Language: C
- Alternative Programming Languages: Rust, Assembly
- Coolness Level: Level 4: Hardcore Tech Flex
- Business Potential: 3. Service & Support
- Difficulty: Level 3: Advanced
- Knowledge Area: Low-Level Optimization / Secure Coding
- Software or Tool:
valgrind --tool=lackey - Main Book: “Cryptography Engineering” by Ferguson
What you’ll build: A C library for PQC matrix-vector multiplication that uses zero branches and zero secret-dependent memory lookups.
Why it teaches PQC: This is the “correct” way to implement crypto. You’ll learn to think in bit-masks instead of if statements. This project transforms you from a “coder” into a “cryptographic engineer.”
Core challenges you’ll face:
-
Bitwise Selects → maps to *replacing ‘if’ with ‘(mask & a) (~mask & b)’* - Loop Normalization → maps to making loops always run the maximum number of iterations
- Constant-Time Modular Reduction → maps to Barrett or Montgomery reduction
Real World Outcome
Deliverables:
- Constant-time LWE operations library
- Timing harness for comparison
Validation checklist:
- Timing variance is reduced vs naive
- Output matches naive implementation
- No secret-dependent branches remain
A .a static library and a test suite. When you run the test suite under a timing-leakage detector, it reports Zero Variance. You will also inspect the generated assembly to ensure the compiler didn’t “optimize” your bitwise masks back into conditional branches.
$ make test_constant_time
[+] Running 1,000,000 iterations of masked_select...
[+] Mean execution time: 12.400ns
[+] Standard Deviation: 0.002ns
[SUCCESS] No statistical correlation between input data and execution time.
$ objdump -d libpqc_secure.a | grep -E "cmov|and|or|not"
# You'll see the compiler using conditional moves and bitwise logic instead of 'jne' or 'je' branches.
The Core Question You’re Answering
“How do I perform computation on data I am not allowed to ‘look’ at?”
In secure programming, you cannot branch on secret data. If bit == 1, you cannot do_thing(). You must always do_thing() but use a mask to make its effect null if bit == 0.
Concepts You Must Understand First
- Bitwise Masks: How to implement
a = (condition) ? b : cusing only&, |, ^, ~. - Data-Independent Memory Access: Why are lookup tables (LUTs) dangerous in crypto? (Hint: Cache hits/misses).
- Barrett Reduction: How to calculate
x % qusing only multiplications and shifts. - Compiler Barriers: How to stop
gccfrom “fixing” your secure code.
Questions to Guide Your Design
- How do you create a mask
-1(all 1s) from a boolean1without using anif? - Why is
volatilesometimes necessary when dealing with secret-dependent variables? - How do you implement a constant-time “swap” of two arrays?
Thinking Exercise
The Branchless Choice
Implement this in one line of C using only bitwise operators, assuming condition is either 0 or 1:
int result = (condition == 1) ? x : y;
- Step 1: Turn
conditioninto a mask of all 1s or all 0s. - Step 2: Use
&and|to pick the result.
The Interview Questions They’ll Ask
- “What is secret-dependent branching and why is it bad?”
- “Why is Montgomery multiplication preferred in secure implementations?”
- “How does the
SELECTinstruction (e.g.,CMOV) help in writing constant-time code?”
Hints in Layers
Hint 1: The Mask
Create a mask from a boolean: int32_t mask = -(int32_t)condition; (If condition is 1, mask is 0xFFFFFFFF. If 0, it’s 0x00000000).
