Ethical Hacking & Penetration Testing: Expanded Project Guides
Goal: Develop hands-on offensive security skills by building tools and lab environments that demonstrate real attack paths with safe, reproducible evidence.
This directory contains comprehensive, expanded guides for each project in the Ethical Hacking & Penetration Testing learning path. Each guide is designed to provide everything you need to complete the project while building deep understanding of offensive security concepts.
Offensive Workflow and Safety
Every offensive task has a legal boundary and a safety boundary. Define scope, isolate labs, and collect evidence without causing damage.
Reconnaissance to Exploitation
Recon discovers surface area, scanning validates exposure, and exploitation demonstrates impact. Each phase should output artifacts that make the next phase precise and repeatable.
Post-Exploitation and Reporting
Access without evidence is not a result. The goal is reproducible findings, minimal persistence, and clear remediation steps.
Concept Summary Table
| Concept Cluster | What You Need to Internalize |
|---|---|
| Recon | Asset discovery and fingerprinting. |
| Exploitation | Controlled proof of impact. |
| Post-exploitation | Privilege escalation and evidence capture. |
| OpSec | Avoid collateral damage, use lab setups. |
| Reporting | Clear, actionable remediation output. |
Deep Dive Reading by Concept
| Concept | Book & Chapter |
|---|---|
| Recon & scanning | The Hacker Playbook 3 — recon chapters |
| Web exploitation | Web Application Hacker’s Handbook — SQLi/XSS |
| Post-exploitation | Penetration Testing by Weidman — post-ex chapters |
| Reporting | PTES Technical Guidelines — reporting |
Project Index
| # | Project | Difficulty | Focus Area | Status |
|---|---|---|---|---|
| 1 | Network Reconnaissance Toolkit | Beginner-Intermediate | Network Security, TCP/IP | Ready |
| 2 | Web Application Vulnerability Scanner | Intermediate | Web Security, OWASP Top 10 | Ready |