Hint 2: The Select
result = (mask & x) | (~mask & y);
Hint 3: Modular Reduction
Don’t use the % operator. It’s almost never constant-time on modern CPUs. Use Barrett reduction: r = a - ((a * inv_q) >> k) * q.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Secure Coding | “Serious Cryptography” | Ch. 11 |
| Low-level C | “Expert C Programming” | Ch. 8 |
Project 7: The Stateless Signer (Toy SPHINCS+)
- Main Programming Language: Python
- Alternative Programming Languages: C (OpenSSL), Go
- Coolness Level: Level 4: Hardcore Tech Flex
- Business Potential: 1. The “Resume Gold”
- Difficulty: Level 3: Advanced
- Knowledge Area: Hash-Based Signatures / Merkle Trees
- Software or Tool: SHA-256 / SHA-3
- Main Book: “Post-Quantum Cryptography” by Bernstein
What you’ll build: A simplified version of SPHINCS+. You’ll build a “Hypertree” (a tree of trees) where each leaf is a One-Time Signature (OTS) key.
Why it teaches PQC: SPHINCS+ is the “backup” for the NIST standards. If lattice math is broken, hash-based signatures will save us. This project teaches you how to turn a simple one-way function into a massive, stateless signature system.
Core challenges you’ll face:
- Winternitz OTS (WOTS+) → maps to reducing signature size by hashing multiple times
- Merkle Tree Traversal → maps to calculating authentication paths
- Statelessness via Randomness → maps to using a pseudo-random index to avoid state
Real World Outcome
Deliverables:
- Toy SPHINCS+ signer/verifier
- Stateless key derivation demo
Validation checklist:
- Valid signatures verify correctly
- Modified message fails verification
- Addressing is deterministic per seed
A command-line tool that can sign a file and produce a signature file. You will be able to verify this signature using only the public key (the Merkle Root).
$ python sphincs_tool.py --keygen --out my_key
[+] Public Key (Root): 5f31... (32 bytes)
$ python sphincs_tool.py --sign my_firmware.bin --key my_key.priv --out sig.dat
[+] Selected Leaf Index: 142,551 (via PRF)
[+] Computing WOTS+ chains...
[+] Computing Merkle Path...
[SUCCESS] Signature size: 8.4 KB
$ python sphincs_tool.py --verify my_firmware.bin --sig sig.dat --pubkey my_key.pub
[+] Verifying WOTS+... OK
[+] Verifying Merkle Path to Root... OK
[SUCCESS] Signature is VALID.
The Core Question You’re Answering
“How can we prove who we are using nothing but a bunch of hashes?”
Most crypto relies on “hard” math problems like LWE or Factoring. SPHINCS+ relies only on the existence of “one-way functions” (hashes). If SHA-3 is secure, SPHINCS+ is secure.
Concepts You Must Understand First
- One-Time Signatures (OTS): Why can you only sign one message with a Lamport key? (Hint: Reusing a key leaks bits of the private key).
- Winternitz chains: How do you sign a 4-bit value with a single hash chain?
- Hypertree: Why not just use one giant Merkle tree? (Hint: You can’t compute a tree with 2^64 leaves, but you can compute 8 layers of trees with 2^8 leaves each).
Questions to Guide Your Design
- How do you prevent two different messages from picking the same “random” leaf index? (Look up the FORS algorithm).
- What is the impact of the “Winternitz parameter” (w) on signature size vs. signing speed?
- How do you represent a Merkle Path in binary format?
Thinking Exercise
The Hash Chain
Imagine a private key x. The public key is H(H(H(H(x)))) (4 hashes).
- How do you sign the number
2? (Answer: RevealH(H(x))). - How does the verifier check it? (Answer: Hash the signature twice and see if it matches the public key).
- If an attacker sees the signature for
2, can they forge a signature for3?
The Interview Questions They’ll Ask
- “Why is SPHINCS+ called ‘stateless’ compared to LMS or XMSS?”
- “What are the trade-offs of SPHINCS+ vs. Dilithium (ML-DSA)?”
- “What is a ‘few-time’ signature scheme (FORS) and why is it used in SPHINCS+?”
Hints in Layers
Hint 1: Start Small First, implement a Lamport signature (sign 1 bit). Then upgrade it to WOTS+ (sign 4-8 bits per hash chain).
Hint 2: The Tree
Use a binary tree where Node = Hash(LeftChild || RightChild). The Merkle Path for a leaf is the set of “sibling” nodes needed to recompute the root.
Hint 3: SPHINCS+ Logic The message hash determines which leaf OTS is used. SPHINCS+ uses a pseudo-random function (PRF) to pick the leaf based on the message, so the same message always uses the same leaf.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Hash Signatures | “Serious Cryptography” | Ch. 11 |
| Merkle Trees | “Mastering Bitcoin” by Andreas Antonopoulos | Ch. 7 |
Project 8: The PQ-Safe File System (Encryption at Rest)
- Main Programming Language: Python / Rust
- Alternative Programming Languages: C++ (with FUSE)
- Coolness Level: Level 3: Practical but Forgettable
- Business Potential: 2. Micro-SaaS
- Difficulty: Level 3: Advanced
- Knowledge Area: Storage / Cryptographic File Systems
- Software or Tool: AES-256 + Kyber
- Main Book: “Designing Data-Intensive Applications” by Kleppmann
What you’ll build: A virtual vault where files are encrypted using AES-256, but the AES key itself is “wrapped” using a PQC KEM (Kyber). Each file gets its own unique, quantum-wrapped header.
Why it teaches PQC: Most PQC focus is on “data in transit” (TLS). This focuses on “data at rest.” You’ll learn how to manage long-term PQC keys and how to handle the “metadata” overhead of PQC (large public keys/ciphertexts).
Core challenges you’ll face:
- Header Design → maps to storing PQC ciphertexts alongside data
- Key Rotation → maps to re-wrapping AES keys without re-encrypting the file
- Performance Overhead → maps to caching decapsulated keys
Real World Outcome
Deliverables:
- PQ-safe file encryption tool
- Encrypted metadata + integrity tags
Validation checklist:
- Files decrypt to original hashes
- Tampered ciphertext is rejected
- Key rotation preserves access
A “vault” utility that converts any directory into a quantum-encrypted archive. Each file is individually encrypted so that you can retrieve a specific file without decrypting the whole archive.
$ pq-vault protect ./personal_docs --recipient bob_pqc.pub
[+] Scanning 12 files...
[+] Encrypting 'tax_return.pdf' (AES-GCM + Kyber-1024)...
[+] Encrypting 'passwords.txt' (AES-GCM + Kyber-1024)...
[SUCCESS] Vault created: ./personal_docs.pqv
$ pq-vault open ./personal_docs.pqv --key my_pqc.priv --out ./restored
[+] Decapsulating master header...
[+] Decrypting files...
[SUCCESS] 12 files restored.
The Core Question You’re Answering
“How do we protect archived data for the next 50 years against the coming quantum revolution?”
Data encrypted with AES-256 today is safe from quantum computers (Grover’s algorithm only halves the security). But the key for that AES data is often shared via RSA or ECC. If an attacker has the RSA-encrypted AES key, they can unlock the data in the future.
Concepts You Must Understand First
- Key Wrapping (Envelope Encryption): Why don’t we just encrypt the whole file with Kyber? (Hint: Asymmetric crypto is 1000x slower than symmetric).
- Authenticated Encryption (AEAD): Why must you use AES-GCM or Poly1305? (Hint: Integrity matters as much as privacy).
- KEM Encapsulation: How to turn a public key into a session key.
Questions to Guide Your Design
- If you have 10,000 files, and you want to change your PQC private key, do you have to re-encrypt every byte of every file? (Hint: Use a Master Key).
- How do you store the IV (Initialization Vector) for each file?
- What happens if the header is corrupted? Can you still recover the data?
Thinking Exercise
The Header Bloat
- An AES-GCM tag is 16 bytes.
- A Kyber-768 ciphertext is 1088 bytes.
- If you encrypt a 1KB text file, your metadata is larger than your data. How do you design a system that handles many small files efficiently?
The Interview Questions They’ll Ask
- “What is the ‘envelope encryption’ pattern and why is it the industry standard?”