| 3 | Complete CTF Challenges | Progressive | Binary Exploitation, Forensics, RE | Ready |
| 4 | C2 (Command & Control) Framework | Intermediate-Advanced | Malware Analysis, Networking | Ready |
| 5 | Vulnerable Lab Network | Advanced | Network Security, Active Directory | Ready |
| 6 | End-to-End Penetration Test (Capstone) | Advanced | Full Methodology | Ready |
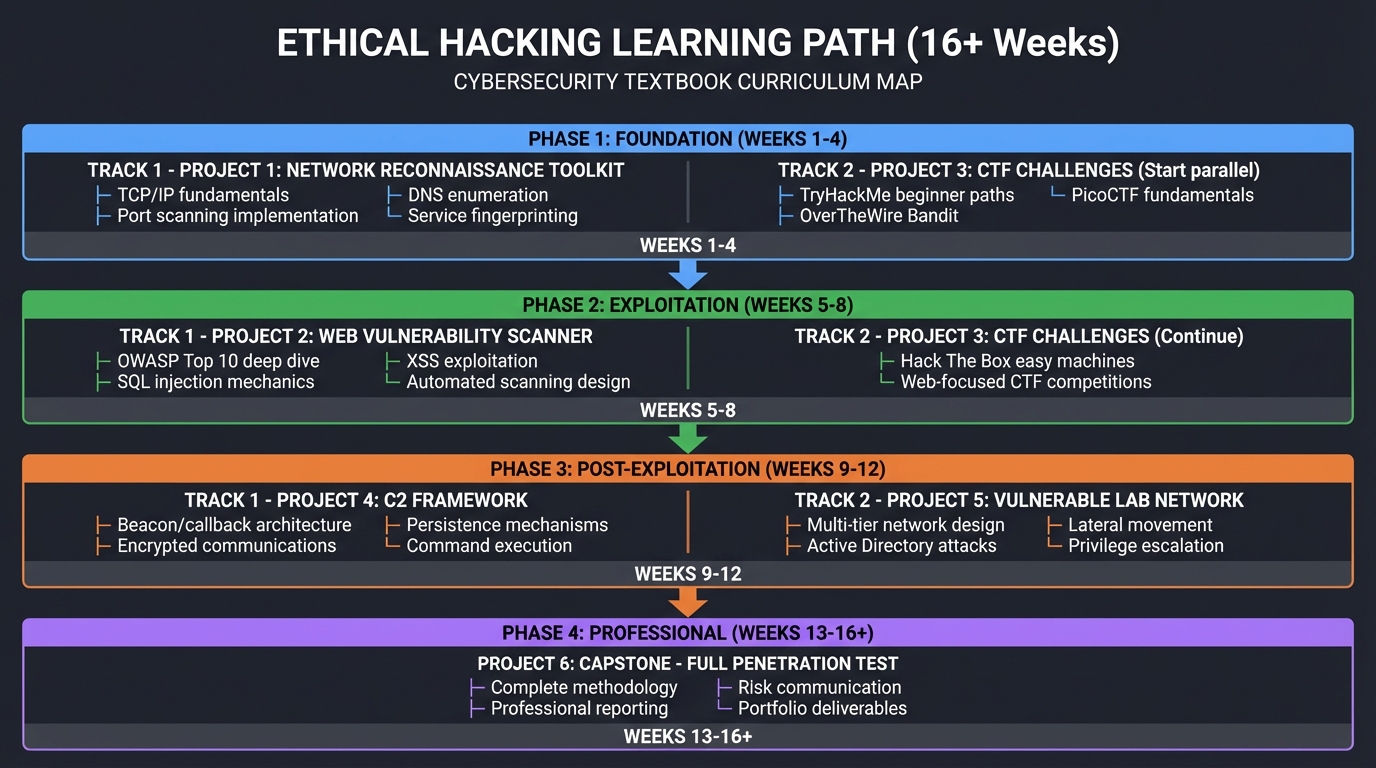
Learning Path Overview
┌─────────────────────────────────────────────────────────────────────────┐
│ ETHICAL HACKING LEARNING PATH │
└─────────────────────────────────────────────────────────────────────────┘
FOUNDATION (Weeks 1-4)
├── Project 1: Network Reconnaissance Toolkit
│ ├── TCP/IP fundamentals
│ ├── Port scanning implementation
│ ├── DNS enumeration
│ └── Service fingerprinting
│
├── Project 3: CTF Challenges (Start parallel)
│ ├── TryHackMe beginner paths
│ ├── OverTheWire Bandit
│ └── PicoCTF fundamentals
EXPLOITATION (Weeks 5-8)
├── Project 2: Web Vulnerability Scanner
│ ├── OWASP Top 10 deep dive
│ ├── SQL injection mechanics
│ ├── XSS exploitation
│ └── Automated scanning design
│
├── Project 3: CTF Challenges (Continue)
│ ├── Hack The Box easy machines
│ └── Web-focused CTF competitions
POST-EXPLOITATION (Weeks 9-12)
├── Project 4: C2 Framework
│ ├── Beacon/callback architecture
│ ├── Encrypted communications
│ ├── Persistence mechanisms
│ └── Command execution
│
├── Project 5: Vulnerable Lab Network
│ ├── Multi-tier network design
│ ├── Active Directory attacks
│ ├── Lateral movement
│ └── Privilege escalation
PROFESSIONAL (Weeks 13-16+)
└── Project 6: Capstone - Full Penetration Test
├── Complete methodology
├── Professional reporting
├── Risk communication
└── Portfolio deliverables
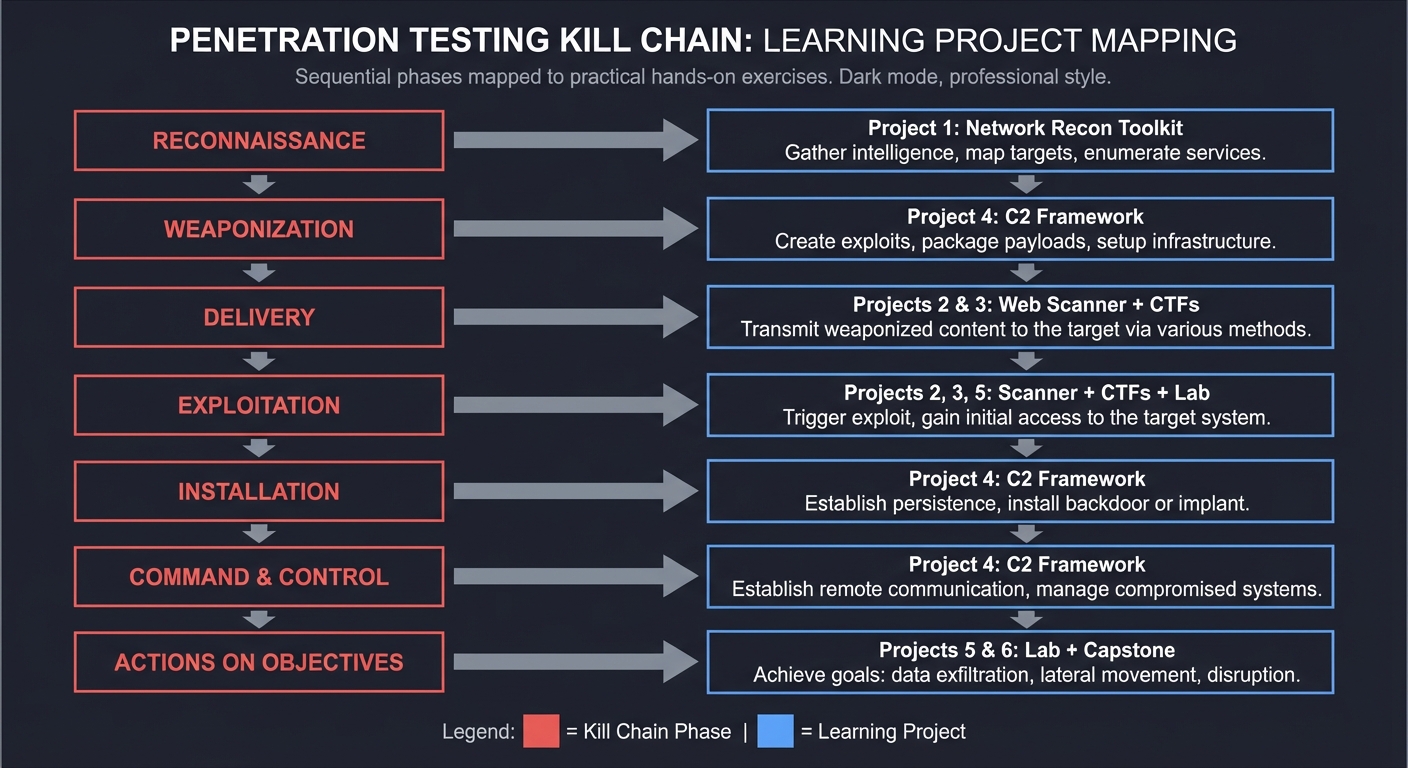
The Penetration Testing Kill Chain
Each project maps to specific phases of the Cyber Kill Chain:
RECONNAISSANCE ──────────────────────► Project 1: Network Recon Toolkit
│
▼
WEAPONIZATION ───────────────────────► Project 4: C2 Framework