- “How would you implement multi-user access (different people opening the same file)?”
- “Why is Kyber-1024 preferred for data at rest over Kyber-512?”
Hints in Layers
Hint 1: The Structure
File = [Magic Bytes][KEM Ciphertext][IV][AES Ciphertext][GCM Tag].
Hint 2: The Master Key Don’t wrap every file’s key with Kyber. Wrap a Master Key with Kyber once, and then use that Master Key to wrap individual file keys with AES (KeyWrap). This saves space and time.
Hint 3: Use a Library
Use liboqs-python for the Kyber operations and cryptography.hazmat for the AES-GCM operations.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Encryption at Rest | “Designing Data-Intensive Applications” | Ch. 3 (Storage Engines) |
| AEAD | “Serious Cryptography” | Ch. 8 |
Project 9: The PQ-Secure VPN (P2P Mesh)
- Main Programming Language: Go
- Alternative Programming Languages: Rust, Python
- Coolness Level: Level 4: Hardcore Tech Flex
- Business Potential: 4. Open Core
- Difficulty: Level 5: Master
- Knowledge Area: Networking / TUN/TAP
- Software or Tool: WireGuard (conceptually) / Go-tun
- Main Book: “TCP/IP Illustrated” by Stevens
What you’ll build: A Peer-to-Peer VPN that uses Kyber for every session handshake. You’ll create a virtual network interface (TUN) and tunnel encrypted IP packets between two machines.
Why it teaches PQC: VPNs are the first line of defense for enterprises. This project teaches you how to handle PQC in a high-concurrency, low-latency environment. You’ll deal with packet fragmentation (since PQC keys are big!) and the “noise” of real networks.
Real World Outcome
Deliverables:
- PQ-secure VPN handshake demo
- P2P key exchange transcript
Validation checklist:
- Peers derive identical session keys
- Rekeying occurs on schedule
- Connection fails on auth mismatch
A functional VPN client/server where you can ping a virtual IP address. You’ll observe that while the handshake packets are large (and might be fragmented by the network), the data packets are fast and secure.
$ sudo ./pqc-vpn server --listen :12345 --key server.priv
[+] VPN Server started on 10.0.0.1
[+] Listening for PQC Handshakes...
# On Client:
$ sudo ./pqc-vpn client --connect server_ip:12345 --key client.priv
[+] TUN Interface 'utun9' created (10.0.0.2)
[+] Initiating Kyber-768 Handshake...
[+] Handshake complete (Blended Session Key: 0x55...)
[+] Tunnel established.
$ ping 10.0.0.1
PING 10.0.0.1 (10.0.0.1): 56 data bytes
64 bytes from 10.0.0.1: icmp_seq=0 ttl=64 time=1.20 ms (QUANTUM SAFE)
The Core Question You’re Answering
“How do we handle the ‘Bloat’ of PQC in real-time networking?”
Classical ECC keys are 32 bytes. Kyber ciphertexts are ~1KB. Dilithium signatures are ~2.5KB. This doesn’t fit in a single standard UDP packet (MTU 1500) once you add IP/UDP headers. You must learn to handle fragmentation gracefully.
Concepts You Must Understand First
- TUN/TAP Interfaces: How does the OS send raw IP packets to your program?
- UDP Fragmentation: What happens when a packet is larger than the MTU?
- Session Re-keying: Why must we generate a new Kyber secret every hour?
- WireGuard Protocol (High Level): How does a modern, lean VPN handle handshakes?
Questions to Guide Your Design
- If your PQC handshake packet is 3000 bytes, and the network MTU is 1500, will the OS fragment it for you? (Answer: Yes, but UDP fragmentation is unreliable).
- How do you implement a “Hello” packet that tells the server which PQC algorithms the client supports?
- How do you ensure “Forward Secrecy” in your VPN?
Thinking Exercise
The MTU Trap
- Standard MTU is 1500 bytes.
- IPv4 header = 20 bytes.
- UDP header = 8 bytes.
- If your Dilithium signature is 2420 bytes, how many fragments will it create?
- If one fragment is lost, what happens to the whole signature?
The Interview Questions They’ll Ask
- “Why is UDP preferred over TCP for VPN tunnels?”
- “How do you handle Path MTU Discovery (PMTUD) in a PQC world?”
- “What is the impact of PQC on VPN ‘Time to First Byte’ (TTFB)?”
Hints in Layers
Hint 1: The TUN Device
Use the water library in Go or pytun in Python to create the virtual interface.
Hint 2: Packet Structure
Every packet should start with a 1-byte Type (0x01 = Handshake, 0x02 = Data).
Hint 3: Fragmentation Don’t rely on IP fragmentation. Break your large handshake messages into 1KB “Chunks” at the application layer and reassemble them.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Networking | “TCP/IP Illustrated, Vol 1” | Ch. 11-12 |
| VPN Internals | “Virtual Private Networks” | Ch. 4 |
Project 10: The HSM Simulator (Protecting the Master Key)
- Main Programming Language: C / Python
- Alternative Programming Languages: Rust
- Coolness Level: Level 4: Hardcore Tech Flex
- Business Potential: 3. Service & Support
- Difficulty: Level 4: Expert
- Knowledge Area: System Isolation / PKCS#11
- Software or Tool: Unix Domain Sockets / Protected Memory
- Main Book: “Security Engineering” by Ross Anderson
What you’ll build: A separate process that acts as a “Hardware Security Module” (HSM). It holds the PQC private keys. The main application can only ask the HSM to “Sign” or “Decapsulate” via a socket—it can never see the raw private key.
Why it teaches PQC: In the real world, you never keep PQC keys in application RAM (where heartbleed-style bugs can steal them). This teaches you the “Isolation” principle of high-assurance security.
Real World Outcome
Deliverables:
- HSM simulator with sealed key storage
- Audit log of key operations
Validation checklist:
- Private keys never leave the vault
- Policy denies unauthorized access
- Audit logs are tamper-evident
Two running processes.
- Process A (The Vault): Holds a Kyber private key in locked memory. Listens on a local socket.
- Process B (The App): Receives a ciphertext from the internet. It sends the ciphertext to The Vault. The Vault decapsulates it and returns only the shared secret (or uses it to encrypt a response).
$ ./hsm_daemon --key master.priv &
[+] HSM Simulator running. Slot 0 initialized.
$ ./pqc_app --request_decapsulate 0xABC...
[+] Sending request to HSM...
[+] HSM response: Decapsulation successful. Session Key: 0x99...
[!] Security Check: App RAM contains 0x99, but NOT master.priv.
The Core Question You’re Answering
“How do we prevent a single software bug from compromising our entire quantum-safe identity?”
If your VPN server has a buffer overflow, the attacker might read its RAM. If your private keys are in that RAM, you are finished. If they are in a separate process (HSM), the attacker can only use the key, not steal it.
Concepts You Must Understand First
- PKCS#11: The standard API for talking to crypto hardware.
- Unix Domain Sockets: Fast, local process communication.
- Memory Locking (
mlock): How to prevent the OS from swapping your keys to the disk. - Privilege Separation: Why root should not run the crypto daemon.
Questions to Guide Your Design
- How do you authenticate the App to the HSM? (So random processes can’t use your keys).
- What is the overhead of a context switch for every signature?
- How do you handle “Key Wrapping” (storing the keys on disk encrypted by a password)?
Thinking Exercise
The Heartbleed Scenario
Imagine your web server has a bug that lets an attacker read any 64KB of its RAM.
- If you use a software library, the private key is in RAM.
- If you use an HSM, only the socket file descriptor is in RAM.
- How does this change the attacker’s path?
The Interview Questions They’ll Ask
- “What is a ‘Root of Trust’?”