│
▼
DELIVERY ────────────────────────────► Projects 2 & 3: Web Scanner + CTFs
│
▼
EXPLOITATION ────────────────────────► Projects 2, 3, 5: Scanner + CTFs + Lab
│
▼
INSTALLATION ────────────────────────► Project 4: C2 Framework
│
▼
COMMAND & CONTROL ───────────────────► Project 4: C2 Framework
│
▼
ACTIONS ON OBJECTIVES ───────────────► Projects 5 & 6: Lab + Capstone
Key Resources
Primary Books
- “Penetration Testing” by Georgia Weidman - Complete methodology reference
- “Bug Bounty Bootcamp” by Vickie Li - Web vulnerability deep dive
- “Black Hat Python” by Justin Seitz - Tool development
- “Windows Security Internals” by James Forshaw - Active Directory attacks
Practice Platforms
- TryHackMe - Guided learning
- Hack The Box - Challenge-based
- PortSwigger Academy - Web security
- VulnHub - Offline vulnerable VMs
Reference Materials
- OWASP Testing Guide
- HackTricks - Privilege escalation
- PayloadsAllTheThings
- PTES Technical Guidelines
Legal & Ethical Notice
CRITICAL: Only practice on systems you own or have explicit written permission to test.
Unauthorized access to computer systems is a federal crime (CFAA in the US, similar laws elsewhere). Safe practice options include:
- Your own VMs and home lab
- CTF platforms designed for practice
- Bug bounty programs with defined scope
- Employer-authorized security testing
Building these skills ethically makes you valuable to organizations defending against the same techniques.
Expected Outcomes
After completing all projects, you will:
- Understand attack methodology - Not just how to use tools, but why they work
- Build custom security tools - Port scanners, vulnerability scanners, C2 frameworks
- Master web application security - Complete OWASP Top 10 exploitation and defense
- Conduct professional penetration tests - Full methodology with portfolio-quality reports
- Demonstrate job-ready skills - Technical depth plus communication ability
These expanded guides are part of the Learning Journey project-based curriculum.