- “Why is PKCS#11 considered a ‘noisy’ or complex API?”
- “How do you protect against a ‘side-channel’ attack on the HSM process itself?”
Hints in Layers
Hint 1: The API
Don’t invent your own protocol. Use a simplified version of the PKCS#11 C_Sign and C_Decrypt functions.
Hint 2: Unix Sockets
Use socket(AF_UNIX, SOCK_STREAM, 0). It’s much faster than TCP for local calls.
Hint 3: Memory Safety
If writing the HSM in C, use memset_s or explicit_bzero to wipe the session key from RAM after the response is sent.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Security Eng | “Security Engineering” | Ch. 16 |
| Linux IPC | “The Linux Programming Interface” | Ch. 57 |
Project 11: The PQ-Safe Code Signer (Supply Chain Security)
- Main Programming Language: Python
- Alternative Programming Languages: Go, Rust
- Coolness Level: Level 3: Genuinely Clever
- Business Potential: 1. The “Resume Gold”
- Difficulty: Level 3: Advanced
- Knowledge Area: Digital Signatures / PKI
- Software or Tool: Dilithium (ML-DSA)
- Main Book: “Serious Cryptography” by Aumasson
What you’ll build: A tool that signs software binaries using Dilithium. It generates a “manifest” file that a loader can use to verify the binary’s integrity before execution.
Why it teaches PQC: Supply chain attacks are the biggest threat to modern devops. This project teaches you how to use PQC to ensure that the “update” you just downloaded wasn’t signed by a quantum-enabled hacker.
Real World Outcome
Deliverables:
- PQ code signing toolchain
- Verification utility for releases
Validation checklist:
- Signed artifacts verify successfully
- Tampered binaries fail verification
- Signatures include build metadata
A utility that signs a .deb, .rpm, or .exe file. It outputs a .sig file. A second utility (the “Verifier”) checks the signature against a PQC public key.
$ pq-signer sign my_app.bin --key release.priv --out my_app.sig
[+] Hashing binary (SHA-3)...
[+] Signing hash with Dilithium-L5...
[SUCCESS] Signature produced (2.5KB).
$ pq-signer verify my_app.bin --sig my_app.sig --key release.pub
[+] Extracting manifest...
[+] Verifying PQC Signature...
[SUCCESS] Integrity Verified. Identity: Release-Team-2025.
The Core Question You’re Answering
“How do we trust the code we run in a world where RSA-3072 is broken?”
If your software updates are signed with RSA, a quantum computer can forge an update. You need to upgrade your “Root of Trust” to a PQC algorithm like Dilithium or SPHINCS+.
Concepts You Must Understand First
- Hashing (SHA-3): Why do we sign the hash, not the whole file?
- Dilithium (ML-DSA): The NIST-standard for PQC signatures.
- Canonicalization: How to ensure a JSON manifest always produces the same hash.
Questions to Guide Your Design
- Should the signature be “detached” (a separate file) or “embedded” (inside the binary)?
- How do you handle “Timestamping” to prove a signature was made before a key was revoked?
- Why is SHA-3 (Keccak) preferred over SHA-2 in PQC environments?
Thinking Exercise
The Metadata Attack
Imagine you sign the binary, but not the version number.
- An attacker takes a signed version 1.0 (with a known bug) and sends it to a user asking for version 2.0.
- The signature is valid!
- How do you design your “Manifest” to prevent this “Downgrade Attack”?
The Interview Questions They’ll Ask
- “Why use Dilithium instead of Kyber for code signing?”
- “What is the size difference between a Dilithium signature and an Ed25519 signature?”
- “How would you implement ‘Multi-Signature’ (where 2 out of 3 admins must sign)?”
Hints in Layers
Hint 1: The Hash
Sign the output of sha3_256(file_content).
Hint 2: The Format
Use a JSON manifest: {"filename": "app.bin", "version": "1.2", "sha3": "...", "signature": "..."}.
Hint 3: Libraries
Use oqs-python for the Dilithium calls.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| Signatures | “Serious Cryptography” | Ch. 12 |
| Supply Chain | “The Practical Guide to Supply Chain Security” | Ch. 2 |
Project 12: The Hybrid TLS Proxy (The Gateway)
- Main Programming Language: Go / Rust
- Alternative Programming Languages: Python (Twisted)
- Coolness Level: Level 5: Pure Magic
- Business Potential: 5. Industry Disruptor
- Difficulty: Level 5: Master
- Knowledge Area: Network Proxies / TLS Internals
- Software or Tool: OpenSSL 3.3 (with PQC) / Go crypto/tls
- Main Book: “Bulletproof SSL and TLS” by Ivan Ristić
What you’ll build: A “Man-in-the-Middle” proxy that upgrades incoming non-PQ connections to PQC-enabled connections for the backend.
Why it teaches PQC: This is the ultimate “real world” project. It shows how we can protect old, legacy systems by wrapping them in a PQC shell.
Real World Outcome
Deliverables:
- Hybrid TLS proxy with PQ handshake
- Compatibility report for clients
Validation checklist:
- Handshake completes with PQ + classical
- Downgrade attempts are detected
- Session keys match across proxy ends
A proxy server. You point your browser to it. It negotiates a Hybrid TLS 1.3 connection (X25519 + Kyber) with the internet, but talks standard HTTP/HTTPS to your internal, old server.
$ ./pqc_proxy --frontend :443 --backend 192.168.1.10:80
[+] Proxy listening on 443 (Hybrid TLS Enabled).
[+] Negotiated Cipher: TLS_AES_256_GCM_SHA384
[+] Key Exchange: X25519 + Kyber768
[SUCCESS] Securely tunneling traffic for legacy-web-server.
The Core Question You’re Answering
“How do we protect a trillion-dollar legacy infrastructure without rewriting every line of code?”
Most companies have thousands of servers that won’t be updated to PQC for a decade. A PQC Proxy (or Service Mesh sidecar) allows you to “encrypt the link” with quantum-safe math without touching the application code.
Concepts You Must Understand First
- TLS 1.3 Handshake: How are key shares sent in the
ClientHello? - Reverse Proxies: How to forward requests while preserving headers.
- X.509 Extensions: How to signal PQC support in certificates.
- Go
crypto/tls: How to add custom key exchange logic.
Questions to Guide Your Design
- How do you handle “Certificate Pinning” if you are a proxy?
- What happens to latency when you add 2KB to every handshake?
- How do you load-balance across multiple PQC-enabled backends?
Thinking Exercise
The Middlebox Problem
Many enterprise firewalls “break” if they see a ClientHello they don’t recognize.
- How does the “Hybrid” approach (greasing the handshake) help PQC traffic pass through old firewalls?
- Look up “TLS Greasing” (RFC 8701).
The Interview Questions They’ll Ask
- “What is a ‘Sidecar’ pattern in microservices?”
- “How do you upgrade a TLS 1.2 connection to PQC?” (Answer: You can’t easily, you need TLS 1.3).
- “What is the ‘X25519Kyber768Draft00’ group in TLS?”
Hints in Layers
Hint 1: The Language
Use Go. Its net/http/httputil.ReverseProxy makes this much easier than C.
Hint 2: The TLS Config
You’ll need a version of crypto/tls that supports PQC (like the Cloudflare fork or Go 1.24+).
Hint 3: Handshake Inspection
Use tcpdump or wireshark to see the “Key Share” extensions in the handshake. You should see two entries: one for X25519 and one for Kyber.
Books That Will Help
| Topic | Book | Chapter |
|---|---|---|
| TLS Mastery | “Bulletproof SSL and TLS” | Ch. 2-3 |
| Go Networking | “Network Programming with Go” | Ch. 8 |
Project Comparison Table
| Project | Difficulty | Time | Depth of Understanding | Fun Factor |
|---|---|---|---|---|
| 1. Shor’s Sim | Level 4 | 2 Weeks | Theoretical Foundation | 5/5 |
| 2. Lattice Visualizer | Level 2 | Weekend | Visual Intuition | 4/5 |
| 3. Toy Kyber | Level 3 | 1-2 Weeks | Algorithmic Mastery | 4/5 |
| 4. Hybrid Bridge | Level 3 | Weekend | Practical Deployment | 3/5 |
| 5. Timing Attack | Level 4 | 1-2 Weeks | Defensive Mindset | 5/5 |
| 6. Constant-Time Lib | Level 3 | 1-2 Weeks | Low-Level Engineering | 3/5 |
| 7. Stateless Signer | Level 3 | 1 Week | Hash-Based Security | 4/5 |
| 8. PQ File System | Level 3 | Weekend | Storage Principles | 3/5 |
| 9. PQ VPN | Level 5 | 1 Month | Network Architecture | 5/5 |
| 10. HSM Simulator | Level 4 | 1-2 Weeks | Systems Isolation | 4/5 |
| 11. Code Signer | Level 3 | Weekend | Supply Chain Security | 3/5 |
| 12. Hybrid TLS Proxy | Level 5 | 1 Month | Protocol Engineering | 5/5 |
Recommendation
If you are a math nerd: Start with Project 1 (Shor’s) and Project 2 (Lattice Visualizer). They will give you the “Why” and the “How” of the underlying math.
If you are a systems engineer: Start with Project 4 (Hybrid Bridge) and Project 8 (PQ File System). These are the most immediately useful in a professional environment.
If you want to be a Security Researcher: Focus on Project 5 (Timing Attack) and Project 6 (Constant-Time Lib). This is where the real vulnerabilities live.
Final Overall Project: The Quantum-Resistant Root of Trust
What you’ll build: A complete Secure Boot and Update system.
- A PQC CA (Certificate Authority) using SPHINCS+.
- A Firmware Loader that verifies Dilithium-signed updates.
- A Secure Storage area for keys protected by a Kyber-wrapped master key.
- A Hardware Simulation (Project 10) that isolates these operations.
This final project combines every concept: math, protocol design, isolation, and side-channel resistance into a single, cohesive “Secure System” that would withstand a quantum apocalypse.
Summary
This learning path covers Post-Quantum Cryptography through 12 hands-on projects. Here’s the complete list:
| # | Project Name | Main Language | Difficulty | Time Estimate |
|---|---|---|---|---|
| 1 | Shor’s Simulator | Python | Level 4 | 2 Weeks |
| 2 | Lattice Visualizer | Python | Level 2 | Weekend |
| 3 | Toy Kyber | Python | Level 3 | 1-2 Weeks |
| 4 | Hybrid Bridge | Python | Level 3 | Weekend |
| 5 | Timing Attack | C / Python | Level 4 | 1-2 Weeks |
| 6 | Constant-Time Lib | C | Level 3 | 1-2 Weeks |
| 7 | Stateless Signer | Python | Level 3 | 1 Week |
| 8 | PQ File System | Python / Rust | Level 3 | Weekend |
| 9 | PQ VPN | Go | Level 5 | 1 Month |
| 10 | HSM Simulator | C / Python | Level 4 | 1-2 Weeks |
| 11 | Code Signer | Python | Level 3 | Weekend |
| 12 | Hybrid TLS Proxy | Go / Rust | Level 5 | 1 Month |
Expected Outcomes
After completing these projects, you will:
- Understand exactly how quantum computers threaten modern life.
- Be able to implement Lattice-based and Hash-based primitives from scratch.
- Master the art of constant-time programming to prevent side-channel leaks.
- Design hybrid protocols that bridge the gap between classical and PQ eras.
- Build production-ready tools for secure communication, storage, and software distribution.
You’ve built 12 working projects that demonstrate deep understanding of PQC from first principles. Welcome to the quantum-safe future.